What Is Threat Hunting and Why Does It Matter?
Threat hunting in most cases involves searching for “unknown unknowns”—previously undetected anomalies, unusual activity, or malicious code that might open the door to a cyberattack. Threat hunters continuously look for cybersecurity threats across an organization’s networks and endpoints, including laptops, PCs, tablets, and virtual machines in the cloud. The approach proactively finds, removes, and remediates threats before hackers can burrow into your network.
Much cybersecurity work is reactive. Threat intelligence experts and providers release indicators of a breach, malware, or ransomware, and then they look for them in their network. The hope is to stop bad actors before they do too much damage.
Unfortunately, reactive cybersecurity leaves too many opportunities for attackers to infiltrate systems and wreak havoc. Fortunately, a technique known as threat hunting offers a proactive way forward.
Tanium’s Cyber Hygiene Assessment: An actionable path to better endpoint management and security
Threat hunts can be ongoing ad hoc searches for outliers within networks, or they can be scheduled and time-limited, allowing you to marshal a team with diverse areas of expertise to perform a broad search for potential threats.
How does threat hunting work?
To understand how threat hunting fits into the overall cybersecurity landscape, it helps to first understand the four types of cybersecurity threats you may face:
- Unknown unknowns. You don’t know if you have threats in your environment, and you have no indicators of potential cybersecurity threats. These are the most dangerous threats you face, because you don’t know what you don’t know.
- Known unknowns. You know a threat is possible, but you don’t know if a threat is in your environment. These are the kind of threats you’re aware of.
- Unknown knowns. An outside source has notified you that a threat exists in your environment, but you don’t want to hear about it. These are blind spots—the threats we pretend not to know about.
- Known knowns. You know what a threat looks like, and you have reliable evidence about whether it is already inside your network. You know what you know.
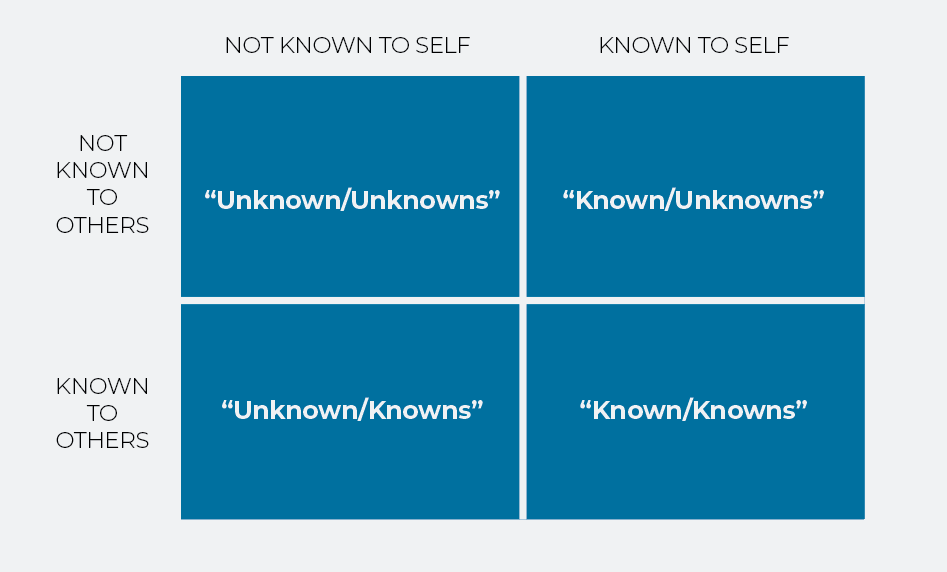
Most threat hunting falls into the “unknown unknowns” category. Threat hunting is the proactive search for unknown malicious activity in undisclosed locations.
Threat hunts require nuance and expertise. Most threat hunters have intense cybersecurity experience, and many have Department of Defense backgrounds. They are the type of people who can look at threat indicators and quickly intuit what doesn’t belong.
What steps are involved in threat hunting?
Threat hunters don’t blindly sort through mountains of data hoping to spot an anomaly. The threat hunting process revolves around clearly defined steps:
- Hypothesis generation. This is the research phase of a threat hunt. It includes reading about and researching the latest threats and developing a hypothesis that the hunt will test. These hypotheses tend to be fairly narrow. For example, if you know that attackers commonly install services remotely, you might decide to focus your search on those services.
- Data gathering. Now that you have a hypothesis, the next step is to gather and identify the data. Cybersecurity threats evolve constantly, and threat hunters need the flexibility to customize tools to fit their needs. If you’re looking for an indicator that no one has searched for before, you might need to build a new sensor to test your hypothesis. Fortunately, advanced cybersecurity tools are available to give threat hunters the ability to quickly develop the features they need to seek out novel threats.
Threat hunting requires nuance and expertise. Most hunters can look at threat indicators and quickly intuit what doesn’t belong.
- Data analysis. The next step is to review the data you have gathered to search for outliers and anomalies that could point to potential threats. Automated threat assessment tools give you the capacity to comb through massive amounts of data and delve into the indicators that warrant further review.
- Investigation. Investigation is the point in the threat hunting process where you discover whether your hypothesis is correct. Further examination of the outliers in your data will determine if they are true positives or if there is an innocent explanation for the anomalies. Even if the anomalies turn out to be part of a standard business practice in some department, they could point to flawed procedures that may inadvertently create cybersecurity vulnerabilities. Threat hunting allows you to proactively mitigate vulnerabilities before they lead to disaster. In other words, even if your hypothesis doesn’t lead you to uncover an active threat, it has the potential to unearth actionable data your organization can use to improve its cybersecurity.
- Intelligence. This optional fifth step is built around ongoing and continuous threat hunting. While it’s a best practice, it isn’t realistic for every organization because of the heavy resources it requires. But consider the benefits of the greater preparedness that comes from developing a sensor that looks for new remotely installed services. By keeping this sensor operating in real time, you can significantly enhance your endpoint security over the long term.
What are the benefits of threat hunting?
Threat hunting moves your cybersecurity from reactive damage control to proactive damage prevention. By the time a third party alerts you to a data breach, or you receive a ransom demand, the damage to your systems and the cost of remediation may be severe.
One way to think of threat hunting is that it’s like your body’s immune system. Your T cells don’t wait for you to feel bad. They constantly seek out and kill invading germs and cells that exhibit abnormal behavior. In many instances, your immune system prevents you from getting sick at all.
[Read also: How to identify and contain adversaries before they can spread across your network]
Of course, like attacks on the immune system, cyberattacks can sometimes slip through, even in organizations with robust and ongoing cybersecurity operations. However, in many of these cases, threat hunting allows you to catch cybersecurity breaches earlier, saving your company’s reputation and protecting its data.
What are the risks if you don’t proactively hunt for threats?
It’s easy to see what happens in organizations that don’t conduct proactive threat hunting. These organizations make headlines when they’re forced to report a massive data breach or ransomware attack. That’s not to say that a company with a proactive threat hunting program will never get hacked. But it’s far less likely.
What techniques are used for threat hunting?
Threat hunting requires creativity and ingenuity, so threat hunting techniques can be as diverse as the threat hunters themselves. Here are a few standard techniques that many threat hunters employ.
- Stacking. One of the characteristics that can point to malicious activity is the presence of more (or fewer) occurrences of an otherwise benign type of data. Stacking, which is also called stack counting, tabulates occurrences and identifies anomalies for in-depth review.
- Frequency. Analyzing the frequency of a certain type of network activity, such as traffic from or to a certain endpoint, can expose malicious activity.
- Volume. Volumetric analysis also often focuses on endpoints but examines the volume of data sent outside the network or other anomalous characteristics related to quantity.
- Clustering. The clustering threat hunting technique starts by cataloging the common features of a network. From there, companies use statistical analysis to detect anomalies within those features. For example, if an otherwise normal type of behavior follows an unusual pattern, it may indicate a threat.
- Grouping. Grouping is a refinement of clustering with an emphasis on a subset of network features. If you have identified potentially malicious behavior, you can use grouping to better focus your hunt on areas with concentrated levels of suspicious activity.
These threat hunting techniques rely on automation to review and analyze large volumes of data. While threats have multiplied exponentially in the current environment, AI and machine learning tools enable threat hunters to sense and respond at scale.
What are the best practices of threat hunting?
Employing best practices increases your chance of success at threat hunting. First, start with research. If you plan a weeklong hunt, spend the first two or three days researching the correct artifacts and the proper data you will need to collect. This provides a solid foundation for the hunt so you aren’t simply casting around in the dark.
Next, assemble a team with the proper skill sets. Ideally, your team should include people with forensic skills to determine root causes, data analysis capabilities to pinpoint anomalies, and theoretical brainpower that can generate the threat hypotheses you will use to organize the hunt.
Just as important, your team needs members who bring different perspectives to the hunt. Seasoned professionals who have experience with a variety of threats are essential to threat hunting. But it’s also a best practice to include someone who has recently joined the company, perhaps a team member who is newly out of college. A fresh set of eyes with no preconceived notions has tremendous value in detecting novel types of threats.Threat hunting is like your immune system. T cells don’t wait for you to feel bad. They constantly seek out germs.
Your threat hunting crew should also include at least one member with deep and broad institutional knowledge. That internal intelligence will help determine whether an unusual pattern is genuinely anomalous or part of the regular business practices of a particular department. That can save you a lot of time following up on dead ends.
Finally, place a time boundary on your threat hunt. A defined time for the search is crucial in organizations that are driven by metrics. The number of threats found doesn’t necessarily determine the success of a threat hunt, so an ongoing and ad hoc search might yield disappointing metrics. When your goal is to spend a set amount of time on each hunt, your success is determined by execution rather than the number of threats you discover. That can deliver the positive metrics you need to maintain management support for this essential cybercrime deterrent.
Placing time boundaries around your threat hunt has an additional benefit for team building. When you plan a hunt for a set period of time, it’s easier to assemble the team you need for a thorough and effective process. Gathering a skilled team and conducting a time-bounded hunt will improve your overall outcome.
What are examples of threat hunting?
Proactive threat hunting uses the hypothesis-based model outlined above. An example of a hypothesis-based hunt would be using global threat intelligence to determine the kinds of cyberthreats most likely to be present in your network. This type of threat hunt might use a free, accessible library, such as MITRE ATT&CK, which provides a curated knowledge base of cybercrime techniques that threat hunters use to develop hypotheses and tactics for defense.
A hypothesis hunt is a preferred strategy because it allows you to detect developing threats early. However, in some cases, you will have no choice but to react to a situation that has already developed. For example, if you start with an indicator of compromise (IoC)—forensic data that indicate a computer intrusion with high confidence—you will structure your hunt around the IoC to find its root cause and mitigate the damage.
Reactive threat hunts come after your security system detects an anomaly. Real-time endpoint monitoring gives you timely alerts about potential threats, so you can catch and control them early.Your threat hunting crew should include someone who has recently joined the company, perhaps a team member who is newly out of college.
A hunt based on indicators of attack (IoA)—early warnings that reveal suspicious events—falls between reactive and proactive threat hunting. In this case, your hunt will originate from the IoA, but you’ll have to conduct your search without knowing whether the attack has already breached your network.
What are key indicators threat hunters look for?
Threat hunters can search for a variety of clues that point to potential malicious activity, including the following key threat indicators:
- Hash values. A hash value is the unique numeric ID generated from the contents of an electronic file. Hash values change when someone alters the file contents, so unexpected changes in hash values provide a potential threat signal.
- IoCs. IoCs indicate that your system may have been breached. When an IoC is detected, it’s vital to locate the source as quickly as possible through forensic investigation and threat hunting. After you find the origin, you can move on to incident response and remediation. Proactive threat hunting shortens your response time to IoCs so that you can begin remediation quickly.
- IoAs. IoAs can indicate a breach is imminent. An IoA means that someone may be trying to get into your system from the outside. Regular monitoring of IoAs to determine the threat level and to detect vulnerabilities is a threat hunting best practice.
- Attacker TTPs. Cyberattack tactics, techniques, and procedures (TTPs) are indicators based on the known fingerprints of malicious actors. Studying attacker TTPs is an excellent way to kick off a hypothesis threat hunt.
- Malicious IPs. Threat hunters can identify an internet protocol (IP) address as potentially malicious if it displays specific characteristics: It may connect to infected devices or be the source of a high volume of suspected spam emails. You can compare multiple lists of known malicious IPs against the IPs you see connecting to your network. However, new malicious IPs come online all the time, so you can’t rely solely on publicly compiled lists.
- Anomalies and outliers. Anomalies can include an unusual level of network activity in a particular node, an app installed on the endpoint device of a user who shouldn’t need that software, or a user whose device has characteristics that aren’t shared by the devices of others who fill similar roles in the organization.
- Repetition. Threat hunting is a search for pattern and deviation. If a process happens repeatedly, especially if it originates from multiple IP addresses, that can indicate malicious activity. A process that repeats more frequently than expected is a key indicator of a potential threat.
These are general categories for threat hunting, but they don’t cover everything. Threat hunts often rely on custom content rather than out-of-the-box solutions. Plan to to tailor your hunt and launch it from a platform that gives you the power to further customize your capabilities and integrations and you’ll have a more robust and valuable threat hunt.
What are the challenges of threat hunting?
Understanding where to start the hunt is one of the most significant challenges in threat hunting. You begin with a wide-open field you need to narrow down into a hypothesis you can confirm or invalidate. Seasoned threat hunters have experience with many of the cybersecurity threats your organization could be facing. They will be able to help steer the process and develop a plan.
[Read also: 5 ways your company can avoid becoming a headline]
Conversely, professionals immersed in the world of cybercrime face another challenge. Because they rarely use technology the way average users do, they may be blind to common security threats. To overcome this challenge, include junior associates in your threat hunt planning and execution. Their fresh perspective can identify potential threats based on typical user behavior.
How do you improve the threat hunting process?
Threat hunting, like most cybersecurity operations, requires continuous innovation and improvement. The following are some of the ways you can improve your threat hunting process:
- Continuously monitor your endpoints. By doing so, you will have a baseline of usage data from which to start your hunt.
- Assemble a diverse team. An effective squad of hunters will represent a variety of areas of expertise and levels of experience.
- Don’t skimp on research. Giving yourself ample time in this initial phase will increase the success rate of your threat hunts.
- Act with precision. Conduct time-limited, planned hunts with well-defined metrics for success.
How do you get started with threat hunting?
If your organization isn’t proactively hunting for cyberthreats, it should be. Before you get started, you can increase your threat hunting knowledge through expert-led webinars and in-depth articles. Also, threat hunting doesn’t happen in isolation. You can get support to start threat hunting from the cybersecurity community, which thoroughly catalogs potential threats.
Proactive threat hunting is essential to the health of your network. The best time to start threat hunting was years ago. The next best time is right now.
More resources:
The Hunt Is On: Practical Ideas to Search for Risks and Exposures Using Tanium
Data-driven Threat Hunting With Tanium + Google Chronicle
Tanium Security Workflow: Advanced Hunting for Evidence of an Attack
Tanium Security Workflow: Threat Alerting and Analysis, and SIEM Integration
Fusing Global Artifact Collection Into a Tanium Threat Hunting Program






