CTI Roundup: Google Ads pushes new BumbleBee malware
A new SLP bug potentially enables massive DDoS amplification attacks, Google Ads pushes new BumbleBee malware, and Chinese hackers use Linux malware variants for espionage
Up first in this week’s roundup is a summary of a new reflective denial-of-service (DoS) amplification vulnerability – impacting a widely used protocol – which could open the door for large-scale DDoS attacks. Next, CTI analyzes a Bumblebee malware loader campaign in which threat actors are leveraging Google Ads to promote trojanized versions of installers for popular applications. Finally, CTI breaks down a Palo Alto report on a new variant of the PingPull malware designed to target Linux systems.
New SLP bug can lead to massive DDoS amplification attacks
BitSight recently described a new reflective DoS amplification vulnerability in the Service Location Protocol (SLP) that reportedly allows threat actors to launch massive, distributed denial-of-service (DDoS) attacks with an amplification factor exceeding 2,200x.
The vulnerability — CVE-2023-29552 — allows unauthenticated, remote attackers to register arbitrary services. This potentially allows attackers to leverage spoofed User Datagram Protocol (UDP) traffic to conduct DDoS attacks with significant amplification vectors.
From BleepingComputer:
This flaw, tracked as CVE-2023-29552, was discovered by researchers at BitSight and Curesec, who say that over 2,000 organizations are using devices that expose roughly 54,000 exploitable SLP instances for use in DDoS amplification attacks.
What is the risk from CVE-2023-29552?
According to available reporting, vulnerable services include a wide range of platforms, including VMWare ESXi hypervisors, Konica Minolta printers, IBM Integrated Management Modules, Planex routers, SMC IPMI, and others.
BitSight determined that, given the vulnerability’s criticality and the potential consequences of successful exploitation, the security flaw warranted the coordination of public disclosure efforts with the Cybersecurity and Infrastructure Security Agency (CISA) as well as known impacted organizations. CISA has since released an alert, which is available here.
As stated in BleepingComputer’s coverage, the most known vulnerable instances are concentrated within the United States, Great Britain, Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain. A significant number of such instances are reportedly owned by various Fortune 1000 companies operating within the technology, telecommunications, healthcare, insurance, finance, hospitality, and transportation verticals.
SLP and the DDoS amplification threat
SLP provides a dynamic configuration mechanism for applications within local area networks (LANs). Ultimately, it is designed to serve enterprise networks with shared services.
From BleepingComputer:
Service Location Protocol (SLP) is an old internet protocol created in 1997 for use in local area networks (LAN), enabling easy connection and communication among devices using a system of service availability through UDP and TCP on port 427… While its intended use was never to be exposed on the public internet, organizations have exposed SLP on tens of thousands of devices over the years.
Unfortunately, the vulnerability discovered in the long-standing protocol — and the nature of SLP itself — makes it a perfect vehicle by which unauthenticated attackers may register arbitrary services on SLP servers. By manipulating the size and content of the targeted servers’ replies, attackers can potentially achieve a maximum DDoS amplification factor of 2,200x.
The significant number of exposed servers worldwide could enable threat actors to carry out massive DDoS campaigns targeting private organizations, governments, and critical infrastructure — capable of disrupting essential services or rendering them unreachable or unusable entirely.
What is a DDoS amplification attack?
During a DDoS amplification attack, a threat actor sends a request with the target’s source IP address to a vulnerable device. This lets data grow within the abused service, up to a maximum point. Then, it transmits a reply to the victim.
From BleepingComputer:
Usually, the size of a typical reply packet from an SLP server is between 48 and 350 bytes, so without manipulation, the amplification factor can reach up to 12x … However, by exploiting CVE-2023-29552, it’s possible to increase the server’s UDP response size by registering new services until the response buffer is full.
By successfully increasing the server’s UDP response size, attackers can achieve a maximum amplification factor simply by turning a normally tiny 29-byte request into a massive 65,000-byte response directed at a target of the attacker’s choosing.
How to protect your business
- Disable SLP on any internet-connected, publicly exposed systems.
- According to BleepingComputer, “It is recommended to configure a firewall that filters traffic on UDP and TCP port 427, which is the main entry for the malicious request that exploits SLP services.”
- VMWare has also published a bulletin on the matter, clarifying that the issue only impacts the platform’s older ESXi releases that are no longer supported, advising admins to avoid exposing them to untrusted networks.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“If everything which has been reported proves true, this situation poses a tremendous threat. Security professionals are encouraged to follow available guidance as appropriate and do so as quickly as possible.”
2. Google Ads pushes BumbleBee malware used by ransomware gangs
A recent Secureworks report highlights a new campaign where threat actors are using Google Ads to promote trojanized versions of installers for popular applications and deliver the BumbleBee malware loader to unsuspecting victims.
BumbleBee was most likely developed by the Conti team to replace the BazarLoader backdoor, in order to aid attackers in accessing networks and distributing ransomware and other secondary payloads. According to BleepingComputer, a new version of the malware loader was observed in the wild in September 2022 with a stealthier attack chain leveraging the PowerSploit framework and supporting DLL injection into memory.
Recent campaigns have seen the enterprise-targeting BumbleBee malware distributed through Google Ads, employing search engine optimization (SEO) poisoning to create promotions designed to appeal to users eager to facilitate the easy download of popular software, such as Zoom, Cisco AnyConnect, and Citrix Workspace.
Details on the BumbleBee malware attacks
According to Secureworks’ Counter Threat Unit (CTU), researchers observed BumbleBee malware being distributed via weaponized installers for popular software —not only in the platforms referenced above but also via infected installers for the much-hyped ChatGPT.
Targeting ChatGPT is likely an attempt by attackers to capitalize upon the widespread controversy and public interest surrounding OpenAI’s revolutionary AI chatbot.
CTU says as much in its report:
Trojanizing installers for software that is particularly topical (e.g., ChatGPT) or software commonly used by remote workers increases the likelihood of new infections.
Another campaign observed by researchers began with a Google advertisement promoting a fraudulent Cisco AnyConnect Secure Mobility Client download page, created on February 16 and hosted on the legitimate-looking domain, appcisco[.]com.
“An infection chain that began with a malicious Google Ad sent the user to this fake download page via a compromised WordPress site,” explains SecureWorks’ report.
The fake landing page prompts the user to download a trojanized MSI installer, called cisco-anyconnect-4_9_0195.msi, which installs the BumbleBee malware. Upon the malicious file’s execution, both a copy of the legitimate program installer and a malicious PowerShell script (cisco2.ps1) are copied to the victim’s device.
CiscoSetup.exe — the authentic installer for AnyConnect — installs the legitimate application on the user’s device to preemptively put to rest any suspicion on the part of the user. Unfortunately, the accompanying, appropriately named PowerShell script installs BumbleBee and begins its work carrying out malicious activity on the now-compromised system.
This includes the installation of an encoded BumbleBee malware payload, which is reflectively loaded into memory. Essentially, this means that BumbleBee is still leveraging the same post-exploitation framework module to load malware into memory – without setting off any alarm bells on the part of existing security solutions and antivirus products.
As Secureworks explains, CTU researchers discovered additional software packages with similarly named pairs of files, like ZoomInstaller.exe/zoom.ps1, ChatGPT.msi/chch.ps1, and CitrixWorkspaceApp.exe/Citrix.ps1.
Inherent ransomware threat
Because the observed attacks which thus far comprise this campaign have targeted corporate users — as well as the fact that BumbleBee has historically laid the groundwork for extortion operations — there is a high degree of possibility that devices infected during these attacks will be viewed by threat actors as prime candidates for jumping off points for ransomware deployments.
From BleepingComputer:
Secureworks examined one of the recent BumbleBee attacks closely. They found that the threat actor leveraged their access to the compromised system to move laterally in the network approximately three hours after the initial infection… The tools the attackers deployed on the breached environment include the Cobalt Strike pen-test suite, the AnyDesk and DameWare remote access tools, network scanning utilities, an AD database dumper, and a Kerberos credentials stealer.
Based on previous reporting, the attack profile at play here seems to indicate that the malware’s operators are looking to secure reliable network access points from which they may pivot to other systems, exfiltrate sensitive information, and ultimately deploy ransomware — or at the very least, attempt to extort the corporate organizations to which the compromised enterprise environments belong.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“As BleepingComputer explains, ‘using malicious Google Ads or SEO poisoning to distribute malware has become a common tactic for cybercriminals. For example, in the Report, Counter Threat Unit™ (CTU) researchers described legitimate web searches being hijacked by SEO poisoning to infect victims’ systems with Gootloader, and malicious Google Ads bundling infostealers like RedLine in trojanized installers for messaging apps such as Signal.’”
“Such tactics mark a significant shift from BumbleBee’s traditional methods of distribution, which primarily consisted of phishing campaigns deployed in aid of ransomware deployments. In terms of stealth and its ability to evade defensive measures and antivirus solutions, BumbleBee outshines many of its peers, such as BazarLoader.”
3. Chinese hackers use new Linux malware variants for espionage
Palo Alto’s Unit 42 recently exposed a new variant of the PingPull malware designed to target Linux systems.
The malware is historically used by Chinese threat actor Alloy Taurus, also known as Gallium. Palo Alto also uncovered a previously undocumented backdoor during their research known as Sword2033.
Also known as Gallium, Alloy Taurus is a Chinese state-sponsored cyberespionage group that has been active since at least 2012. The group has historically targeted telecommunications companies, financial institutions, and government entities across Asia, Europe, and Africa.
Last year, the group was seen leveraging a remote access trojan named PingPull. During this time Palo Alto identified several connections between Alloy Taurus infrastructure and targeted entities across Afghanistan, Australia, Belgium, Cambodia, Malaysia, Mozambique, the Philippines, Russia, and Vietnam. Details on the previous Windows variant of PingPull can be found here.
The PingPull Linux variant
On March 7, 2023, a PingPull Linux variant was uploaded to VirusTotal. At the time of Palo Alto’s report, only three out of 62 vendors found this sample to be malicious. Despite many vendors finding this sample benign, additional analysis confirmed this sample to be a Linux variant of PingPull malware. This determination was made based on matching HTTP communication structure, POST parameters, AES key, and command-and-control (C2) commands.
- Upon execution, this sample is configured to communicate with the domain, yrhsywu2009[.]zapto[.]org, over port 8443 for C2. It leverages a statically linked OpenSSL library to interact with this domain over HTTPS.
- The payload then expects the C2 server to respond with data that is Base64 encoded and encrypted with AES with a specific key. This key is the same key observed in the original Windows PE variant of PingPull.
- Once decoded, the cleartext resembles HTTP parameters. One of the parameters will contain a single upper-case character between A and K as well as M, which the payload uses as the command value.
- After running the command, the payload sends the results back to the C2 server via an HTTPS request resembling the beacon request, but with Base64 encoded ciphertext. The command handler supports the following functionality (which aligns with both China Chopper capabilities and those of the original Windows PE PingPull variant):
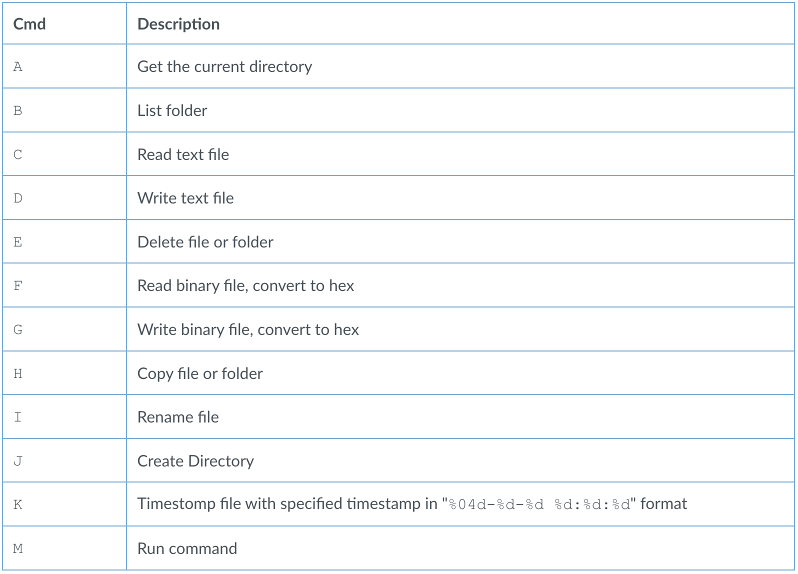
Figure 1 PingPull command handler functionality. Image courtesy of Palo Alto.
An overview of the Sword2033 backdoor
Palo Alto pivoted on the C2 domain and identified one additional sample communicating with the same domain.
Like the new Linux PingPull variant, this sample was designed to connect to port 8443 over HTTPS. However, this sample is a rather simple backdoor, tracked now as Sword2033.
This backdoor supports three basic functions, as seen in Fig. 2:
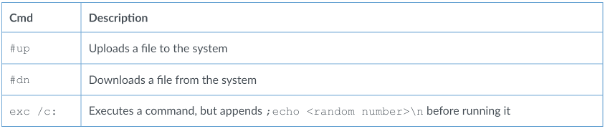
Figure 2 Sword2033 command handler functionality. Image courtesy of Palo Alto.
- These three commands map to commands in a second command handler that uses A, C, D, and M commands that are identical in value and functionality to the PingPull commands outlined previously.
- Searching for other Sword2033 samples led Palo Alto to a second sample. This second sample was observed in July 2022 and is configured to connect to 196[.]216[.]136[.]139, located in South Africa, for its C2 operations.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“Alloy Taurus is clearly continuing to refine and update its arsenal and has increased its range of targeting with a new Linux variant of PingPull and the new Sword2033 backdoor. The similarities in the command handlers used in the new PingPull variant with those used in the notorious China Chopper web shell, while concerning, is not a total surprise given how common it is for Chinese threat actors to share tooling.”
Do you have insight into these stories that you want to share? Head over to Tanium’s discussion forum to start a conversation.
For further reading, catch up on our recent cyber threat intelligence roundups.




