How Enterprise Is Facing Up to Ransomware
A new survey shows which industries are winning, and which are losing, the ransomware showdown, and how best to fight back.
The ongoing ransomware attacks against enterprises large and small have brought a wave of unwanted disruption, publicity, and costly payouts around the world. Headline-making ransomware hacks against companies like JBS, Colonial Pipeline, and software manager Kaseya, are only the tip of the ransomware iceberg.
In fact, more than a third of organizations recently surveyed by IDC, say that in the past 12 months a ransomware attack has blocked access to their systems or data. While U.S. organizations have experienced an incident rate of only 7%, American companies are far more concerned about these cyber assaults than their global peers.
It’s easy to see why: The Colonial attack shut down the company’s East Coast fuel supply for six days, while the supply chain breach of US-based Kaseya affected some 1,500 businesses worldwide.
The payout costs alone can be staggering. In the past year, the average ransomware payment was almost $250,000, according to IDC’s survey. Of course, large payouts skew that figure. Colonial paid $4.4 million and JBS forked out $11 million. The median ransomware payout is actually about $75,000. But that’s nothing compared to the cost of reputation and the loss of consumer trust.
IDC’s survey, released in July 2021, queried 791 IT decision-makers and influencers at midsize to large enterprises in the U.S., Europe, and the Asia-Pacific region. For a data-driven look at the ransomware threat, who’s most at risk (spoiler alert: it’s digital-transformation laggards), and how large and medium-size enterprises are facing the challenge, please check out the seven charts below, which summarize the survey’s key findings.
Now and then
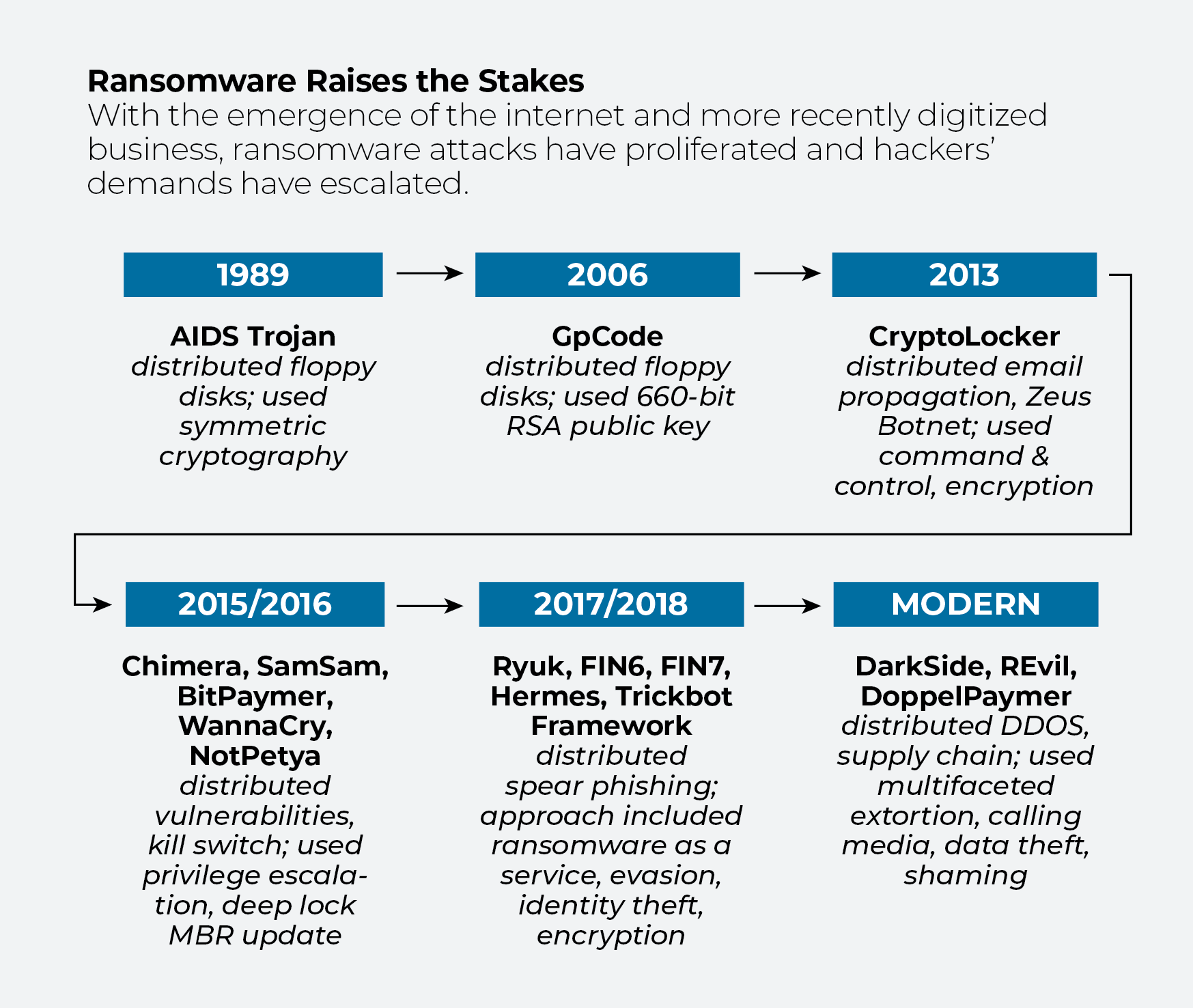
What a difference a decade makes. Or three.
IDC took a look back at ransomware’s past, starting with AIDS Trojan—the world’s first ransomware attack—which was delivered on floppy disks to medical researchers in 1989. They found that ransomware has become more sophisticated, is harder to neutralize, and in recent years has significantly upped its game.
Compared with modern-day cyber extortion tactics, organizations subject to the AIDS Trojan attack got off relatively lightly. In many cases, security teams were able to restore encrypted files and avoid payouts. And as recently as 2006, ransomware was still pretty much small potatoes. GpCode, the malware that encrypted files on Windows machines, elicited payouts of just $100 to $200. By 2015, the stakes had raised. Criminal innovations like “privilege escalation” (a way of working up through a system to gain access to more sensitive data) were generating ransoms of $40,000 to $60,000.
Today, groups like DarkSide, REvil and DoppelPaymer work on multiple fronts, not only encrypting or blocking access to files, but also threatening to sell stolen data to the highest bidder or shame a company and its clients by publishing sensitive data or revealing it to the media. Remote working and the digitization of business have aided their cause, and ransoms have skyrocketed into the millions.
Facing up to ransomware
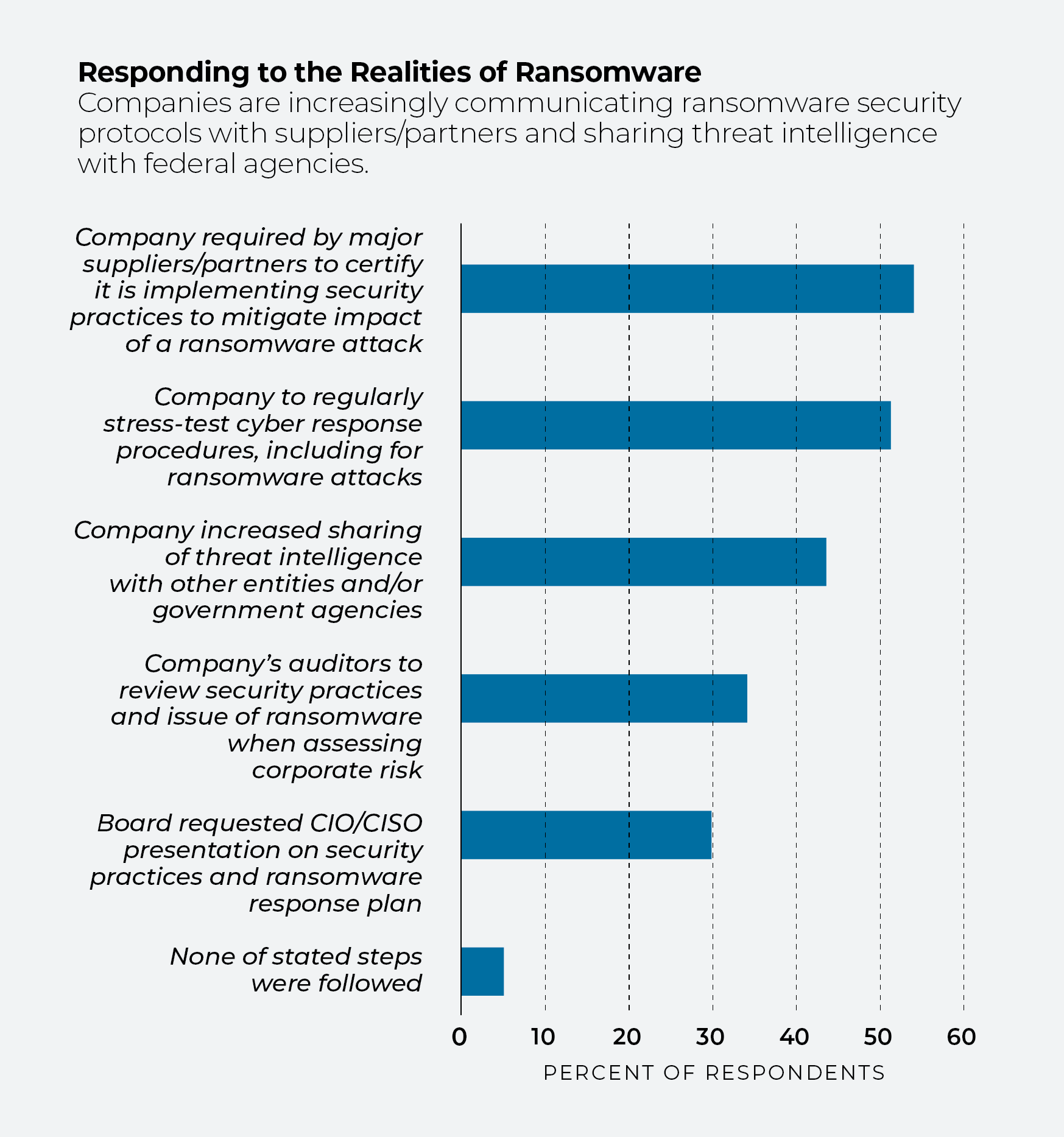
Ransomware is no longer only an internal matter. More than half of those surveyed by IDC acknowledged that major suppliers or partners had in the past year required them to certify they had implemented and maintained data protection and recovery practices to prevent business disruptions from cyberattacks.
[Read also: Ransomware 101: What is it and how do I prevent an attack?]
More than 40% reported their security teams had increased sharing of threat intelligence with government agencies and other groups. In nearly a third of companies, the board of directors had required their CIOs or CISOs to deliver cybersecurity presentations, addressing data protection and recovery practices and incident response procedures.
Ransom demands
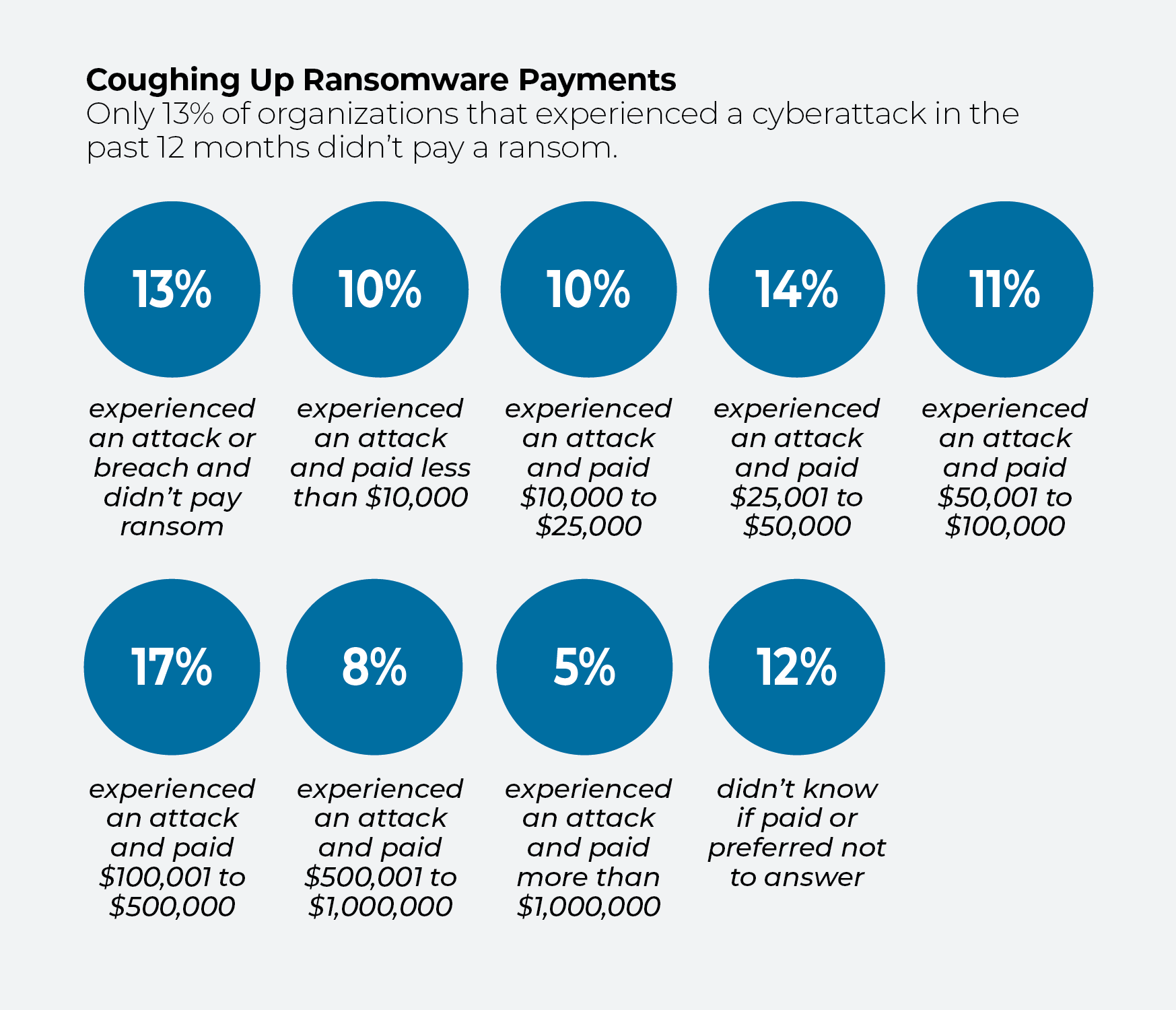
When targeted by ransomware, most organizations pay, but the amount varies: 10% of respondents paid less than $10,000; 35% paid $10,000 to $100,000; 25% paid $100,001 to $1 million; and 5% paid more than that. Only 13% experienced a cyberbreach that blocked access and refused to pay a ransom, according to IDC.
While the FBI doesn’t recommend paying a ransom, so as not to encourage cybercriminals, a top official urged Congress in July not to make such payments illegal: Bryan A. Vorndran, assistant director of the FBI’s Cyber Division, told a Senate Judiciary Committee hearing that banning ransom payments would put U.S. companies in the position of facing additional extortion. Hackers could blackmail them for paying a ransom and not sharing that information with authorities, he said.
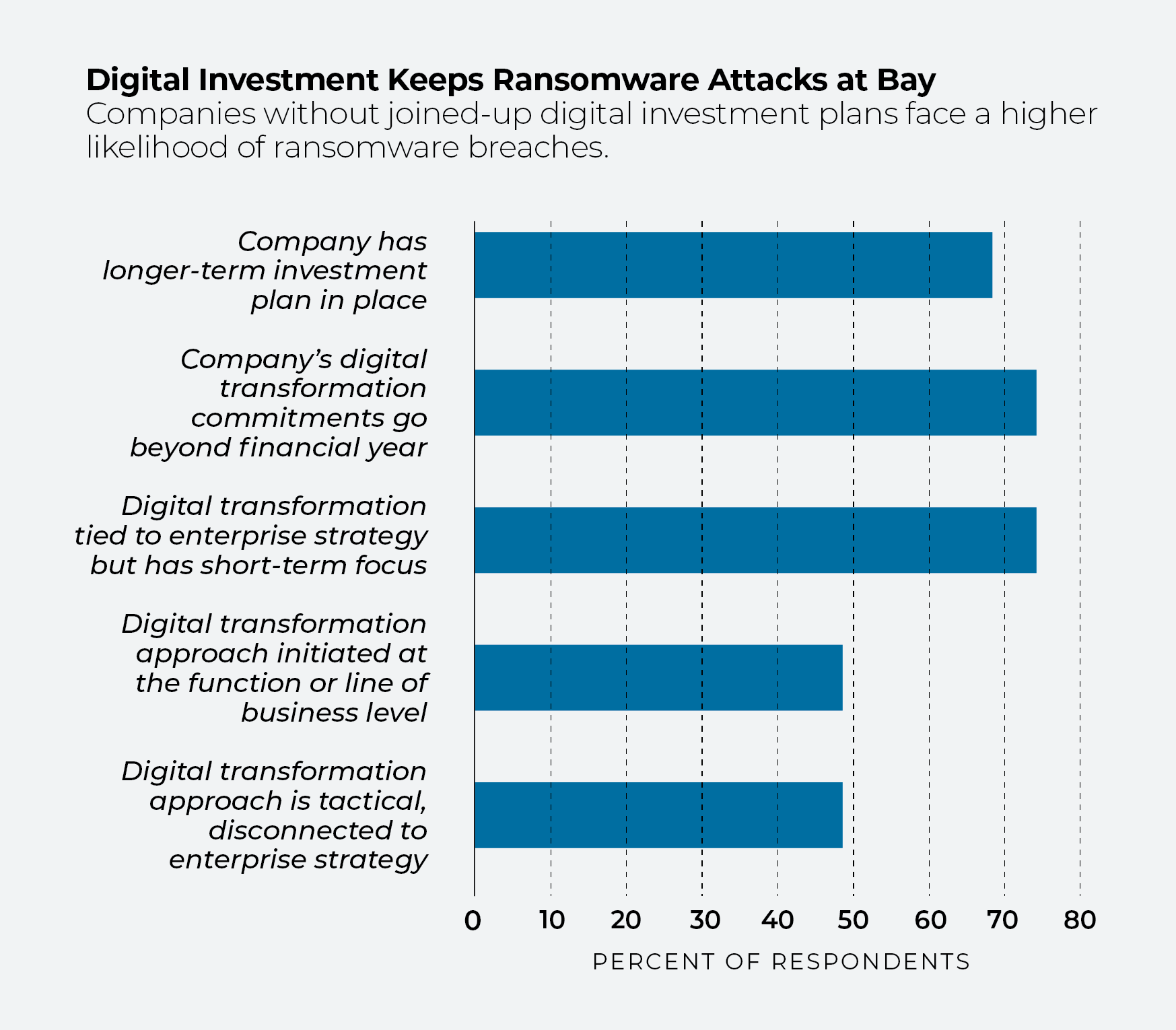
Digital laggards at higher risk
Organizations that had no ransomware attacks in the past year share something in common: a strong commitment to digital transformation. About seven in 10 have a longer-term investment plan in place, or a plan that at least goes beyond the current financial year or is tied to enterprise strategy.
Digital transformation inevitably means a review of cybersecurity. Whether you are a retailer embracing e-commerce, a healthcare provider adopting telemedicine, or a financial company partnering with a technology platform, your enterprise network will be transformed, especially if a chunk of operations is migrated to the cloud.
[Read also: How the cloud can be efficient and safer for regulated industries]
At a minimum, legacy security tools will need to be updated. Savvier players will see an opportunity to scale up security with the adoption of endpoint management tools, which proactively monitor networks for signs of intrusion.
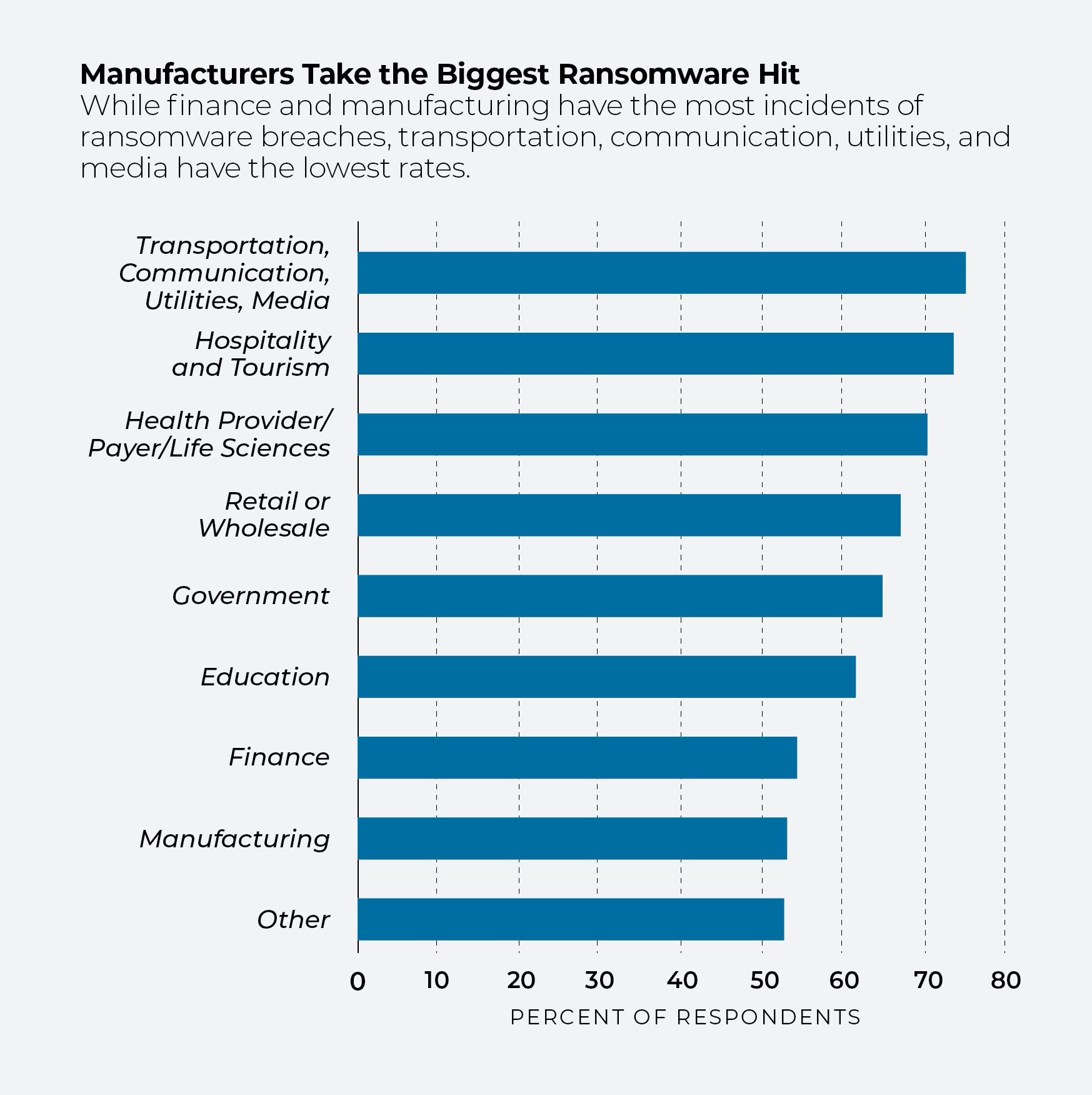
Sector disruption
Only about 50% of manufacturers were unharmed by ransomware in the past 12 months, according to IDC, compared with some 75% of transportation, communications, utilities, and media firms. Hospitality and tourism also fared well (almost 75% avoided an attack) as did healthcare providers, health plan administrators and the life sciences (about 70%).
It’s not just a company’s behavior that influences its security defenses. The type of industry is also key. Financial services and healthcare firms, because of regulator requirements, may be more cognizant of cyber risk than industries like manufacturing. By the same token, companies may find themselves exposed to new cyber risks because of advancements in their fields. Telemedicine augmented by artificial intelligence, for example, can spur healthcare into new markets, and that can throw up opportunities for hackers.
[Read also: 4 industries that are ready for what’s next]
Ultimately, all industries are on notice. As telecommuting continues to entrench itself in the work space, so the number of remote endpoints and the intruder attack space will continue to increase.
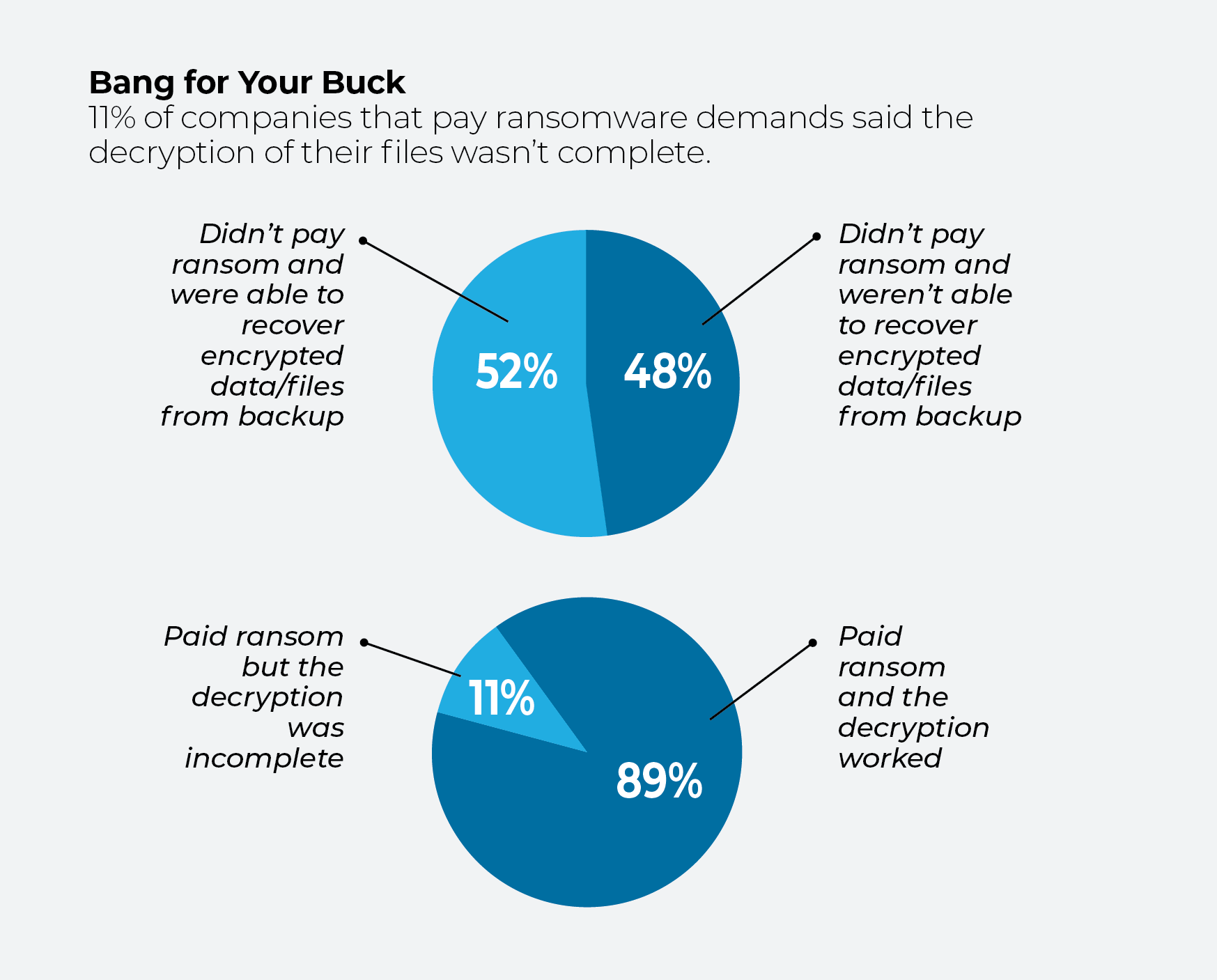
How to respond to ransomware demands
Despite the tendency to frown on ransom payouts, the benefits of paying can, in the short term, outweigh a strategy of playing hardball. Of those organizations that suffered a ransomware incident in the past year, not paying gave roughly 50-50 odds of a satisfactory outcome: 48% of those who didn’t pay a ransom were unable to recover encrypted data or files from backup while 52% managed to do so.
[Read also: Don’t be a cyberwar victim—become digitally resilient]
Of those that paid a ransom, 89% reported a successful decryption, and the remainder found the decryption incomplete.
Attack aftermath
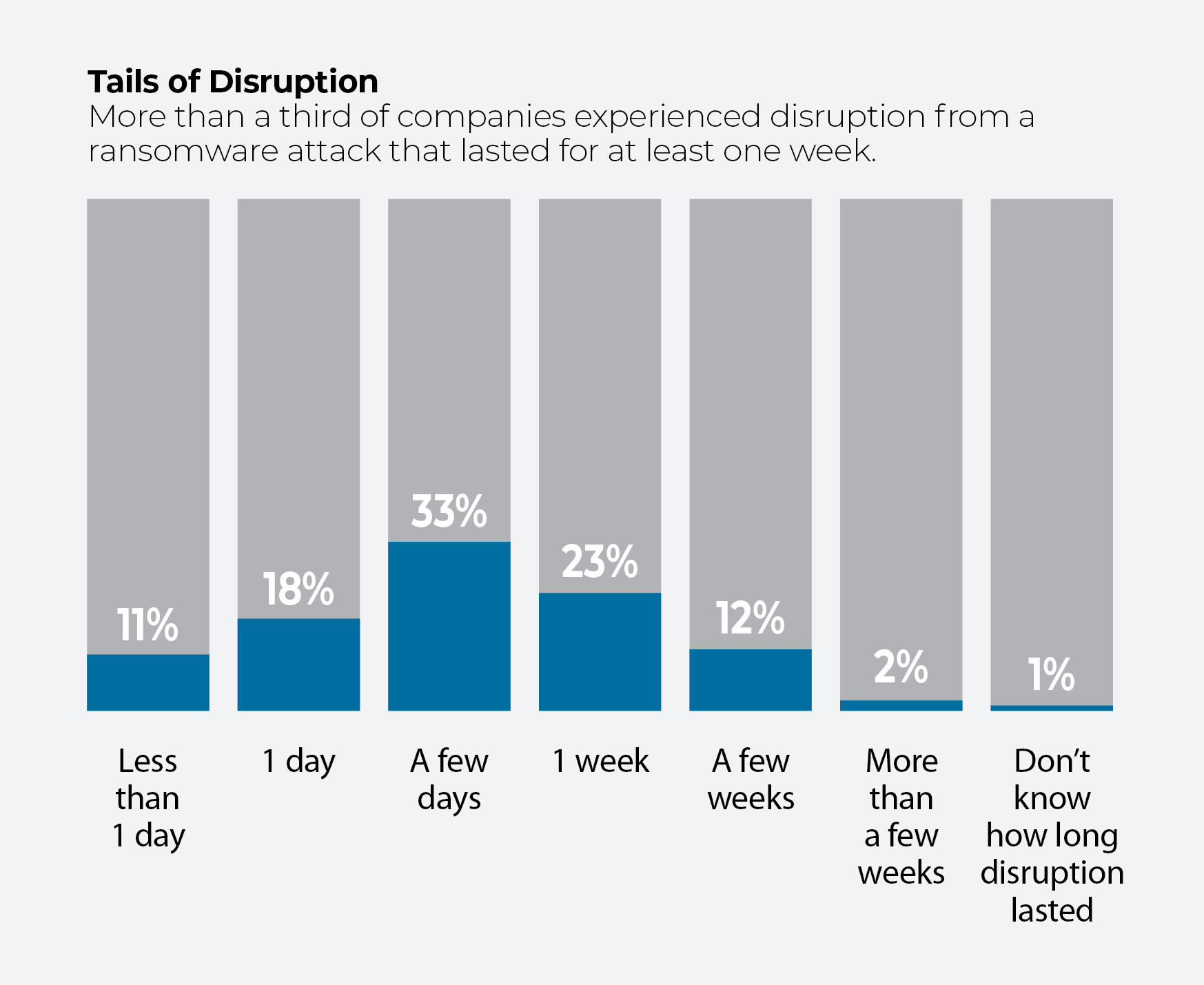
For most businesses, the biggest concern over a breach—besides the question of whether to pay or not to pay a ransom—is one of duration: Just how long will a ransomware assault disrupt normal operations?
The good news, relatively speaking, is that most survey respondents (62%) reported less than a week of disrupted work after a breach, while a third said an attack interfered with operations for a few days. Only 2% of firms reported trouble lasting more than a few weeks, while 11% saw less than a day’s disturbance.