Rising Trend in APT Hackers Using Excel Add-ins as Intrusion Vector
APT hackers turn to malicious Excel add-ins as initial intrusion vector, PurpleUrchin bypasses CAPTCHA and steals cloud platform resources, and Russia’s Turla APT piggybacks on other hackers’ USB infections
Up first, we look at a rising trend involving advanced persistent threat (APT) actors and commodity malware families increasingly leveraging Excel add-in files (.XLL files) as an initial intrusion vector. Next, we cover the latest information on Automated Libra, the cloud-focused threat actor behind the freejacking campaign tracked as “PurpleUrchin.” Finally, we take a deep dive into Mandiant’s recent report on malicious activity attributed to the notorious Russian state-backed threat group, Turla.
1. APT hackers turn to malicious Excel add-ins as initial intrusion vector
According to a threat spotlight blog by Cisco Talos, advanced persistent threat (APT) actors and commodity malware families are increasingly leveraging Excel add-in files (.XLL files) as an initial intrusion vector.
The observed increase in the use of XLL files comes after Microsoft’s decision to block the execution of VBA macros by default. Microsoft Office applications now go through a stricter decision process and restrict users from running macros when a document has a Mark of the Web (MOTW) tag. Microsoft’s decision to block macros was largely due to the fact that many threat actors leveraged VBA macros as their initial vector to deploy malware and ransomware.
Microsoft and add-ins: A brief overview
Add-ins are pieces of executable code that come in various formats and have many different capabilities. They can be added to Microsoft Office applications to enhance functionality.
- Word: For Microsoft Word, add-ins need to be dropped in a specific location that is specified by the registry value. If an attacker were to place a DLL into a trusted location using the file extension .wll, Word would attempt to load the DLL into its own process space.
- Excel: For Microsoft Excel, if the user attempts to open a .XLL filer in Windows Explorer, the shell automatically attempts to launch excel to open the file. Before an XLL file is loaded, Excel displays a warning about the possibility of malicious code being included – this is a similar warning/approach displayed after a document containing VBA macro code is opened. This sounds good in theory, but most people tend to click past this and disregard the warning without thinking.
What are XLL files?
XLL files are standard Windows dynamic loading libraries (DLLs). What differentiates an XLL file is its ability to implement certain exported functions which will be called by the Excel add-in manager. The add-ins are created in native code, and they enable developers to extend Excel’s functionality.
- C/C++ based XLLs: Native XLL add-ins are developed using the Microsoft Excel XLL software development kit (SDK). For an add-in to be loaded by the add-in manager, the XLL must implement at least one exported function, called xlAutoOpen, so the code can be called with the add-in is loaded by Excel. The Excel XLL SDK consists of C/C++ header files and libraries that allow XLL files to use the Excel API to access workbook data and call Excel functions.
- Excel-DNA based XLLs: Two popular frameworks, Add-In Express and Excel-DNA, allow developers to create XLL add-ins using .NET languages. Since Excel-DNA is a free framework, many malware authors have adopted it to create malicious XLL files.
The evolution of malicious XLLs
Cisco Talos was able to track the number of VirusTotal submitted native and Excel-DNA based malicious files over time.
Cisco Talos also dug deeper and determined mid-2017 to be the beginning of threat actors leveraging XLL files as a vector to execute malicious code. It appears the usage of XLL files was sporadic until 2021, when commodity malware families like Dridex started using it.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“It seems as though Microsoft’s decision to block VBA macros is not the only reason for the increase in XLLs as infection vectors. The significant increase has been observed over the last few years and began well before Microsoft’s well-received macro blocking decision. Regardless of the reasoning and timeline, more and more commodity malware families and threat actors are adopting XLLs. A recent example involving XLLs is the Ekipa RAT which has incorporated XLL Excel add-ins in its attacks along with taking advantage of Microsoft Publisher macros to drop the remote access trojan.”
2. PurpleUrchin bypasses CAPTCHA and steals cloud platform resources
Palo Alto’s Unit 42 recently performed a deep dive into Automated Libra, the cloud threat actor behind the freejacking campaign PurpleUrchin.
Automated Libra is a South African-based freejacking group that is known to target cloud platforms that offer limited-time trials of cloud resources. The free trials are then used by the threat actor to perform cryptomining operations. The threat actor is said to be behind the freejacking campaign known as PurpleUrchin.
Automated Libra was observed using a new CAPTCHA solving system, following a more aggressive use of CPU resources for cryptomining, and mixing techniques to abuse free cloud resources.
What is PurpleUrchin?
The PurpleUrchin cryptomining campaign was observed in October 2022 as a freejacking operation. The campaign relied on the abuse of resources offering free-tier cloud accounts to generate a small profit from each free account, resulting in a more significant dollar amount when combined.
The actors behind PurpleUrchin used Play and Run operations by creating and using fake cloud accounts with either falsified or potentially stolen credit cards. The fake accounts resulted in unpaid balances for the cloud services.
Palo Alto’s Unit 42 analyzed over 250GB of data, including container data and system access logs. The infrastructure architecture used by the threat actors uses CI/CD techniques, where each individual software component of an operation is placed within a container. The CI/CD architecture allows some components of an operation to fail/update/terminate without causing impact to the larger environment. Analysis allowed researchers to trace this threat actor’s activity back to August 2019. It also revealed the threat actor’s preference for using cloud services via traditional virtual service providers, or VSPs.
Mining with GitHub workflows
The threat actor’s operations on GitHub used a combination of Play and Run and freejacking tactics. The threat actors automatically created GitHub accounts at an average rate of three to five per minute. After establishing the account base, the freejacking activity began.
Each GitHub account was subsequently involved in a Play and Run strategy in which each account would use the computational resources provided to that account, but the resulting bill was left unpaid. Researchers uncovered evidence of the threat actor creating over 130,000 accounts across various virtual private server providers and cloud service providers.
Automating GitHub account creations
One of the threat actor’s latest observed deployments involved running Togglebox using AHP services. Togglebox is a fully managed solid state drive cloud VPS and application hosting platform. The threat actor leveraged this platform to run a series of containers. Each container is capable of automatically creating GitHub accounts. Researchers also identified a switch called “named” based accounts within the user account creation Python process. This process used randomly generated named accounts based on Md5 hashes.
The tools needed for the automatic account creation process were shipped as a container. With the latest version of the container, the threat actor combined multiple publicly available and legitimate tools including Iron Browser, xdotool, and ImageMagick. After the tools are in place, the threat actor can begin creating accounts.
Leveraging a CAPTCHA weakness
Creating a GitHub account requires solving a CAPTCHA test. To accomplish this, the threat actor uses two tools from the ImageMagick tools kit including convert and identify.
The CAPTCHA images are first converted into red, green, and blue complemented images using the convert tool.
After the images are converted, the identify command is executed over each image to extract the “skewness” feature. The result is an arranged list in ascending order, revealing the accurate answer as the smallest value.
Once the CAPTCHA is solved, GitHub requires a launch code which is sent to the account email. The threat actor used a Gmail account in this sample to automate the process of getting the launch code by reading incoming IMAP messages.
After the access code is entered, the automation generates a personal access token with workflow permissions. The naming convention has changed in more recent operations where the threat actor is now using random names for the repositories, which were based on MD5 hashes.
Created accounts
Unit 42 has estimated the number of GitHub-created accounts.
After the repository is created in GitHub, a bash script is invoked to update it with the desired workflow. The workflow itself is generated using a PHP script. The workflow mechanism allows the threat actor to execute external applications. In one observed instance, the generated workflow ran 64 total jobs, where each job randomly selected 1 out of 5 available unique configurations.
One of the preferred cloud services used by the threat actor during 2021 was Heroku – a cloud application platform that allows its users to create and deploy applications without maintaining the hosting infrastructure. Researchers identified over 100,000 unique accounts created on the Heroku platform.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“The use of Automated Libra’s CAPTCHA-solving system to create GitHub accounts without manual intervention is impressive. It’s no secret that threat actors stand to make some serious money carrying out cryptomining operations, and this automated account creation process only makes it even easier for cybercriminals. This CAPTCHA bypass technique serves as another example of how threat actors will continue to improve and mature such methodology to better carry out their operations.”
3. Russia’s Turla APT piggybacks on other hackers’ USB infections
A new write-up published by leading cyber threat intelligence firm Mandiant highlights the latest activity attributed to Turla, a notorious Russian advanced persistent threat (APT) group believed with a high degree of confidence to operate at the behest of Russia’s FSB intelligence service.
Along with providing information pertaining to new command-and-control (C2) domains registered by Turla and the group’s targeted deployment of KOPILUWAK and QUIETCANARY malware, Mandiant describes how Turla gained access to victim networks by registering the expired domains formerly associated with a nearly ten-year-old cybercriminal campaign that spread malware via infected USB drives.
USB piggybacking
Mandiant’s report is the result of its September 2022 discovery of an interesting breach of a network in Ukraine, in which several of the computers in that network had become infected after someone inserted a USB drive into a device’s open port.
Mandiant eventually determined the activity to be related to a Turla operation in which the threat actor was able to re-register at least three expired ANDROMEDA C2 domains. This allowed Turla to dig through victims of the relatively old malware (ANDROMEDA was a popular commodity malware in the early 2010s), profile targets, and selectively deploy both the KOPILUWAK reconnaissance utility and QUIETCANARY backdoor against Ukrainian victims.
A note on ANDROMEDA
As stated above, ANDROMEDA was a widespread commodity malware that reached peak popularity sometime in the early 2010s. In this incident, Turla hijacked the infrastructure of a variant that was first uploaded to VirusTotal in 2013. As it happens, this ANDROMEDA variant spreads via the use of infected USB keys.
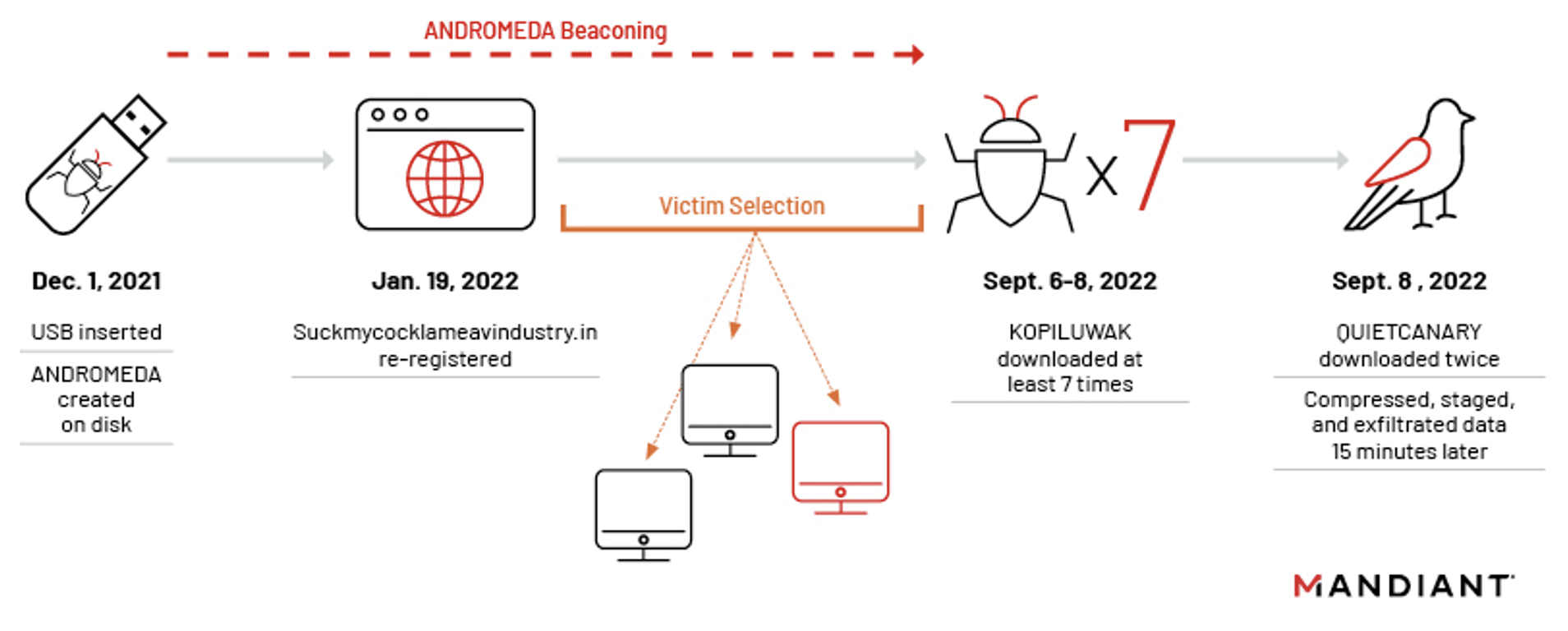
Timeline of ANDROMEDA-to-Turla intrusion. Image courtesy of Mandiant.
This incident stems from a USB key, infected with several strains of older malware, being inserted at a Ukrainian organization in December 2021. According to Mandiant, when the targeted system’s user double-clicked a malicious link (LNK) file disguised as a folder contained within the USB drive, a “legacy ANDROMEDA sample” was automatically installed, at which point it began to beacon out.
Since this version of ANDROMEDA had been uploaded to VirusTotal back in 2013, it follows that most of the malware’s C2 domains had been sinkholed by researchers, or simply expired after nearly a decade. When this particular binary was executed, it established persistence by dropping yet another ANDROMEDA sample to C:\ProgramData\Local Settings\Temp\mskmde.com and added a Run Registry Key to execute it each time the system’s user logged on. Mandiant was able to determine that one of its expired C2 domains had been re-registered in January of 2022 by a privacy-protected registrant, with Dynadot being the accommodating registrar.
By leveraging this C2 to profile existing victims of this malware sample, Turla was able to selectively target interesting users with the first-stage KOPILUWAK dropper.
Recon with KOPILUWAK
According to Mandiant, Turla eventually downloaded and executed a WinRAR Self-Extracting Archive (WinRAR SFX) containing KOPILUWAK onto a victim’s device in September 2022, following several months of ANDROMEDA beaconing which resulted in no significant activity being observed.
Altogether, Mandiant’s researchers observed the attackers download and execute the same WinRAR SFX KOPILUWAK dropper seven times that month, each time attempting to transfer “significant amounts of data to the C2 manager.surro[.]am.”
Why the attackers did this remains unknown. The victim profiling commands in KOPILUWAK are hardcoded, and as such, would not yield different sets of data originating from the same targeted host.
In the incident described by Mandiant, the process “wauclt.exe” was injected by ANDROMEDA and subsequently issued GET requests for “yelprope.cloudns[.]cl” with the target URL “/system/update/version.” This domain is a dynamic DNS subdomain hosted by ClouDNS and was previously linked to ANDROMEDA activity and was another domain re-registered by Turla.
Essentially, Turla leveraged KOPILUWAK as a first-stage target profiling resource, with KOPILUWAK representing the first custom Turla malware used by the attackers after ANDROMEDA. KOPILUWAK aided Turla in facilitating network reconnaissance on the victim host, using utilities such as whoami, netstat, arp, and net, seeking active TCP connections with PID and locating network shares before enumerating logical disks and current running processes. The results of all commands were piped into %TEMP%\result2.dat, before being uploaded to KOPILUWAK’s C2 “manager.surro[.]am” with POST requests.
QUIETCANARY enters the picture
Following the initial execution of KOPILUWAK, Turla was observed twice downloading the lightweight, .NET backdoor QUIETCANARY to a host (though commands were only executed in the second instance). QUIETCANARY was primarily used by Turla to harvest, compress, stage, and ultimately exfiltrate victim data. QUIETCANARY was written to disk.
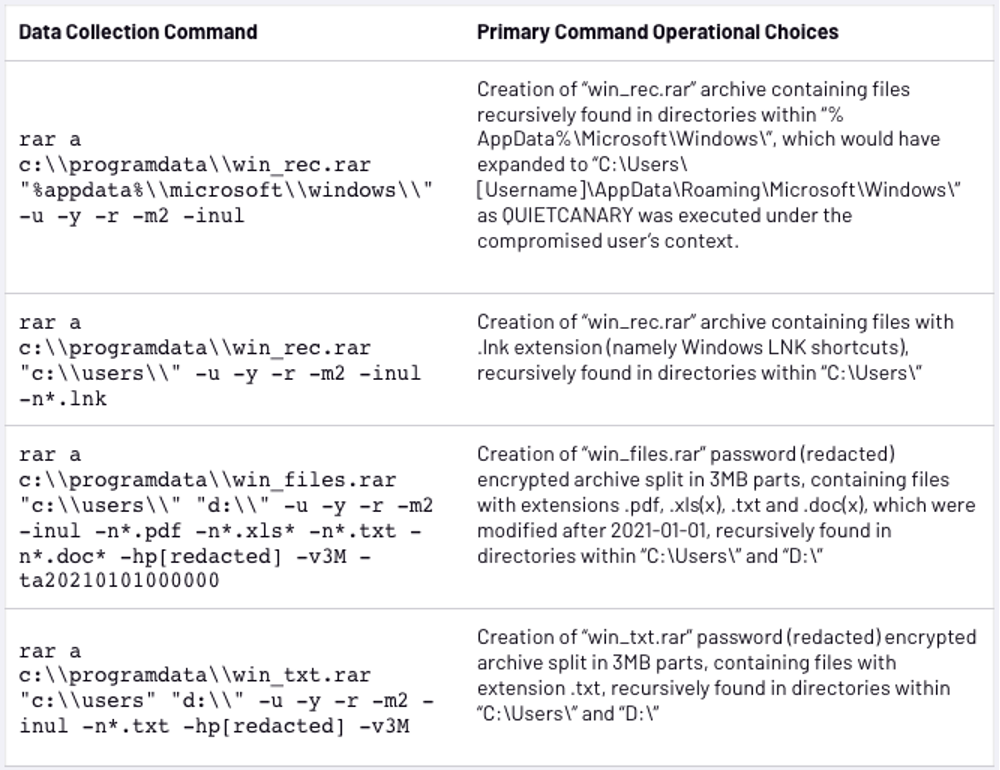
Mandiant was able to observe the interactive commands sent to QUIETCANARY and executed by the backdoor.
Note: Occasional typos in the commands issued – and their subsequent correction and reissue – suggested that this was a manual process, as opposed to automated data collection.
QUIETCANARY commands. Image courtesy of Mandiant.
Interestingly, Turla only appeared to be concerned with the exfiltration of files created after January 1, 2021.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“In its report, Mandiant makes a point of acknowledging that the Turla payloads involved in this incident have only been observed in Ukraine. In fact, Mandiant only observed this single instance of a hijacked ANDROMEDA infection being used to distribute Turla malware. However, it would be unwise to draw the conclusion that Ukraine is the only place in which Turla has carried out this type of operation. It would be equally unwise to conclude that Turla attacks piggybacking off ANDROMEDA infections have been limited to just one target. It would also be reckless to assume that Turla will be the only actor to leverage existing infections for its own purposes. It is likely that other threat actors with differing motivations will seek to capitalize upon previous intrusions in a manner consistent with the activity described herein.”
In fact, this is not the first instance of Turla hijacking the attack infrastructure of other threat actors. As stated in a Wired article on the subject:
Turla has a long history of using clever tricks to hide the control of its malware, and even to hijack the control of other hackers, as Mandiant saw in this most recent case. Cybersecurity firm Kaspersky revealed in 2015 that Turla had taken control of satellite internet connections to obscure the location of its command-and-control servers. In 2019, Britain’s GCHQ intelligence agency warned that Turla had silently commandeered Iranian hackers’ servers to conceal themselves and confuse detectives trying to identify them.
“USB-based hacking techniques seem to have experienced a resurgence in recent years, and Mandiant’s observations of Turla’s stealthy methodology in this incident should serve as a reminder to security professionals that this particular intrusion vector is far from obsolete – and, when placed in the hands of an operator as sophisticated and well-resourced as Turla’s, this technique still poses a significant threat.”
For further reading, catch up on our recent cyber threat intelligence roundups.




