7 Best Practices for Configuration Management
Today’s enterprises are more distributed, making them more vulnerable to security attacks than enterprises were 10 years ago. That’s why IT configuration management tools and practices need to change to keep up.
Configuration management is the process of monitoring the hardware and software configuration of computers and changing configurations when necessary to ensure they stay in line with IT policies. Not surprisingly, those policies typically include guidelines for security and regulatory compliance.
Now that most organizations have shifted to a work-from-home (WFH) policy for employees, configuration management is more important than ever. That’s because an organization’s IT department no longer has ready access to the computers that employees are using.
Those computers, which may include mobile devices employees bought and set up themselves, may have fallen behind on software patches. Or they might be missing updates to antivirus software.
Falling behind on security software updates increases a computer’s vulnerability to malware and other forms of attack.
[Read also: Are cybersecurity analytics missing from your security strategy?]
Benefits of getting configuration management right
It’s tempting to assume that because employees have computers and are using the software and data sources they need for work, their configurations are “good enough.” But when problems occur, such as security attacks, the importance of configuration management becomes obvious to everyone.
There are less dramatic benefits to properly managing configurations, too. When a company gets configuration management right, it can realize these benefits:
- Improved user experiences and increased productivity
When computers are set up properly, they’re less likely to experience performance problems or security incidents that can result in sluggish performance or downtime. By eliminating these problems for users, configuration management improves user experiences and increases employee productivity. - Reduced security vulnerabilities
Configuration errors were found to have played a role in 45 percent of all data breaches, according to Verizon. Criminals know that most organizations are behind on installing software patches, even if those patches close important security vulnerabilities. By keeping endpoints properly configured, organizations can greatly reduce their chances of succumbing to data breaches and other attacks. - Faster time to repair
Because configuration management software reports the configuration of computers, it helps help-desk engineers and other IT staff troubleshoot problems more quickly, reducing mean time to repair (MTTR). When an engineer has a clear understanding of how a computer is set up, it’s easier to uncover problems with incompatible hardware and software, buggy applications, faulty device drivers, and so on. - Improved IT decision-making
Because configuration management data provides a comprehensive picture of the status of endpoints used for operations, IT leaders can make better, more informed decisions about IT purchases, application rollouts, and other important IT topics.
Increasing employee productivity and reducing security risks and MTTR are commendable goals, but organizations are unlikely to achieve them using old configuration management tools and practices.
Why? Today’s enterprises are more distributed, more varied in hardware and software, and more vulnerable to stealthy security attacks than enterprises were 10 and 20 years ago. IT configurations and configuration challenges have changed, so IT configuration management tools and practices also need to change to keep up.
7 best practices for configuration management in a WFH world
Here are seven best practices for configuration management in today’s modern WFH enterprise.
- Start with a plan covering people, processes, and technology
Effective configuration management means a lot more than launching and running a configuration management tool when new software releases come out. Effective configuration management involves people, processes, and technology. It requires planning about how configuration updates will be rolled out, who will manage those updates, how those people will be trained, and so on.It also requires well-defined processes for monitoring endpoints and updating endpoints when they are found to be out of compliance with configuration policies. And it requires a process for rapidly deploying patches or making other types of changes to respond to security threats or serious performance problems from recent changes.
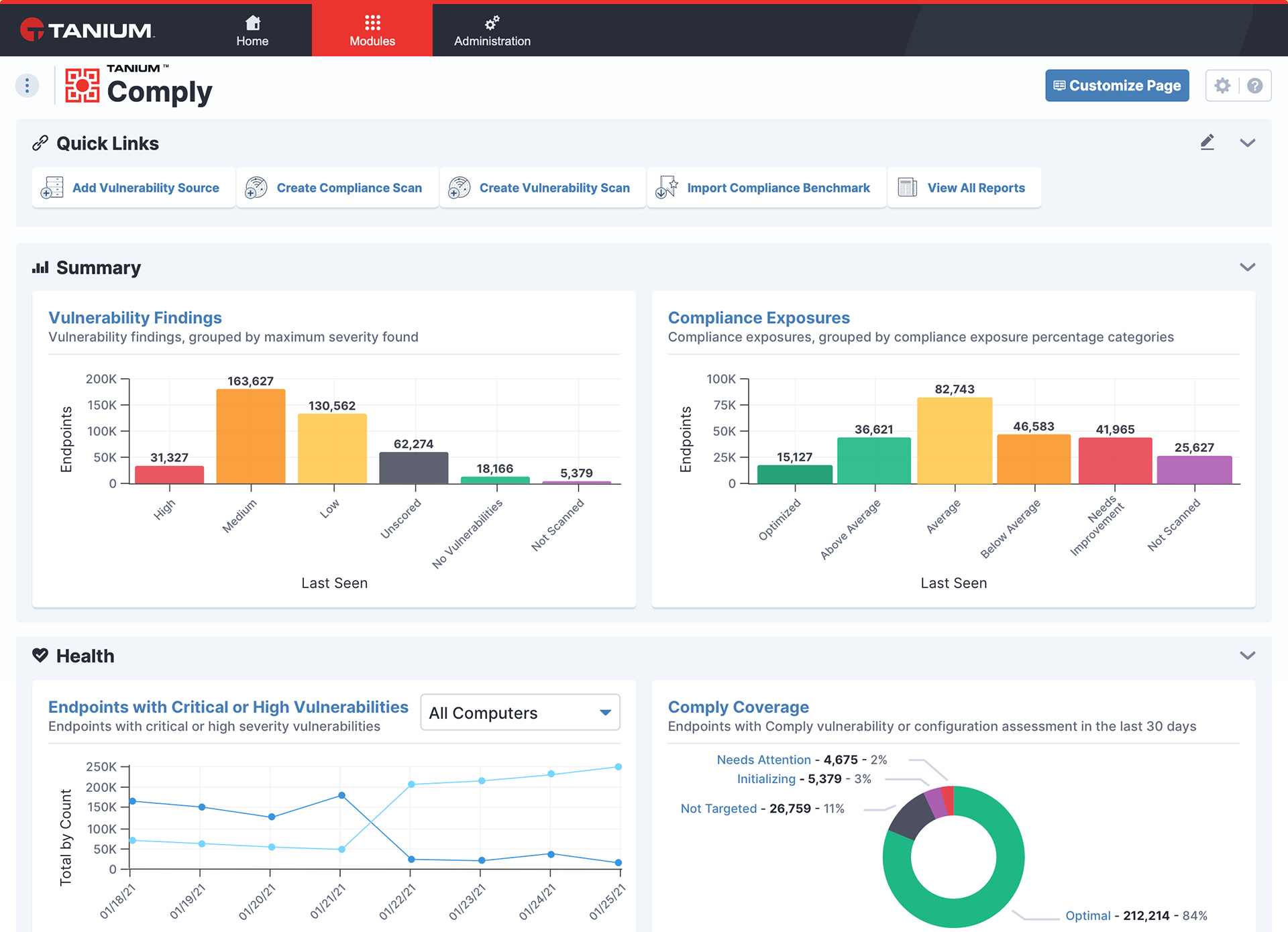
Ensure fast and reliable data gathering
Plans should be documented and understood by all the relevant stakeholders in the IT department. And those plans should include requirements for configuration tools and for training IT engineers on the use of those tools.
- Be able to monitor anywhere: on a local network, in a remote location, or in the cloud
WFH is likely here to stay in some form. IT organizations need a comprehensive way of managing configurations regardless of where an endpoint is being used. Whether an employee is working in the office, at home, or in some other remote location, the IT organization should be able to monitor and configure that employee’s endpoint flawlessly. - Leave no endpoint unmanaged
At most companies I visit, the configuration management process has two glaring shortcomings.First, the IT team can’t find all the endpoints being used by employees. On average, the configuration management products they are using miss 10-15 percent of endpoints that have been deployed — and that 10-15 percent gap was before companies switched to WFH, making endpoints even harder to find.
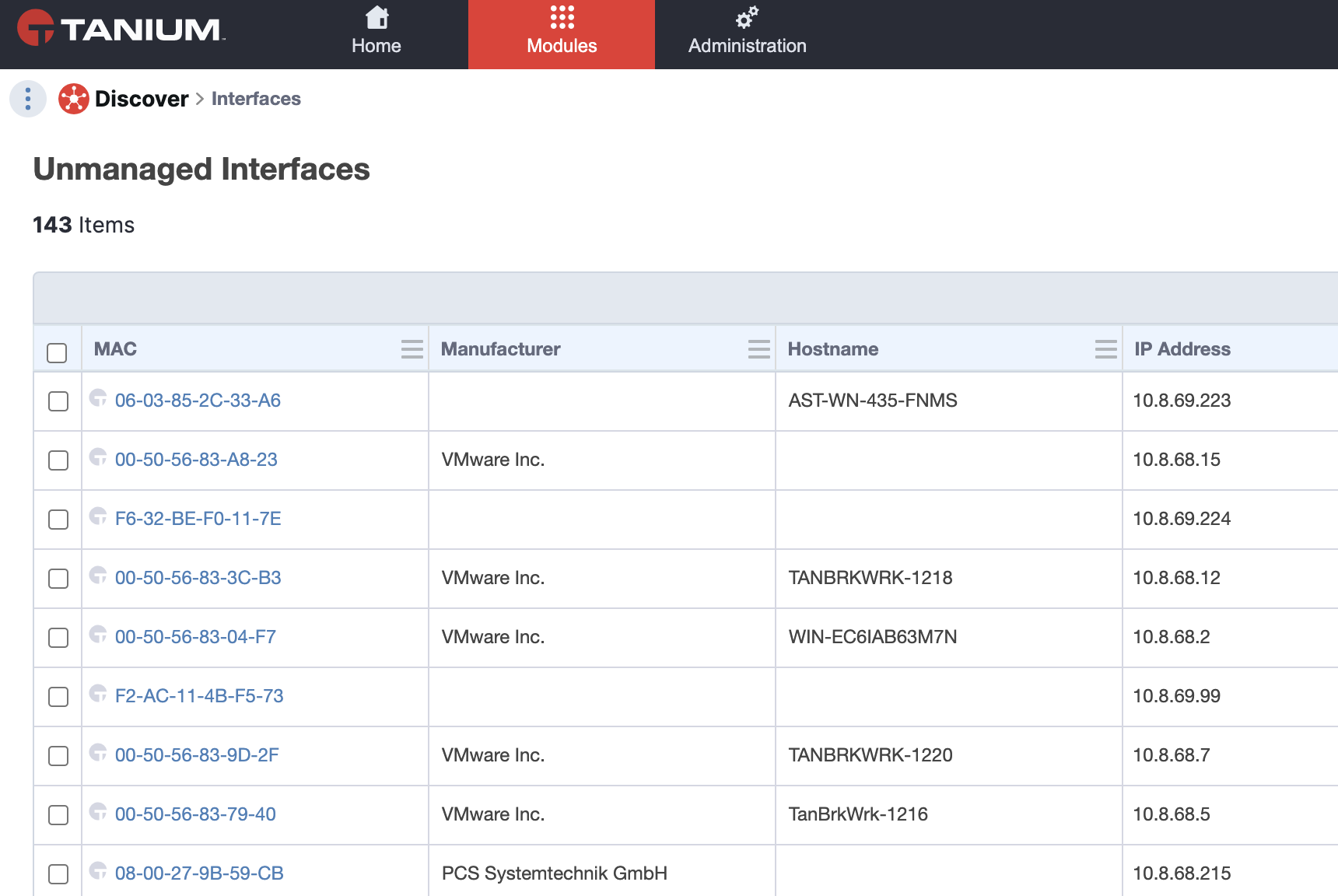
Quickly take back control of rogue endpoints
Second, IT teams can’t confirm that configuration changes have actually been implemented. Instead, they rely on a “spray and pray” model of configuration delivery.
To avoid security risks and optimize endpoint performance for employees, IT teams need to put together tools and processes to ensure that all endpoints have been found and that all changes to those endpoints have been implemented.
- All endpoints means endpoints with any operating system
Make sure your configuration management practices cover all the endpoints employees are using. Even if 98 percent of your employees are on Windows machines, and only a handful of people are on Macs, you still want to be able to manage the configuration of those Macs.Ideally, you should try to manage endpoints running the operating systems you’re most likely to encounter in a business setting: Windows, Linux, and macOS. - Make sure you can monitor and configure remote endpoints without requiring VPN access
It’s expensive to require remote endpoints to stay connected over VPNs 24/7 just so they can be monitored by the IT team.If possible, set up tools and processes for managing endpoints over any standard internet connection — no VPN required. That way, no matter where employees are working, the IT team will be able to stay on top of keeping their computers up-to-date and working well. And you’ll avoid the problem of employees complaining about the slow network performance that’s common with VPNs.
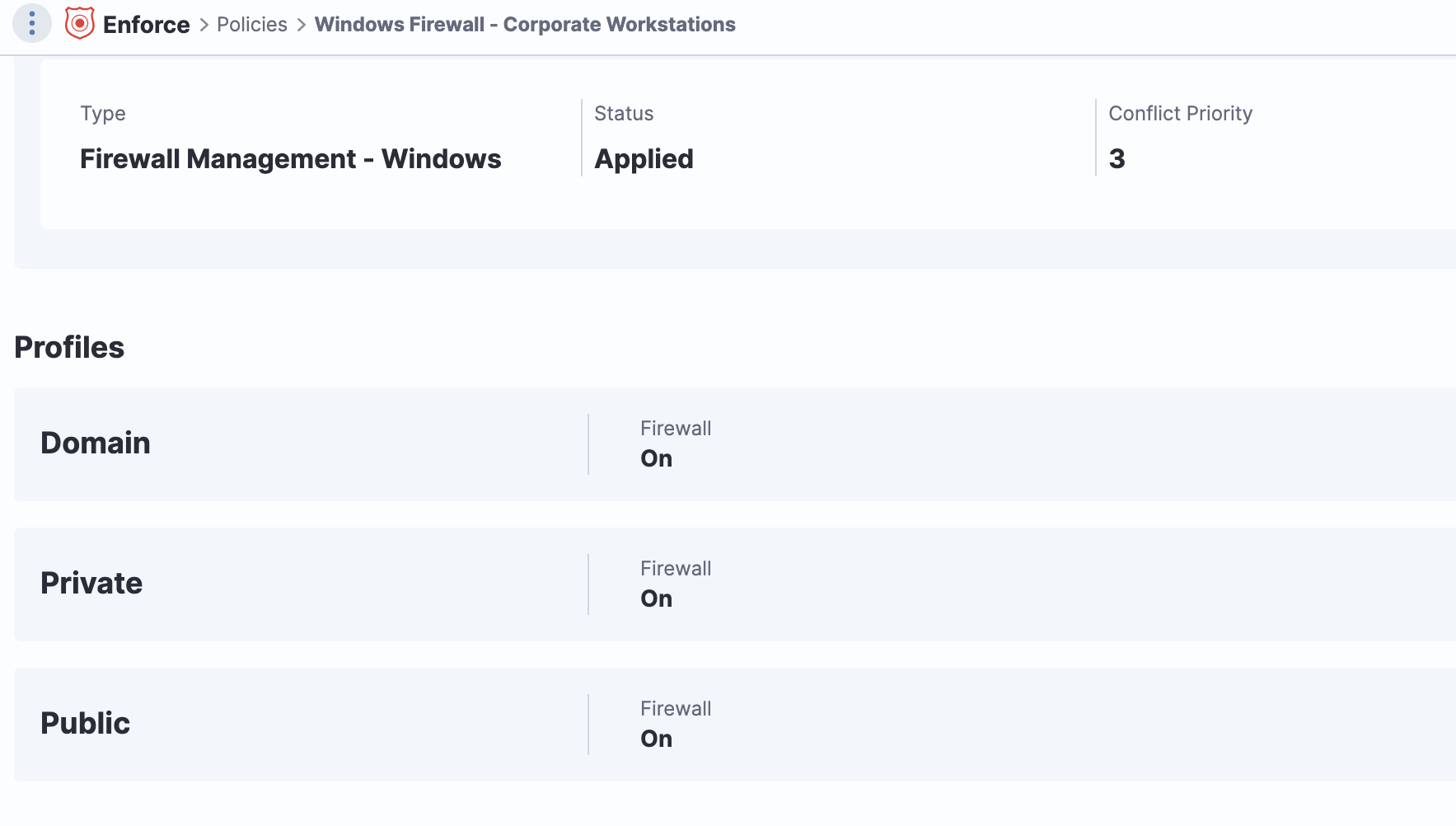
Monitor and maintain firewall policies on endpoints
- Avoid network traffic jams
A lot of traditional configuration management approaches require hundreds or even thousands of servers for monitoring endpoints and pushing configuration changes across corporate networks.It’s great that IT teams can muster these kinds of resources for configuration management, but if you can find a way to manage configurations with fewer servers and less traffic congestion, do so.
Software vendors have made a lot of progress over the past decade in making distributed networks more efficient. See if you can leverage some of those new techniques for configuration management. It’s a big difference, especially in companies with tens of thousands or even hundreds of thousands of endpoints. - Monitor results, remediate problems, and hone your processes over time
Configuration management isn’t a “one and done” or “once-a-quarter and done” kind of project. It’s an ongoing process.IT teams should continuously monitor the configurations of endpoints and make changes whenever necessary.To keep track of that ongoing work, it’s a good idea to build reporting and trend analysis into your documented configuration management processes.
IT leaders, as well as leaders of business units, should be able to understand “the big picture” about the state of the computers that employees depend on every day for work.
[Read also: Mastering employee engagement surveys: From data to action]
Keeping your fleet in fine, running order
Your IT infrastructure is a carefully orchestrated machine. Similarly, it doesn’t make sense to overlook the configuration of the computers that your organization depends on.
Follow the best practices I’ve outlined above, and it will help you avoid the computing breakdowns and risks that result from misconfigured computers. And you’ll reap important benefits, including increased productivity, happier employees, and greater resilience to security threats.
To learn more, check out the blog post 10 Ways Tanium Makes Configuration Management Better.
If you’re ready to see it in action, sign up for a demo today.



