Info-stealing Malware in Software Supply Chains: Cyber Threat Intelligence Roundup
Info-stealing malware in software supply chains and key findings from KELA’s latest cybercrime prevention report
First, we dive into a report detailing multiple fraudulent Python packages within the PyPI registry, which researchers claim are distributing info-stealing malware. Next, we investigate KELA’s latest report, which contains a multitude of findings relating to activity associated with top-ranking ransomware as well as an overview of stolen credential sales figures gathered from initial access brokers (IABs) over the past quarter.
1. Dozens of PyPI packages caught dropping W4SP info-stealing malware
A new report from software supply-chain security firm Phylum reveals the existence of multiple Python packages within the PyPI registry which researchers claim are distributing info-stealing malware (the W4SP info-stealer in particular is being dropped on compromised machines via obfuscated malicious code injected within these packages).
Researchers have discovered 29 packages in the #Python Package Index (PyPI) repository that aim to infect developers’ machines with a #malware called W4SP Stealer.
Read: https://t.co/jgCZPawWyE#infosec #cybersecurity #hacking
— The Hacker News (@TheHackersNews) November 5, 2022
Phylum’s automated risk detection platform alerted its analysts to suspicious activity emanating from dozens of newly published PyPI packages. Its researchers characterize the activity as a sophisticated attempt to deliver the W4SP info-stealer to machines belonging to Python developers.
According to Phylum, this attack begins with the unnamed threat actor copying existing popular libraries and injecting the otherwise benign packages’ codebase with a malicious __import__ statement.
By copying existing authentic packages, the actor can benefit from each package’s accompanying PyPI landing page (generated by its setup.py and including the original packages’ README.md), the result of which is a real-looking landing page, complete with working links, lending a significant sense of legitimacy to the proceedings.
From Phylum: “Here’s the PyPI landing page for the malicious package typesutil. You can see the attacker just copied the datetime2 package and made a few slight modifications in an effort to make the text consistent with the phony package name it was published under.”
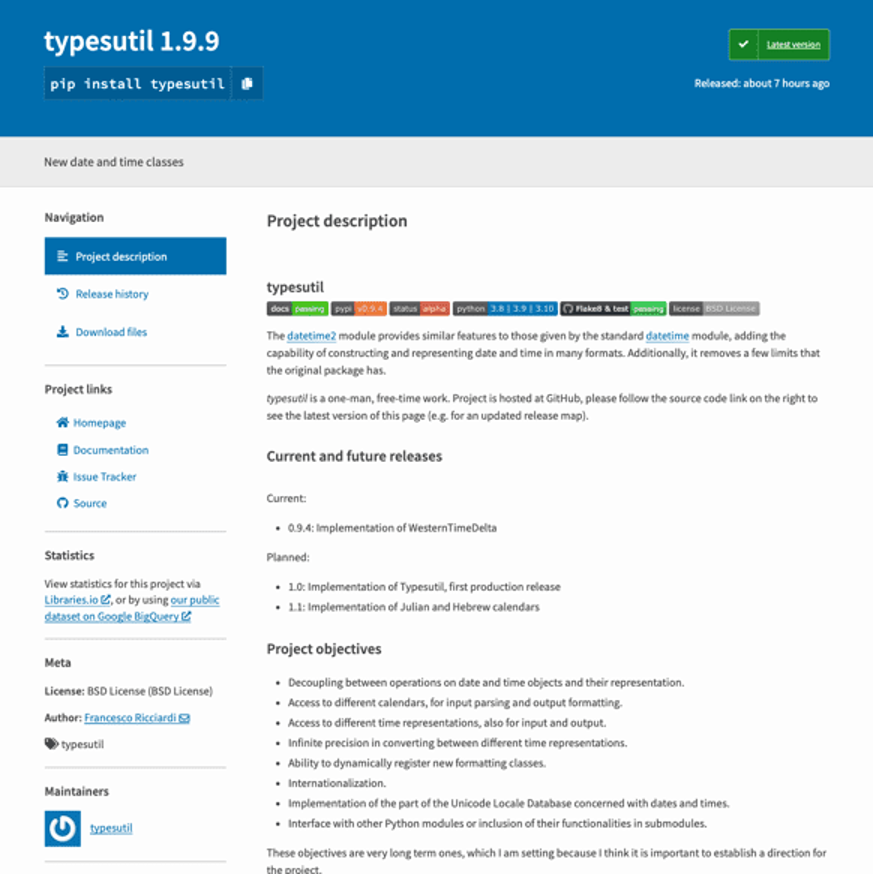
Image Courtesy of Phylum
The attacks appear to have begun somewhere around October 1, 2022, gradually gaining momentum and becoming worthy of being categorized as a concentrated adversarial campaign around October 22, 2022. However, Phylum concedes to having observed a small number of packages containing similar indicators of compromise (IOCs), published in July 2022.
The working theory is that this earlier activity was likely a proof-of-concept (PoC) test, allowing the attackers to test their methodology. What we’re seeing now could very well be the result of those exploratory efforts.
Evolution of adversarial tactics
When analyzing the packages which represent the culmination of this threat actor’s efforts (the earlier ones in particular), it became clear to researchers that the lion’s share of them was simply compromised by injecting the malicious __import__ statement referenced above into either the setup.py or the __init__.py. This proved to be a somewhat ham-fisted solution and dumping the import in rather obvious, easily found locations resulted in many of the actor’s attempts being detected and taken down.
This prompted the attacker to switch up tactics. Instead of simply dumping the import in an easy-to-find spot within the targeted packages, the import began to be deliberately placed far offscreen; which the adversary accomplished by leveraging Python’s seldomly-used semicolon to place the malicious code alongside legitimate code on the same lines (see below for a screengrab of setup.py taken from the malicious package typesutil).
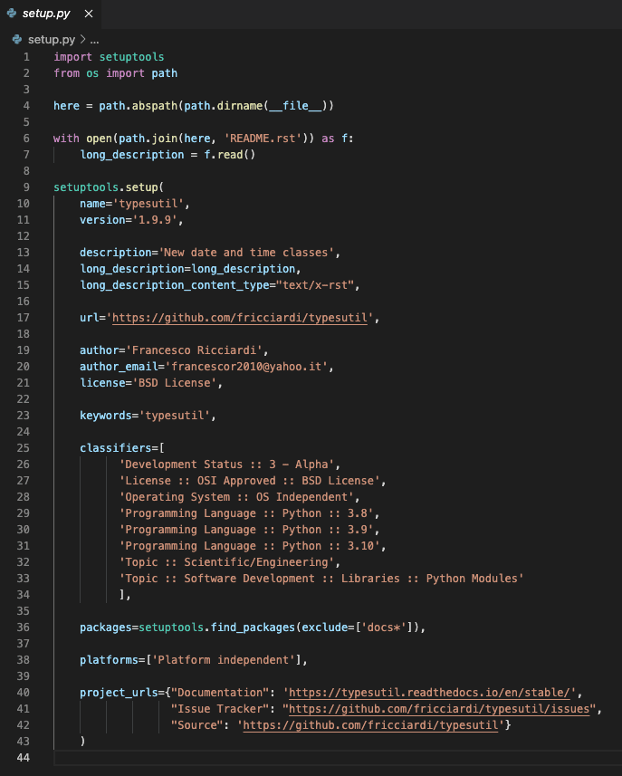
Image Courtesy of Phylum
At first, nothing looks out of order. It’s only when one widens their code editor window (or enables word wrapping) that the ruse is exposed, and __import__ is suddenly visible, way out in left field — offset by 318 spaces (see below).
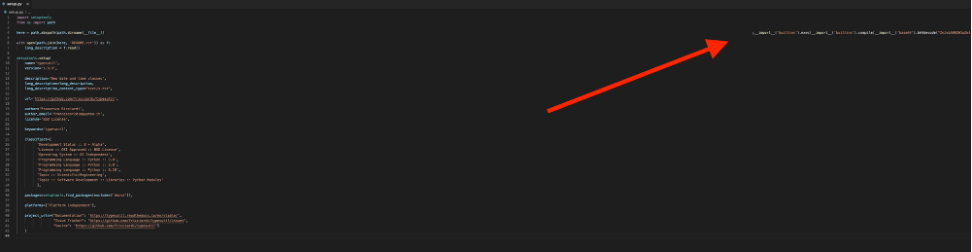
Image Courtesy of Phylum
In many instances, a second or two of carelessness or inattention to detail on the part of the developer is all it takes to leverage a malicious package in place of its legitimate counterpart, thus unwittingly kicking off a potential software supply chain incident.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“Taking into account that software supply chain security is a hot-button topic right now, along with the constant stream of risks facing the open-source software industry, stories such as this should be taken seriously. That said, there is a big difference between taking a threat seriously and acting accordingly in a calm, measured manner – and allowing a potential threat to create chaos and dictate your every movement.”
“The takeaway here is that incidents like Heartbleed and the highly impactful SolarWinds compromise made an indelible mark on the cyber threat landscape, and things will likely never be the same. Is this a good thing? Was the threat landscape ever normal or stable? It’s a highly subjective question, and one I’m not going to try and answer. However, the current consensus among intelligence experts is that the cyber domain has reached a point of instability not previously observed by most sources upon which we depend for information.”
“Still, there are many benefits to working with open-source platforms. And it’s important to cultivate a healthy skepticism regarding the ability of a huge number of projects to implement security consistently and reliably as a feature, versus an afterthought.”
“The PyPI story referenced above is just the latest in a long line of examples of threat actors attempting to compromise the packages, libraries, and projects upon which developers have relied for years to simplify their work, some of whom may take the integrity and authenticity of the resources they are importing for granted.”
“The reality is, open-source software wouldn’t receive so much attention from our adversaries if it weren’t such an attractive, highly successful vehicle for the delivery of malicious payloads or the accomplishment of other malicious goals.”
2. KELA report details ransomware activity and network access sales for the third quarter of 2022
KELA’s recently released “Ransomware Victims and Network Access Sales in Q3 2022” report contains a multitude of findings related to top ransomware activity and initial-access-broker (IAB)-generated sales for the past quarter of 2022.
The report places an emphasis on the fact that threat actors offered more expensive initial access offerings this quarter – a likely indication that demand for access points and stolen credentials is increasing.
KELA’s ransomware findings
In Q3 2022, KELA identified around 600 victims in its sources, including ransomware actors’ blogs/portals, data leak sites, and public reports. On average, KELA observed about 200 attacks each month for Q3 compared to 216 for Q2.
Top ransomware groups
The most prolific ransomware groups for Q3 were LockBit, Black Basta, Hive, Alphv/BlackCat, and BianLian.
- LockBit: LockBit had over 200 victims, which is four times more than its closest rivals had and held its position at the top of the list.
- Black Basta: Black Basta’s activity remained steady between Q2 and Q3 with 50 victims in each.
- Hive: Hive appears to have greatly increased its activity compared to Q2 by roughly 67%.
- Alphv/BlackCat: This operation’s activity decreased by about 28% from Q2 to Q3.
- BianLian: BianLian is a relatively new ransomware group that quickly worked its way up into the top five for this month.
Top ransomware sectors
According to KELA the sector most targeted by ransomware for this quarter was professional services. LockBit, Hive, and Alphv were responsible for about half of the attacks in this sector. The next most targeted sectors were manufacturing and industrial products, and healthcare.
Top ransomware countries
The U.S. appears to be the most targeted country for this quarter, with 40% of KELAs observed attacks impacting U.S. companies. Following the U.S. is the U.K., France, Germany, and Spain.
Network access sales
For Q3 KELA traced over 570 network access listings for sale, with a cumulative requested price of about $4 million, though one access was offered for $3 million itself. This number is a significant increase compared to the roughly $660,000 demanded in Q2. However, excluding the single $3 million outlier, the difference would not be nearly as vast.
Excluding this offering, the average price for access was around $2,800 for Q3 compared to $1,500 for Q2. The median price reflects a more significant change from $300 in Q2 to $1350 in Q3. This increase shows that actors offered more expensive listings in general for this quarter.
Initial access broker findings
About 110 actors were engaged in selling network accesses, which is not far off from the number of actors in the previous quarter.
Top initial access brokers
Each of the top three IABs offered anywhere from 40-100 accesses for sale.
- R1z: This actor joined the cybercrime forums in 2019 but only started selling network access in July 2022. The actor tends to sell remote code execution vulnerabilities and posted around 100 listings for Q3.
- Salvador_Dali: This actor has been an IAB since May 2022 and targets mainly US-based companies. This actor does not typically specify the access type or price.
- Orangecake: This actor has been active since September 2021 and usually offers VPN-RDP access for sale. This actor has demonstrated a high reputation on forums and was even seen collaborating with various ransomware groups.
Top IAB-targeted countries and sectors
The U.S. was the most targeted country by IABs, just as it was in Q2, claiming 30% of the total number of victims. The US is followed by the UK, Canada, and India. The professional services sector was the vertical most targeted by IABs, followed by manufacturing & industrial products, and the technology sector.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
“It’s important to remember that it would be impossible for a company to collect information on every single cyberattack across the globe for a given timeframe, especially considering how many might go unreported or unattributed. It’s also necessary to take this data with a grain of salt, as CTI cannot confirm it is fully comprehensive.”
“CTI has reported on all the operations that KELA has listed in its top ransomware groups and has also heavily reported on IABs over the past few months which aligns quite nicely to was KELA has reported. What might be most noteworthy to pull from this data is the fact that the threat actors are offering network access at a much higher price compared to last quarter. Could it be that cybercriminals are willing to pay a higher amount to enter the market? Or are the IABs just getting greedier with their offerings?”
Do you have insight into these stories that you want to share? Head over to Tanium’s discussion forum to start a conversation.
For further reading, catch up on our recent cyber threat intelligence roundups.




