7 Ways to Minimize Data Risk and Enhance Privacy Compliance
Rapidly evolving compliance regulations, escalating financial penalties and more rigorous enforcement are the name of the game for GRC leaders
Change is the new reality for today’s information and governance, risk management and compliance (GRC) leaders. Rapidly evolving compliance regulations, escalating financial penalties and more rigorous enforcement are the name of the game.
This new environment is being developed partly in response to the digital transformation of modern organizations. But the growing complexity of technology systems, in turn, makes compliance increasingly challenging.
For example, First American was charged by New York state regulators for exposing hundreds of millions of customer documents containing personally identifiable information (PII) for more than 15 years. This major privacy incident was caused by a basic design error on its website.
This incident shows that organizations are under increasing pressure to understand what sensitive data they have, where it is and how it is being secured. But this is just one piece of the puzzle.
How to improve your data risk and privacy strategy
Let’s take a look at seven ways you can improve your data risk and privacy strategy to minimize business risk and optimize compliance efforts.
1. Visibility everywhere
In a modern enterprise, data is everywhere. That creates visibility challenges, given that the endpoint environment is heterogeneous. It might permeate through legacy and current Linux, Mac and Windows-based assets, as well as virtual machines, containers and cloud infrastructure of many different varieties. Understanding what data exists on those endpoints is foundational—if regulators believe you don’t have this insight, you may suffer bigger fines in case of an incident.
You must therefore build an accurate and current inventory, then identify controls needed to protect those endpoints and data. The ability to search quickly, easily and cost-effectively through this inventory is essential to finding noncompliant data and sensitive intellectual property (IP). It will not only help you to manage risk more effectively but could also reduce the third-party costs associated with Certificates of Data Destruction during off-boarding projects.
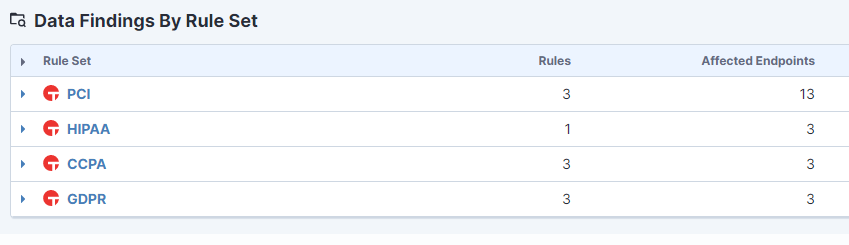
Comprehensive view of sensitive data
2. Encrypt all data at rest
Once you have compiled an accurate inventory as above, it’s time to think more holistically about the controls you can place on data and endpoints. Data loss prevention (DLP) tools are fine in some circumstances. But they can’t help if thieves disconnect stolen laptops/devices or remove the hard drive. That’s why strong encryption of all device hard drives is a good base level control to mitigate data risk. Many operating systems have the functionality built in today, so there’s no need to pay for third-party tools. But they do need to be managed at scale.
3. Data minimization starts with policies
Data minimization is a defining pillar of the EU’s GDPR and is increasingly seen as best practice by regulators globally. It’s based on the idea that organizations should collect and process only data that is adequate and relevant to the purpose at hand, and no more. Put simply: if you don’t need it, delete it. Alongside more technical measures such as encryption and DLP, it can be seen as a highly effective control in itself, as it minimizes the chances of sensitive data being stolen or misused.
Although technology is key to helping you find and erase any unnecessary data, your work should always begin with drawing up administrative policies. This goes not just for data minimization but anything from password management to obtaining informed consent from customers. Next up, find a way to communicate that policy effectively to your employees. Simple policies like this can go a long way, even if they don’t ultimately prevent an incident. If regulators find that controls weren’t effectively implemented, the fact that you have thought about and communicated policies to employees may still limit any punitive action.
4. Conduct privacy impact assessments
Privacy risk or data protection impact assessments are also key principles of the GDPR and CCPA. While it is vital to understand data flows with regard to existing applications and endpoints, it’s also important that you proactively address the same risks in new applications or projects. Take time to document what data will be collected and where it will flow. Then draw up administrative policies governing that data. Apply the data minimization lens to see if specific data even needs to be collected or if it will add unnecessary extra risk and potentially expose the business to major compliance fines.
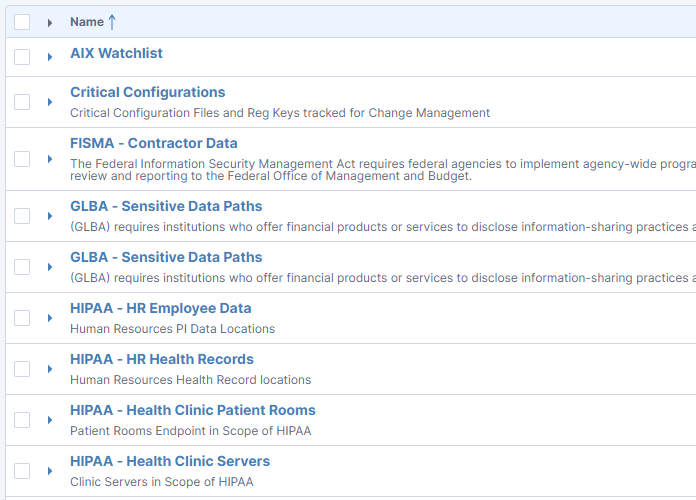
Use ready-made templates to simplify compliance
5. Understand geographical risk
More than 120 global laws govern data protection and privacy, and the number is growing all the time. In the US alone, some individual states have started implementing their own legislation. That creates a great deal of complexity for GRC officers. But one thing that most agree on is that data should be stored locally. In fact, the GDPR has strict rules governing international transfers to “third countries.”
Part of the discovery process must therefore be to understand where data is stored geographically in your organization and where it should be placed to comply with local regulations. Technology and administrative controls should be designed appropriately. Unfortunately, some data risk and privacy tools can exacerbate the problem by copying data and sending it back to a centralized server, which may be in another jurisdiction. Minimization and localization should be the watchwords here.
6. Due diligence on cloud providers
There is a bewildering array of choices in the cloud market for today’s IT leaders. But there are also some hidden risks. While smaller providers may offer attractively priced offerings, the maturity of their data management and privacy processes may not meet your requirements. Deploying third-party tools can lead to large bills as pulling data from cloud environments is typically expensive. Also, consider whether the provider has data centers in relevant regions, so you can fulfill obligations around localization.
7. Get a team together
Finally, remember that data risk and privacy is not primarily a technical challenge—it’s a business and regulatory problem that technology can help to solve. That’s why it’s essential to include not just technical but also legal, compliance and business leaders in developing a strategy. This isn’t something any one of those stakeholders can solve on their own. You may need a large team to map out the various global laws your organization is subject to, design appropriate administrative policies and then apply relevant technical controls.
It’s also important to push back on the view of some boards that this is a cost center ripe for headcount reduction. In fact, the men and women you choose to support your organization’s data risk and privacy strategy will pay for themselves many times over by preventing potentially major regulatory fines and reputational damage. An investment in them is an investment in the future.
For more information on the Tanium Data Risk and Privacy solution, read our blog post 10 Ways Tanium Improves Data Risk and Privacy.
If you’re ready to see it in action, sign up for a demo today.




