Tanium Further Strengthens Zero Trust Capabilities with Cloudflare Partnership
Starting today, Cloudflare, which increases the security and performance of web sites and services of global organizations, and Tanium are partnering to further strengthen organizations’ Zero Trust access policies. Customers of both platforms can now incorporate Tanium’s industry-leading endpoint visibility into Cloudflare for Teams, whereby Cloudflare Access policies decide whether or not a request can reach the applications that power an organization. This is especially relevant in a world where work from home (WFH) has exploded.
The rapid and growing shift to cloud-first technologies dispels the previously held mindset of “inside means secure,”giving rise to new products that identify, authenticate and authorize wholly remote users and devices. In the face of this new operational paradigm, organizations struggle to protect their sensitive applications and data from insecure or unapproved devices. Organizations lack the control required to secure these new networks by restricting not just the user, but more importantly, the devices that access these networks.
With Zero Trust, access to sensitive data, assets, applications and services is provided based on least privilege access, only when required, and user and device verification/authentication must occur before a connection is established. While user authentication has been getting much of the attention, Cloudflare and Tanium are pairing up to strengthen the second piece of that equation: device health.
Tanium’s Endpoint Identity solves this problem by extending Tanium’s visibility into the Zero Trust space. Without requiring another endpoint agent, customers can define which devices can access their Zero Trust networks. All of this is done through seamless and fast integrations with the industry’s leading identity and access management technologies, such as Cloudflare.
Cloudflare access
Cloudflare Access secures applications by applying Zero Trust enforcement to every request. Rather than trusting anyone on a private network, Access checks for identity any time someone attempts to reach the application. With Cloudflare’s global network, that check takes place in a data center in over 200 cities around the world to avoid compromising performance.
Adding more visibility
Tanium monitors and evaluates the health of the endpoint in real time, helping to reduce IT complexity by providing comprehensive visibility and control over endpoints from a single platform.
Like Cloudflare’s products for network performance and security, Tanium replaces traditional endpoint solutions with a single platform to help keep devices safe. Starting today, organizations can connect both platforms for comprehensive network and endpoint security.
How it works
Integrating Tanium and Cloudflare for Teams is a breeze. The handoff between Tanium’s agent on the device and Cloudflare’s network relies on mutually secured connections.
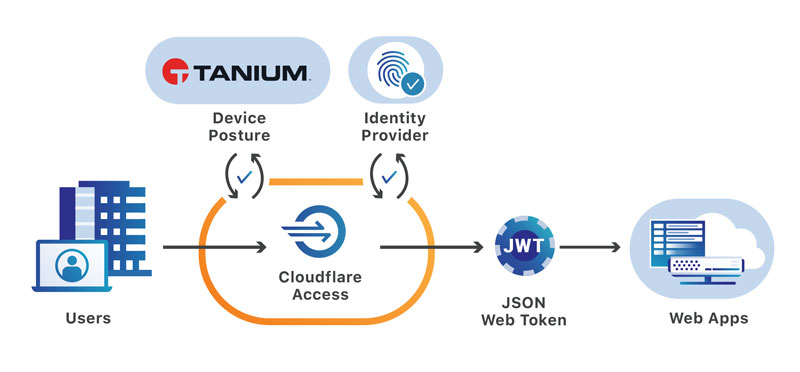
Image Credit: Cloudflare
Cloudflare’s network and Tanium’s distribution makes that check seamless for the end user. Cloudflare Access runs in all of Cloudflare’s data centers in 200 cities around the world; putting enforcement decisions within 100ms of 99% of the world’s Internet connected population. By integrating directly with Tanium, the evaluation can also occur without a connection back to the Tanium administrative layer.
What’s next?
Cloudflare/Tanium customers can immediately start enjoying the integration benefits by restricting access to remotely available resources to only managed and secured devices.
Learn more from Cloudflare’s perspective here.
Interested in seeing Tanium in action? Schedule a one-to-one demo or attend our weekly webinar. Talk to our Tanium experts at our upcoming events.




