5 Charts That Explain IT's Crisis of Visibility
Asset visibility and tool sprawl are two of the top issues bedeviling enterprises and putting business resilience at risk, according to a new IDG survey.
Even before the pandemic sent millions of workers home with their laptops, PCs, and tablets, requiring them to remotely connect to corporate networks, IT security teams were struggling with network complexity.
Now, as large companies delay office returns or settle into long-term hybrid models or simply feel their way forward, those teams face an existential crisis: trying to achieve real-time network visibility.
A key pain point in the struggle will be complying with regulations around data protection, especially in the wake of massive cyber breaches against business, government, and utilities.
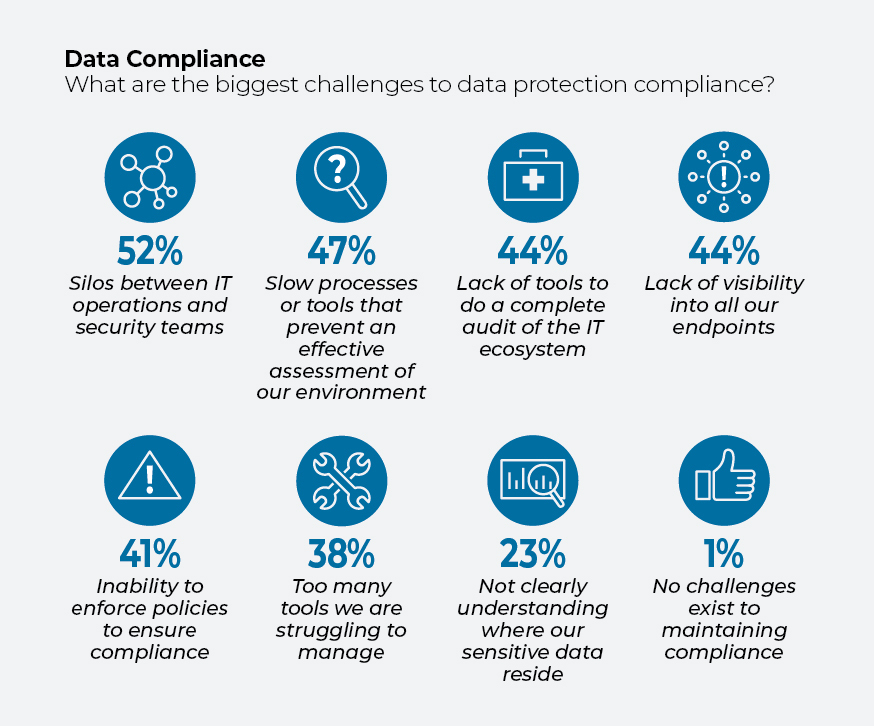
Among the biggest challenges to compliance, according to a new survey of 308 IT decision-makers worldwide by consultancy IDG Connect, are data silos between IT operations and security teams (52%), slow processes or tools that prevent an effective assessment of the IT environment (47%), and a lack of visibility into all endpoints that connect to the network (44%).
At the same time, only 30% said they are confident in their ability to see more than 85% of their endpoints, according to the survey, which IDG conducted for Tanium by querying IT leaders at enterprises with between 1,000 and 25,000 workers.
Tanium’s Cyber Hygiene Assessment: An actionable path to better endpoint management and security
That means there are a lot of companies out there that don’t know what hardware and software they are operating or how secure it is.
What often clouds visibility is the epidemic of tool sprawl, layers upon layers of new and legacy tools that are often outdated, forgotten, or unable to talk to each other. In fact, 38% of those surveyed say they have too many tools they are struggling to manage.
Below are five charts that explain the survey’s key takeaways.
Compliance barriers
Regulatory data protection compliance is hard enough, but it’s made more so by the presence of siloed workflows among teams, the lack of the right tools, and proper visibility into assets.
Those surveyed ranked the persistence of silos (52%) between security and IT operations teams as the top challenge to achieving data protection compliance. What hampers collaboration is not humans refusing or unable to communicate. It’s the hard-to-compare data readouts from siloed tools and data sources. What both sides need is a single, shared source of truth.
In addition, nearly half of respondents say their processes or tools are too slow, preventing an effective review of risk, while 44% say a lack of visibility into endpoints—like laptops, phones, and printers—is hampering their efforts. Some 38% are simply struggling with too many tools.
The IT view and the security view
The limited visibility that IT teams have over asset inventory paints an alarming picture. IDG found that only 30% of respondents felt confident in their organization’s ability to see into more than 85% of endpoints.
This mindset differs between IT teams: Three out of 10 security professionals say they are confident their company has visibility into 75% of endpoints, while only 22% of IT operations professionals agree visibility is this low.
IT operations teams seem more assured on other issues as well. Two-thirds of IT operations respondents regard the risk introduced by remote working as challenging, compared with 75% of IT security professionals. 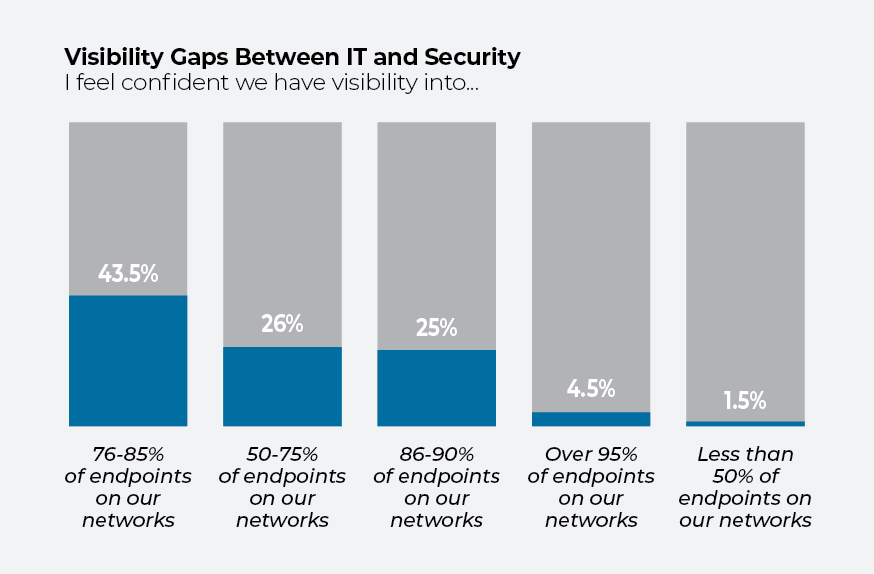
Quarantining bad assets
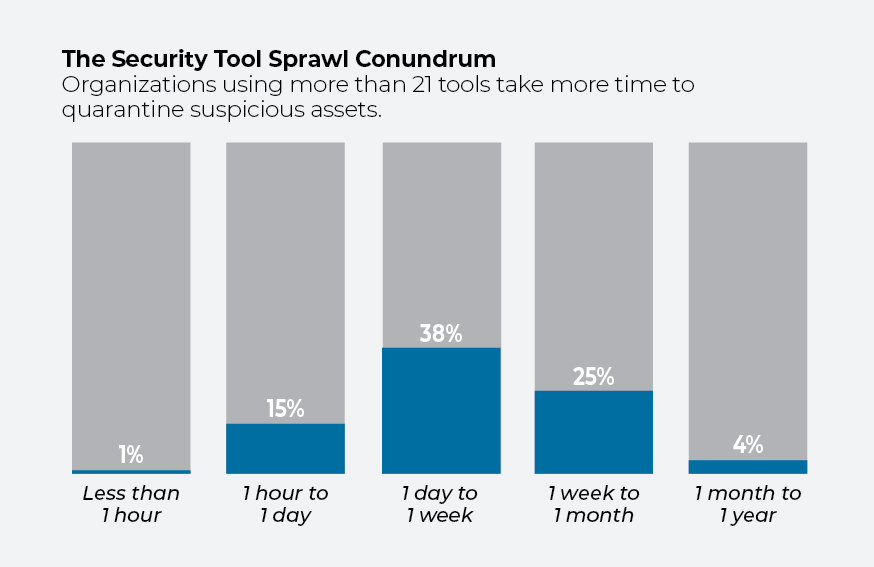
The number of organizations able to quarantine suspicious assets within an average of one day is just 30%, according to the survey, while 43% take up to a week, and a further 28% take more than one week. While 90% of respondents take the view that adding more security tools makes an organization more secure, the poor performance of companies with a high tools ratio questions the accuracy of this view.
[Read also: Federal cybersecurity—too many tools spoil the broth]
For companies with 20 tools or less, a third take a day or less to quarantine an asset, compared with 16% of companies with more than 21 tools. Organizations with more tools are also less confident in their ability to detect a breach. Thirty-four percent of respondents in organizations using 21 to 30 tools say they are confident in their ability to detect breaches in real time, compared to 42% among organizations using a smaller number of tools.
Assessing risk
In spite of the challenges IT professionals face in getting visibility across their systems and getting the best use of security tools like patching and vulnerability configuration, more than 80% of respondents say they are either confident or very confident about the ability of their teams to assess the company’s risk posture and communicate that risk posture to the C-suite.
However, the survey found that senior IT leaders (CIOs, CTOs, and CSOs) are less likely to be very confident about their organization’s risk assessments.
 The priorities ahead
The priorities ahead
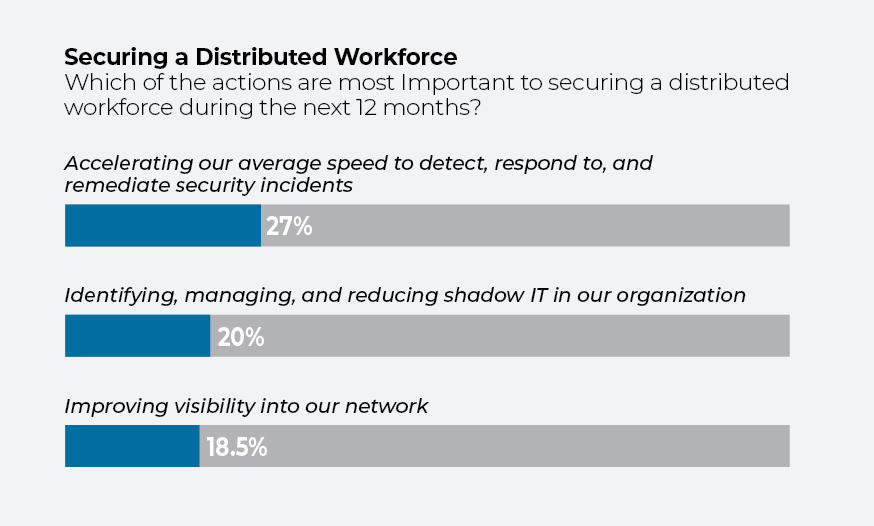
It’s reassuring to note that IT leaders are under no illusion about what’s at stake. When asked about their biggest priority over the next 12 months, 27% of respondents say the need to speed up the detection, response, and remediation of security breaches. Twenty percent say their biggest challenge is identifying, managing, and reducing so-called shadow IT—software, applications, and systems not overseen by central IT, while 18.5% say improving network visibility is at the top of the list.
And given the on-the-ground challenges, IT professionals have their sights set high. More than 80% agree on the need to move endpoint security to the cloud, and 89% see zero-trust practices as a priority.