Tanium value metrics
Through comprehensive and real-time analytical insights about their devices, Tanium helps organizations measurably improve IT hygiene, employee productivity and operational efficiencies while reducing risk, complexity and cost.
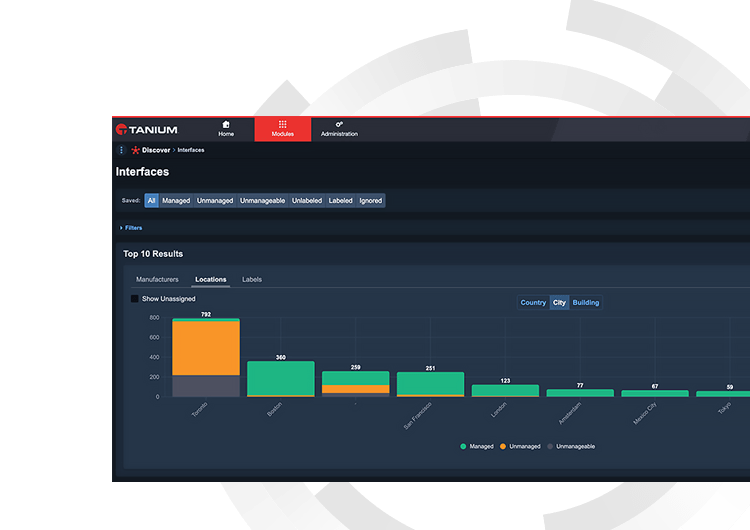
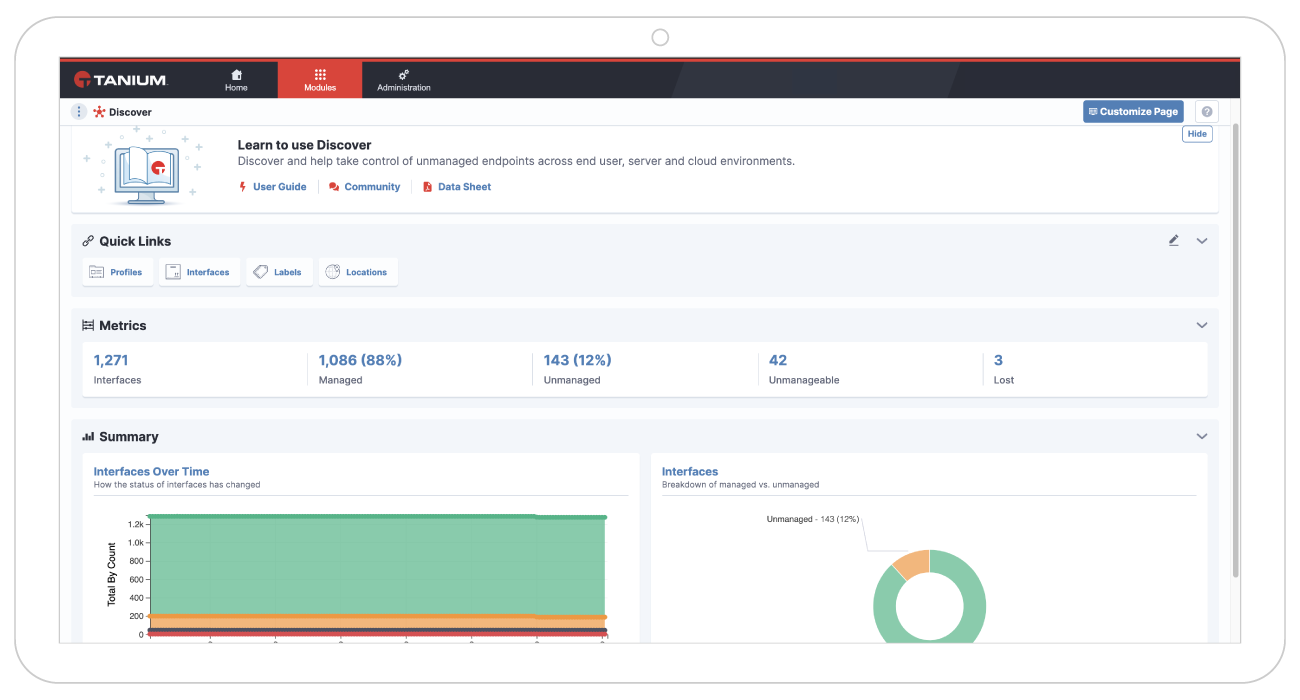
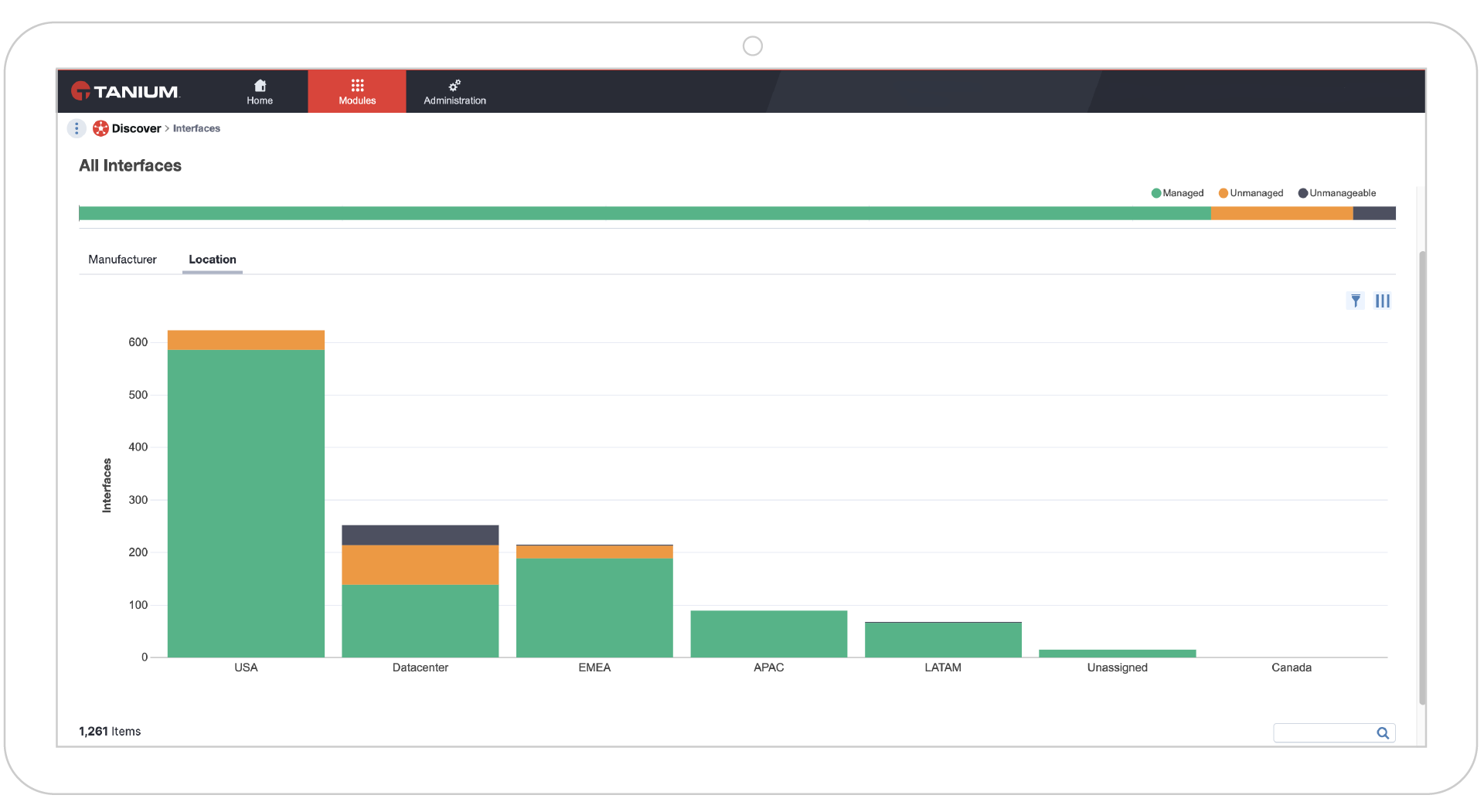
Endpoints managed (% of total endpoints)
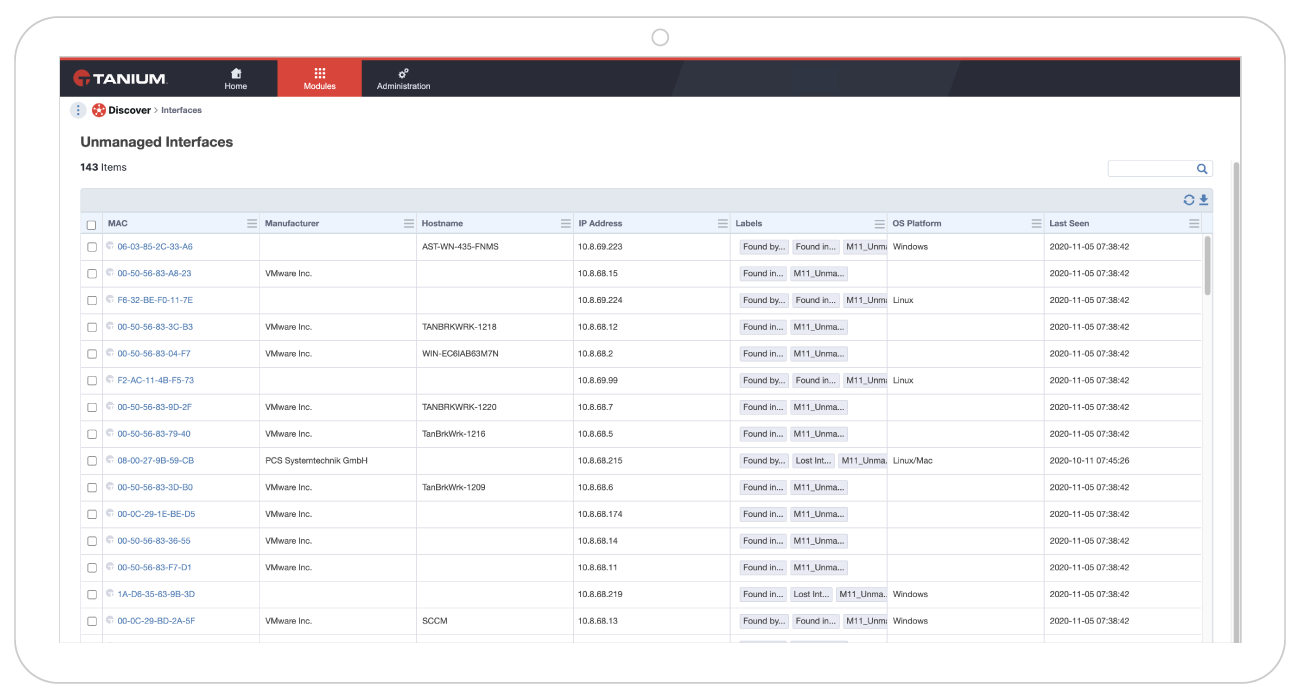
How many of your endpoints are unmanaged? Percent of total endpoints managed supports comprehensive discovery so organizations can mitigate business risk and assess how security policies are applied.
Mean time to manage (time in days)
How long do your endpoints remain unmanaged? Mean time to manage shows how long endpoints remain unmanaged. Unmanaged endpoints expose your organization to security risks and inefficiencies.