Endpoint Detection and Response 101: What EDR Is and Where It Falls Short
Endpoint detection and response tools are designed to detect known bad activity. But it can’t find where attackers are hiding, investigate what they did, or remove them from your environment. Here’s how Tanium can fill those gaps.
Endpoint detection and response (EDR) tools are made to detect known bad activity. But what protects your blind spots where attackers hide these days?
Your organization needs a tool that can find and fix what the attackers did or even where they’re currently hiding in your IT environment. The right solution provides visibility, investigation, and remediation capabilities on your company’s device endpoints — wherever they reside.
This article covers:
- What EDR is and what requirements EDR covers
- What gaps Tanium Incident Response fills that EDR cannot
- Why you still need Tanium Incident Response when you have EDR
What is EDR?
Most EDR solutions are endpoint logging engines using heuristics (sophistication level about halfway between rules and neural network generated machine learning [ML] algorithms) to look for the “known” bad activity.
But there are a couple of limitations with this type of tooling. First, there are plenty of blind spots for attackers to hide in an environment because EDR tools were designed to “see” only specific types of activity running — they are intended to find the known bad.
Additionally, most EDR solutions limit the activity they will record and preserve to reduce bandwidth and storage consumption, including the number of days.
With that in mind, let’s list at a high level the requirements EDR does meet:
- Automated, simple pattern detection of known bad-attack types, leading to triage and investigation of those alerts.
- e.g., a file opened from the Recycling Bin, Execution via PowerShell, fileless exploits and “living off the land”-style attacks
- Automated response in the sense that automated actions can be configured from the detection rules
- e.g., blocking, process termination, creating a shell to the quarantined endpoint, and sending down a Python package
- Centralization of endpoint log and telemetry data in the cloud often before analysis
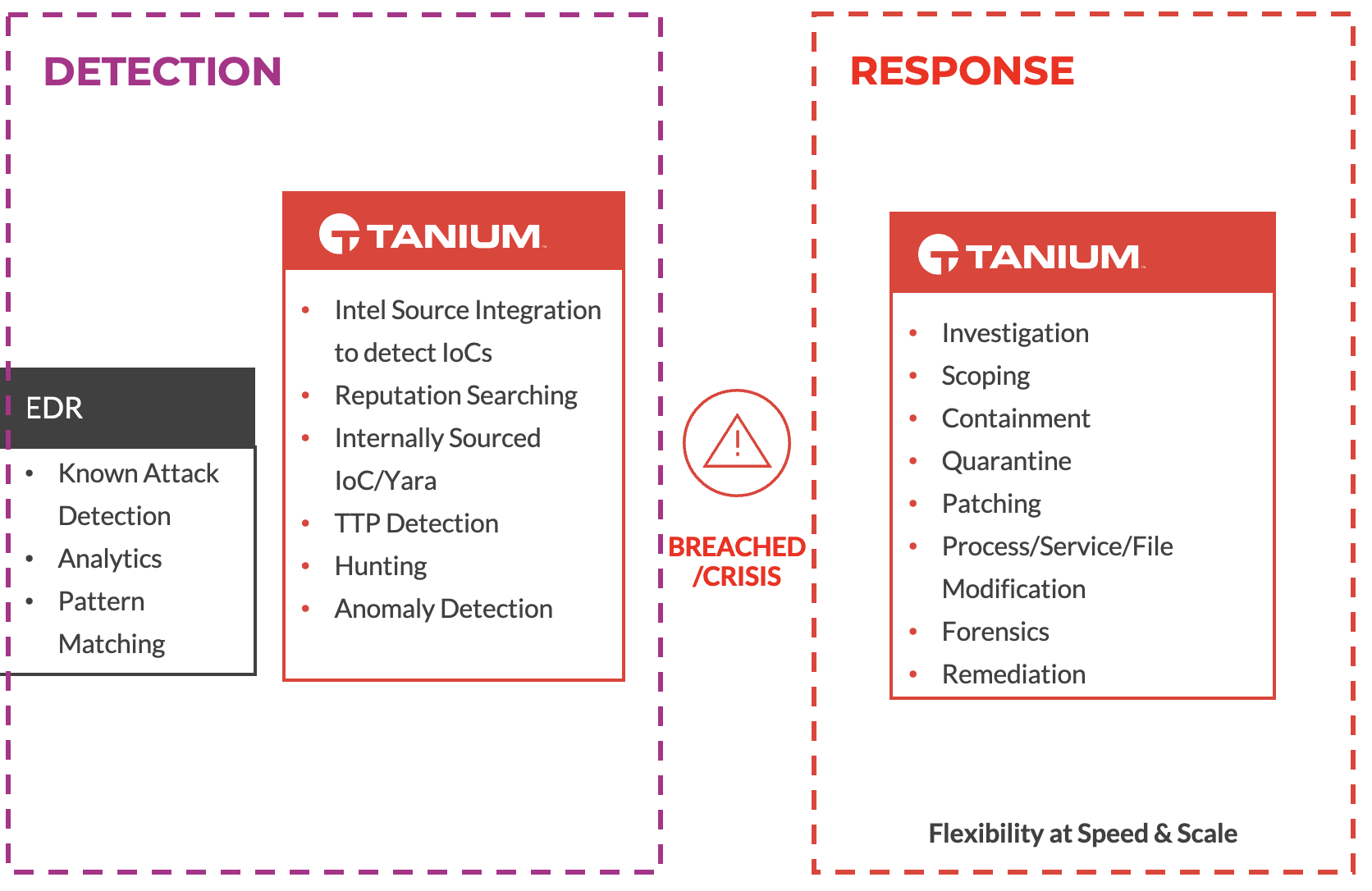
How EDR and Tanium complement each other
What gaps Tanium Incident Response fills that EDR cannot
Tanium Incident Response is a comprehensive, real-time, and historical investigation solution that allows users to search for and find any arbitrary artifact on an endpoint.
The advantage is that these artifacts do not need to be predefined as they are with EDR solutions. Because Tanium instruments are at the edge, Tanium can give you visibility into any monitored item of interest, the moment you need it.
Once you’ve used Incident Response for the investigation phase of your incident response lifecycle, you can execute tailored remediation using the speed and scale of the Tanium platform as a whole.
There are several capabilities Incident Response provides that EDR simply cannot, but we will narrow in on three of the most common ones:
- Endpoint scanning that can leverage in-house-developed and subscription-based intel, including IOC, STIIX, Yara, and Tanium’s own proprietary intel type. The ability to search for any arbitrary indicator of compromise is critical during an incident, giving security teams the confidence they need to take corrective action.
- Execution of a comprehensive remediation strategy by allowing users to dig deep into individual systems during the investigation phase and enabling those same users to take action across any number of endpoints simultaneously. For example, users can kill processes, delete registry keys, uninstall services, or more on one or hundreds of thousands of systems at the same time.
- Visibility into malicious behaviors when an attacker is smart enough to evade detection. Because of the breadth of forensically relevant endpoint telemetry that Incident Response collects and preserves, it gives users detailed and precise information about what an attacker did after gaining initial access. As skilled attackers can avoid tripwires with reasonable ease, security teams rely on Tanium to understand what was done and how to best eradicate the threat.
Why you still need Tanium Incident Response when you have EDR
EDRs were built to detect many, but not all, attack scenarios. They are designed to be elaborate tripwires. Skilled attackers with the knowledge of an EDR tool’s detection capabilities can work around these tripwires, even if for a short amount of time.
EDR can alert only on what it was designed to detect, the known bad. Their value to an organization is that they are alerting on an attack only as it’s happening, such as intellectual property exfiltration, or if the attacker slipped up.
But what happens when something gets past EDR? What happens when there is unknown bad in your network? How long are you willing to wait to know what an attacker did, what machines are affected, what the risks are to your organization? Better yet — how long are you willing to wait to stop the attack?
EDR can’t provide at-scale visibility into all of these things, nor does it allow you to be precise and swift in remediation.
Tanium Incident Response provides deeper and more comprehensive visibility by design. When your EDR detects suspicious activity and generates an alert, teams rely on Tanium to delve into the affected system.
They rely on Tanium to better understand the threat, find additional machines that could have been affected, and take action — to stop the bleeding. The value of Incident Response to your organization is that it’s perfectly crafted to hunt for and investigate attackers in the dwell time before, during, and after the initial alert, and gives you the confidence you need to get them out for good.
Tanium’s speed and power do not falter, regardless of how many endpoints you have and where they’re located around the world.
Learn more about Tanium Incident Response and set up a demo to see if Tanium is right for you.




