Tanium Enforce is the unifying force in policy and configuration management
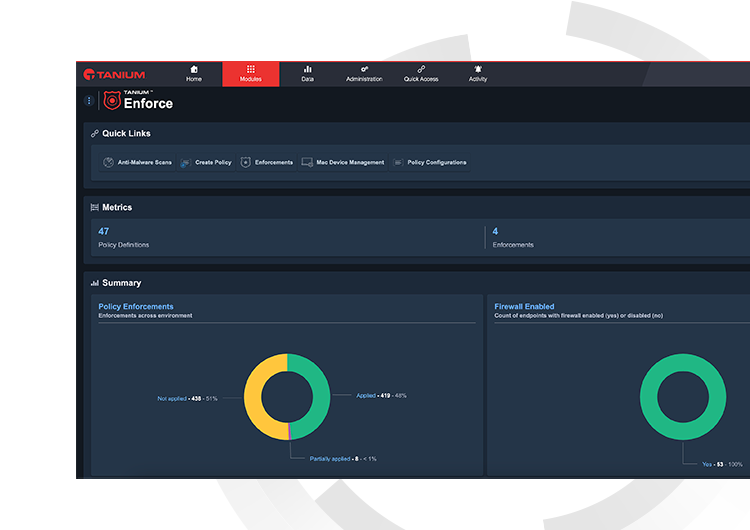
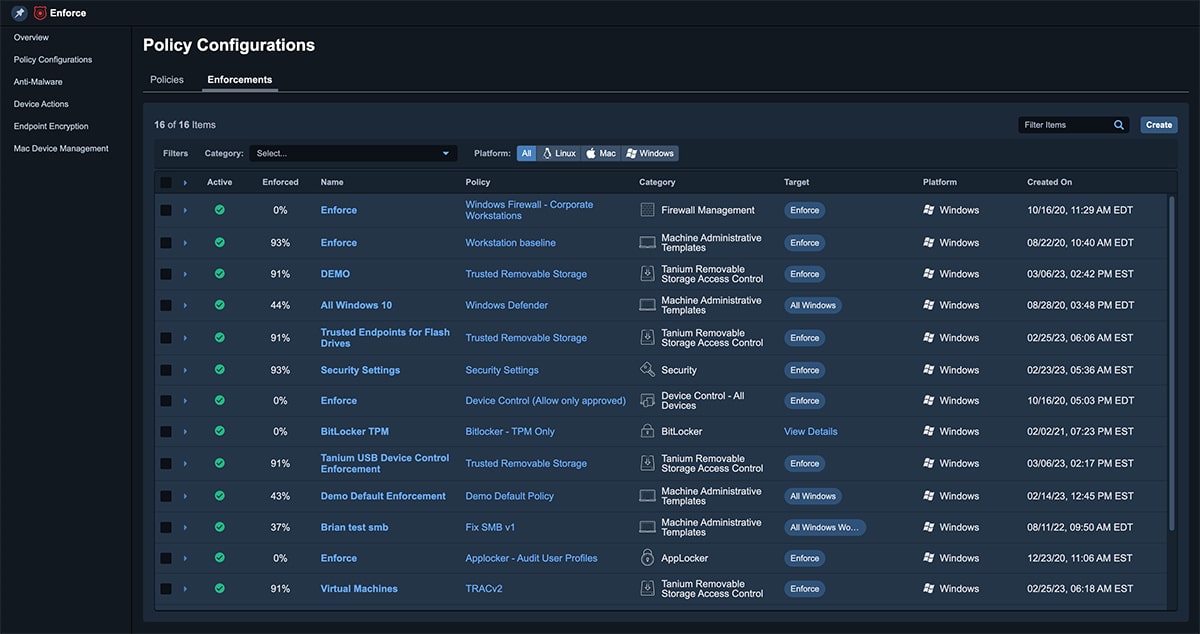
Tanium Enforce allows organizations to replace a variety of point solutions with a single console for policy and configuration management at scale anywhere.
1
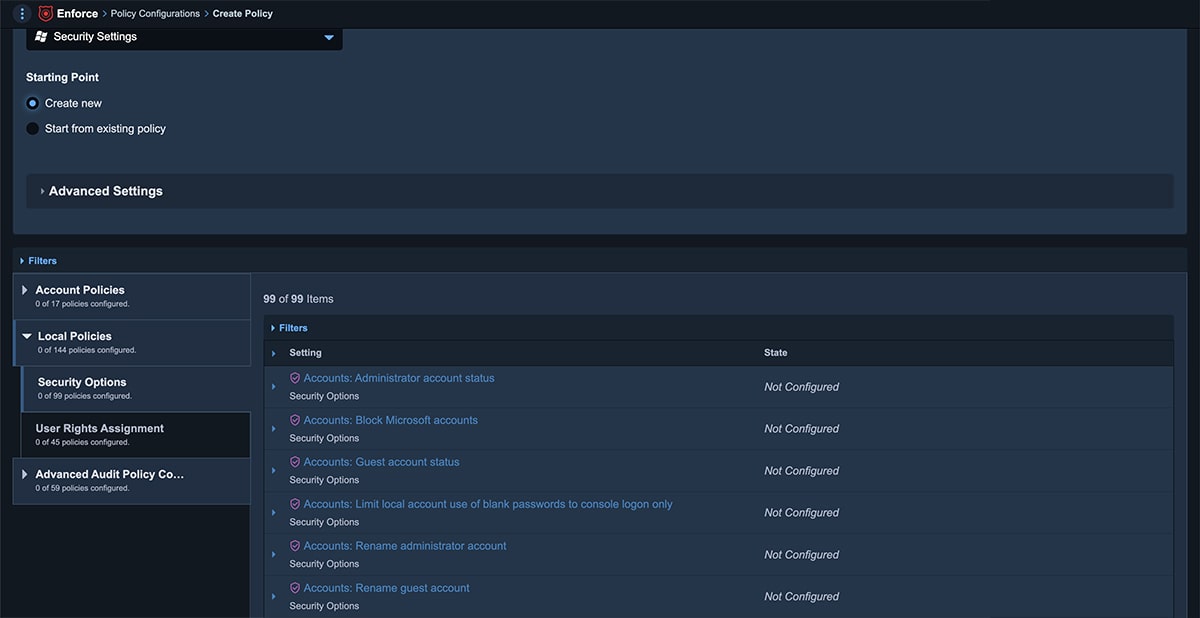
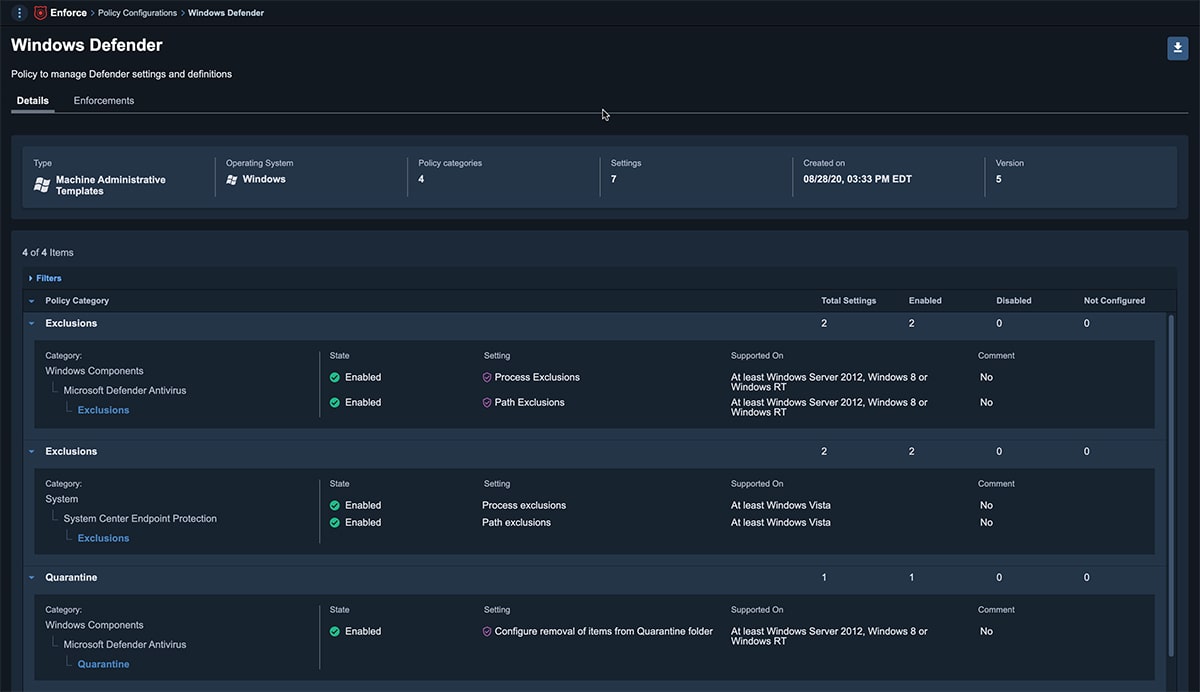
Enhanced policy management for Windows
With Tanium Enforce organizations can easily set up and manage their policies no matter what domain or lack thereof, on premises or remote, without the need of dedicated hardware or complex setup across their endpoint estate.
2
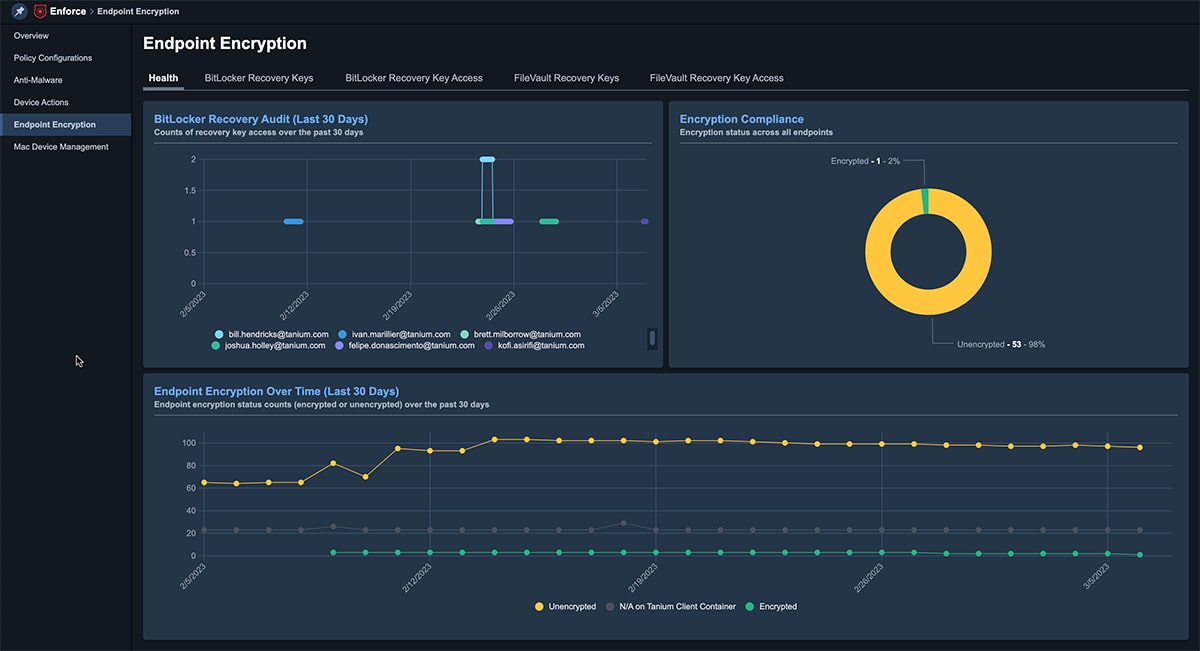
Enhanced Endpoint Encryption
Encrypting data at rest is essential if endpoints are lost, stolen or decommissioned. Tanium Enforce can manage native OS drive encryption offered by FileVault and BitLocker.
3
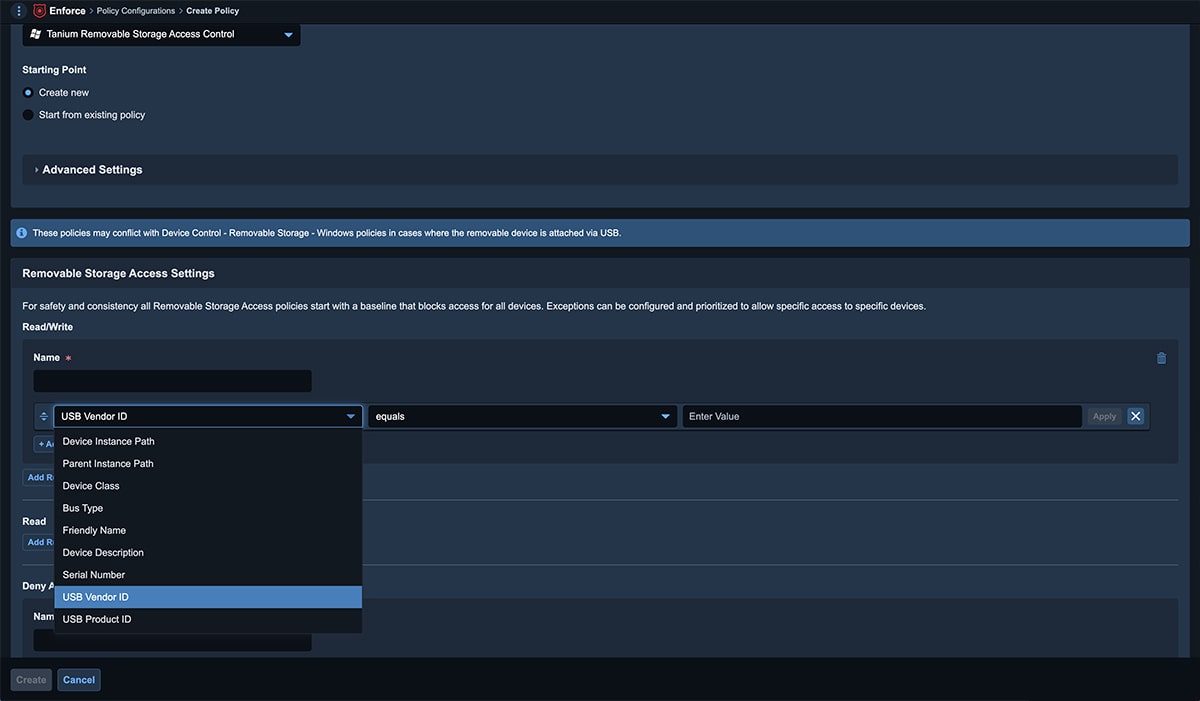
USB removable storage management
Protect your endpoints from unauthorized USB devices with Tanium's USB removable storage management.
Lack of policy enforcement can cost you
0
of remote systems’ policies cannot be applied or enforced
0
worth of sensitive data lost through USB removable storage
0
who found USB sticks in government parking lots plugged them into a computer
0
to bring all macOS devices into the office to manage