How To Turn Your Remote Workers Into Security Advocates
Getting employees to participate requires awareness and that they have their own positive security experiences.
Big hacks get all the attention. This past summer, it was Barack Obama, Joe Biden, Elon Musk and Bill Gates. Hackers seized control of their Twitter accounts and ended up netting more than $100,000 in a scam, by posing as these public figures and soliciting money from other Twitter users.
Peel back the headlines on this high-tech heist and it turns out to be a very old-school con. One of the hackers allegedly used social engineering to trick a worker in Twitter’s IT department into handing over the login credentials to access the company’s master customer service portal.
Such social engineering attacks take advantage of human gullibility. Like scenes from an Ocean’s movie, hackers ask enough unsuspecting employees for help, requiring them to share sensitive company information. It’s a numbers game. The odds are that someone will eventually comply.
That’s partly why nearly 55% of business leaders in a recent survey said they see employees as their biggest security threat — even more than hackers themselves (29%) and far more than malicious insiders (20%). These aren’t trivial statistics. Companies know employees can be careless, easily fooled, and occasionally hostile. It’s an increasingly difficult problem, especially in the COVID-19 era, and many — if not most — organizations don’t know how to overcome it.
With a third of U.S. workers still working remotely, and with cyberattacks and probes up dramatically, experts say the most effective way to keep organizations safe is to address employee risk by involving them in cybersecurity efforts—converting them into campaigners for the cause.
“That has to be the starting point,” says Lance Spitzner, a director and cybersecurity trainer for the SANS Institute in Chicago. “Determine what human behaviors and risks you need to manage, and then pinpoint which ones to prioritize.”
It won’t be easy. It takes a cultural commitment to create change and incite executives from the boardroom to the field offices to show their willingness to participate. It takes investment in the tools and technology to empower employees to do better. And it takes a certain kind of training. Not the constant drumbeat of security lecturing or boring forced-participation training classes. It takes gamified security training that keeps workers engaged and includes them in the process.
Determine what human behaviors and risks you need to manage and then pinpoint which ones to prioritize.
“You also need to dedicate a full-time manager to run cybersecurity awareness and training,” says Spitzner. “Someone who is a good communicator and likes working with people. You need a person who can make complicated subject matter approachable for all.”
After devising a solid plan and appointing a strong leader and team to execute it, experts advise concentrating on three key areas: creating a cybersecurity culture; driving training and awareness; and generating employee engagement through better cybersecurity experiences.
Create security champions
With a cybersecurity culture in place, curbing human risk tends to progress more naturally. Indeed, security awareness and behaviors quickly become a seamless part of daily operations.
Spitzner says one of the most important, but least practiced, habits organizations need to adopt is to constantly train and drive awareness. They should try to achieve a steady drumbeat of activity to promote good cybersecurity hygiene. Mixing it up can help: More active and successful organizations intersperse educational programs with creative campaigns, he says.
For instance, the security training team at one multinational beverage maker works with the company’s regional communications, marketing and sales leads to customize cybersecurity narratives aligned to local needs. These include cultural practices and cybersecurity incidents. So if a particular region had a spate of phishing attacks trying to fool employees into clicking on links related to an approaching cultural holiday, the security awareness team might spend extra time delivering digital communications to help employees recognize and head off such attacks.
In addition, the beverage company anoints “champions” (or employee advocates) in each territory to encourage its nearly 30,000 global employees to participate in cybersecurity programs. Champions, say security experts like Spitzner, tend to be one of the more cost-effective tools in a company’s belt, and they wield considerable credibility with co-workers. These include security training and awareness campaigns built around fun activities, such as virtual games and challenges where employees might take a quiz on cybersecurity best practices for the chance to win a modest prize. The beverage company found that adding prizes of its own products resulted in an exponential increase in the number of responses to the game.
At Switzerland’s largest insurer, Zurich Insurance Group, Janet Roberts is global head of the company’s security education and awareness program. She likewise treats her workers to a steady diet of gamification exercises, online learning, tips and short interactive videos. It’s been a success because Roberts’ team doesn’t overdo it. They serve up information in quick, bite-size morsels instead of forcing people to endure hour-long training sessions.
“People skim information; they don’t always take the time to fully read it,” Roberts says. “That’s even more true now because more people are working remotely and have kids, dogs and all of these other distractions. So you have to figure that you have 30 seconds to a minute to get a concept across to them. You can’t think that just because they’re sitting at home they have all sorts of time. Your information must be quick and easy for them to consume.”
Then train again
Too many organizations do the opposite: They overwhelm employees with technical and inconsequential information. “One of the most common mistakes security professionals make is flooding employees with information,” says Spitzner. “Workers already find security confusing, intimidating and scary. So at some point, the employee just gives up, decides they don’t care or stops listening. The reality of our jobs is that we have to make security as simple as possible.”
To do that he suggests focused and digestible snippets of information on key and impactful topics rather than boiling the ocean. A training micro-video, for example, on how to counter the rising threat of ransomware. Or a fun quiz on ways to spot an advanced phishing attempt.
We patch computers every month. We also need to patch people to keep their cyber security interest and habits up-to-date.
“The key thing to remember is you want to do these things continuously throughout the year,” he says. “Don’t teach them once and forget about them. We patch computers every month. We also need to patch people to keep their cybersecurity interest and habits up-to-date.”
Engage through experience
Another way to keep employees engaged in cybersecurity is to make it a positive, rather than negative, experience. Frank Dickson, a cybersecurity analyst with IDC, says many companies still take an authoritarian approach to cybersecurity. They lay down the law about policy and procedure. They stress that violators might be punished or even terminated. That only creates an adversarial relationship with workers who, these days, have enough stress on their plates.
“Some companies just whack people with a stick where, if they do something wrong, they might be forced to take a two-hour training course about ransomware or they’re sent spam warnings every day reminding them not to repeat such behavior,” Dickson says. “The thing companies should keep in mind is that they are creating adversarial relationships with people who might be frontline workers and have a direct impact on revenues. Ticking them off isn’t the way to go.”
Roberts agrees. “We train and educate to raise awareness, to help employees learn so they feel confident to be an ambassador for the company and to be security champions for us,” she says. “We want them to participate and not be afraid of what we’re doing.”
One way to encourage participation, Dickson notes, is to empower employees with devices that will provide them with rich user experiences — whether laptops, smartphones, tablets, PCs or printers. Trying to save $200 on a company-issued laptop that is too small for daily use only encourages employees to use their personal devices, bypassing corporate security measures.
Such attention to user experience, says Dickson, should not be an afterthought, as it is at many companies. If employers want employees to perform their work securely, companies should securely enable them with devices and apps that also make them more productive, he says.
Similarly, companies can provide employees easy, secure access to their corporate networks. While usernames and passwords haven’t been effective security mechanisms for years, companies still cling to them, requiring employees to update them every 90 days. In the meantime, virtual private networks (VPNs) continue to befuddle and frustrate workers. They are the second most frequent reason (after password retrieval) that remote employees seek IT support, Dickson says.
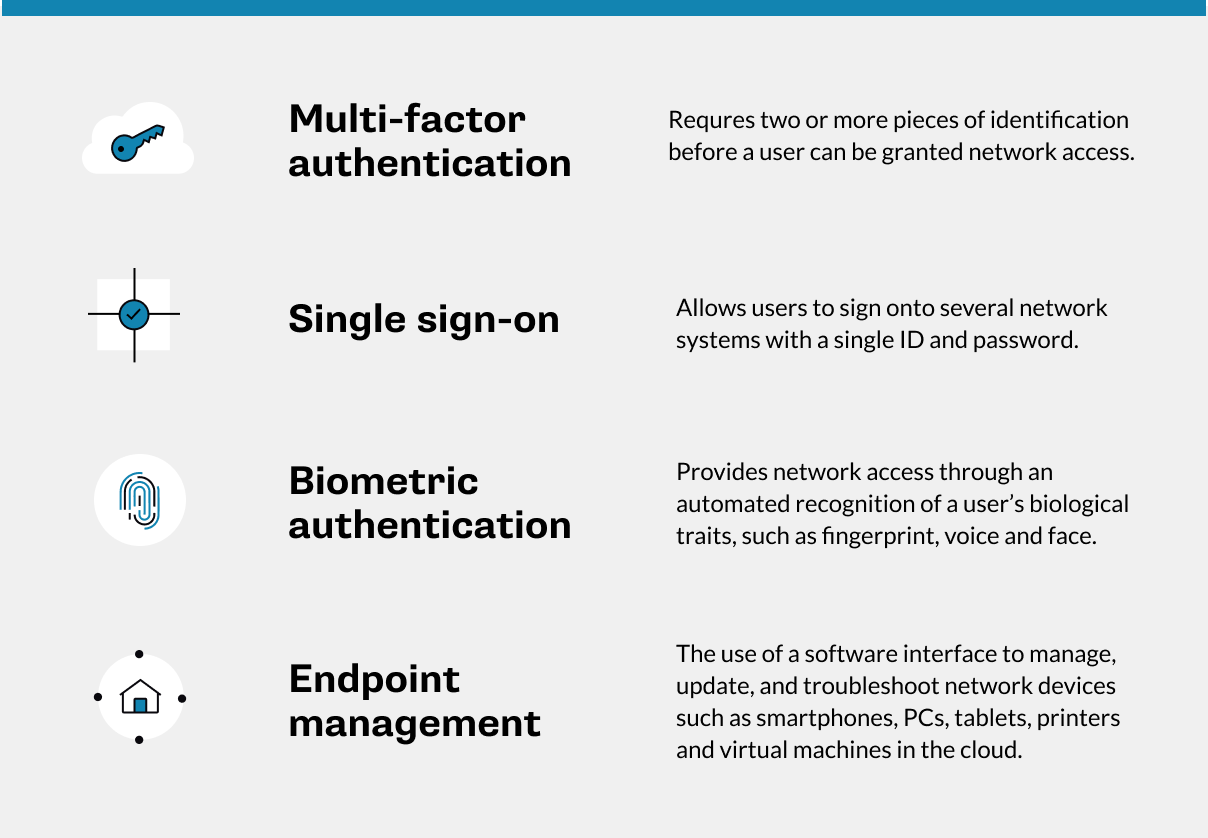
There are better alternatives to consider for making cybersecurity less obtrusive, he notes. These include multifactor authentication, single sign-on, password-less biometric authentication and endpoint management solutions.
“If you truly want to engage employees and turn them into your cybersecurity advocates, you need to make sure they see the benefit for them,” Dickson says. “The way you do that is by making sure they always have a positive user experience so they will want to participate.”








