How your organization could be affected
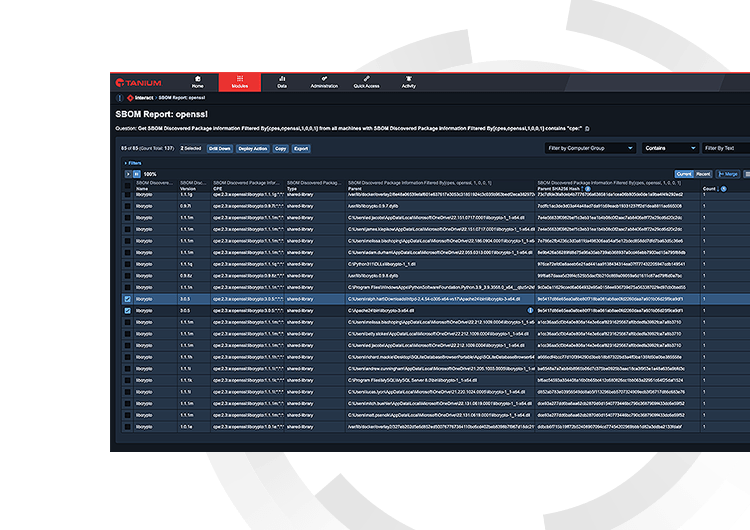
On November 1, OpenSSL issued version 3.0.7 to address high severity vulnerabilities found in versions 3.0 and above. The key to reducing your organization's risk is to find, patch and remediate any affected implementations as soon as possible. However, patching third-party open-source libraries like OpenSSL can be challenging.
1
Is this another Log4Shell?
No. The vulnerability isn’t as widespread or critical, but both CVE-2022-3786 and CVE-2022-3602 should still be patched as soon as possible.
2
Will this be widespread?
Even though OpenSSL is used from IoT devices to enterprise applications, the circumstances required for the exploit are specific and therefore not expected to be widespread.
3
Why is this challenging to find?
OpenSSL is source code that can be distributed statically or dynamically, resulting in dependencies that are challenging, sometimes impossible, for traditional vulnerability scanners to find.

Think you’re exposed?
We can help. Tanium can quickly find vulnerable software packages, patch them and continuously monitor as the situation evolves.