Tanium value metrics
Through comprehensive and real-time analytical insights about their devices, Tanium helps organizations measurably improve IT hygiene, employee productivity and operational efficiencies while reducing risk, complexity and costs.
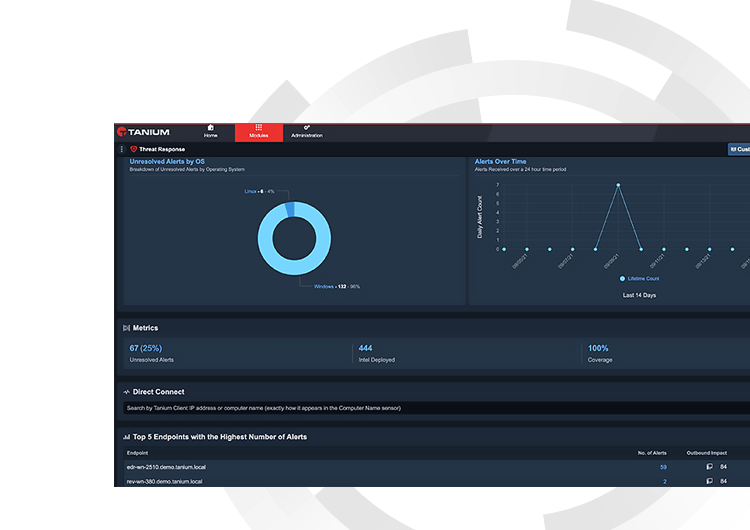
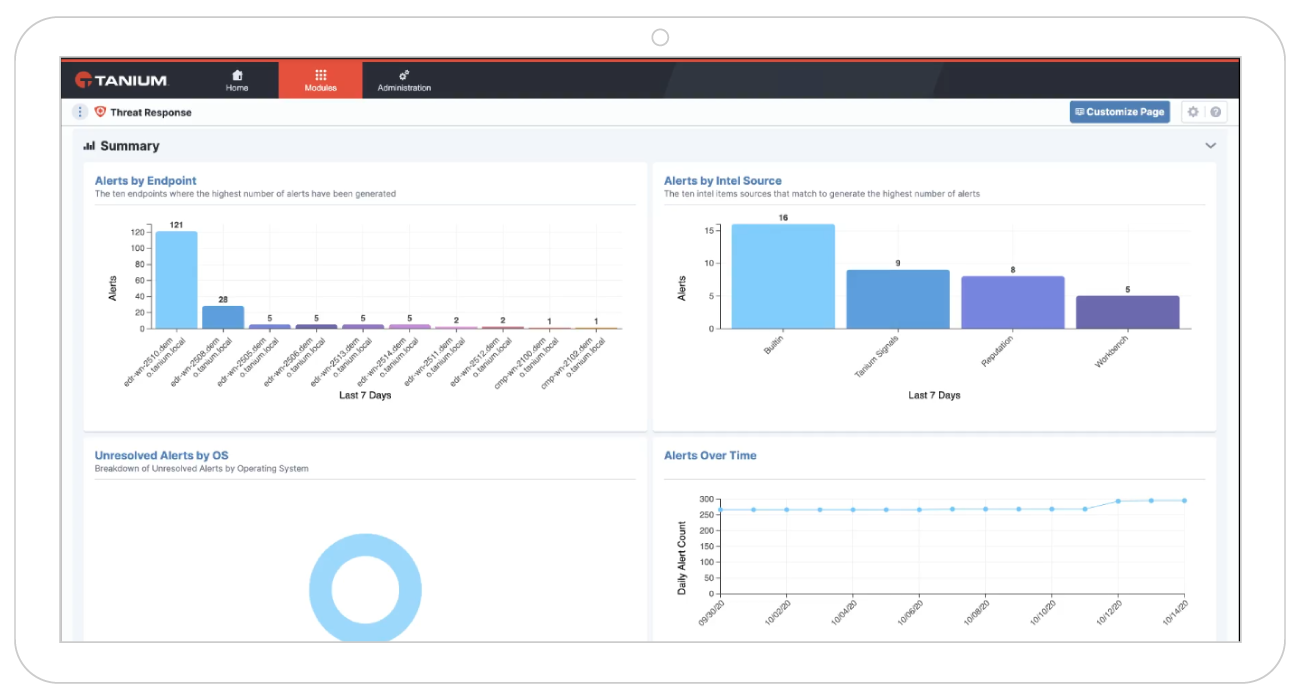
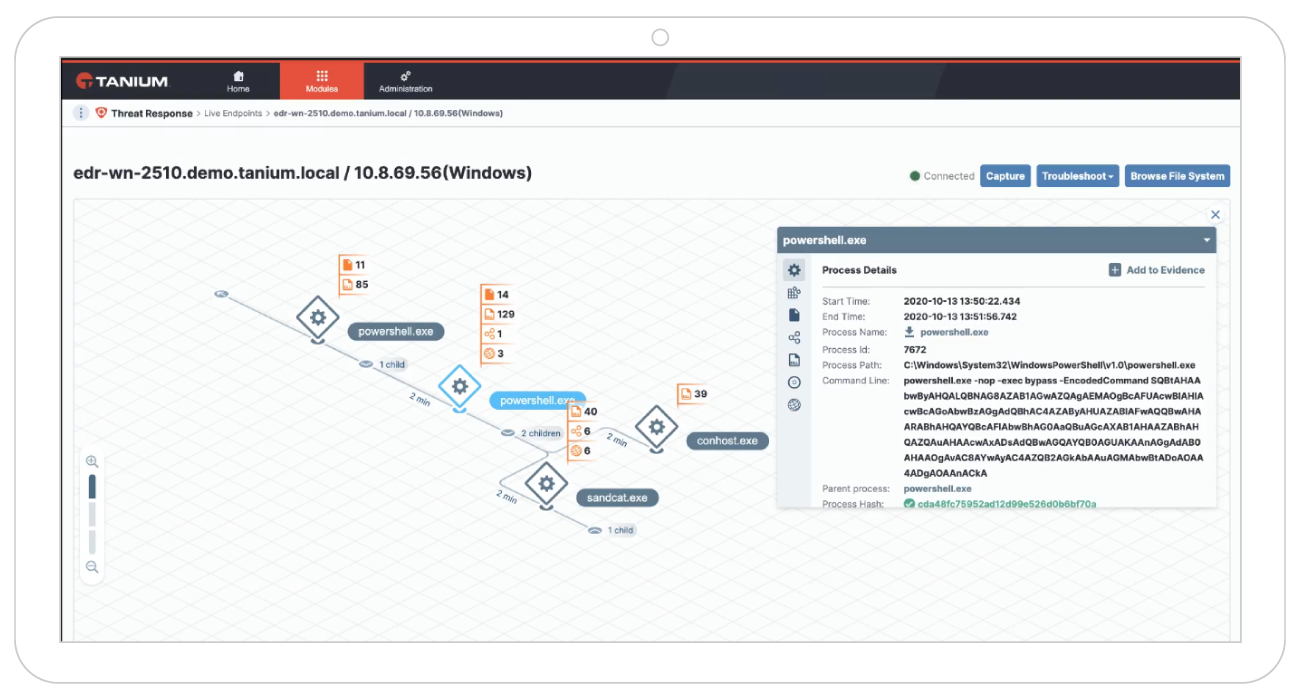
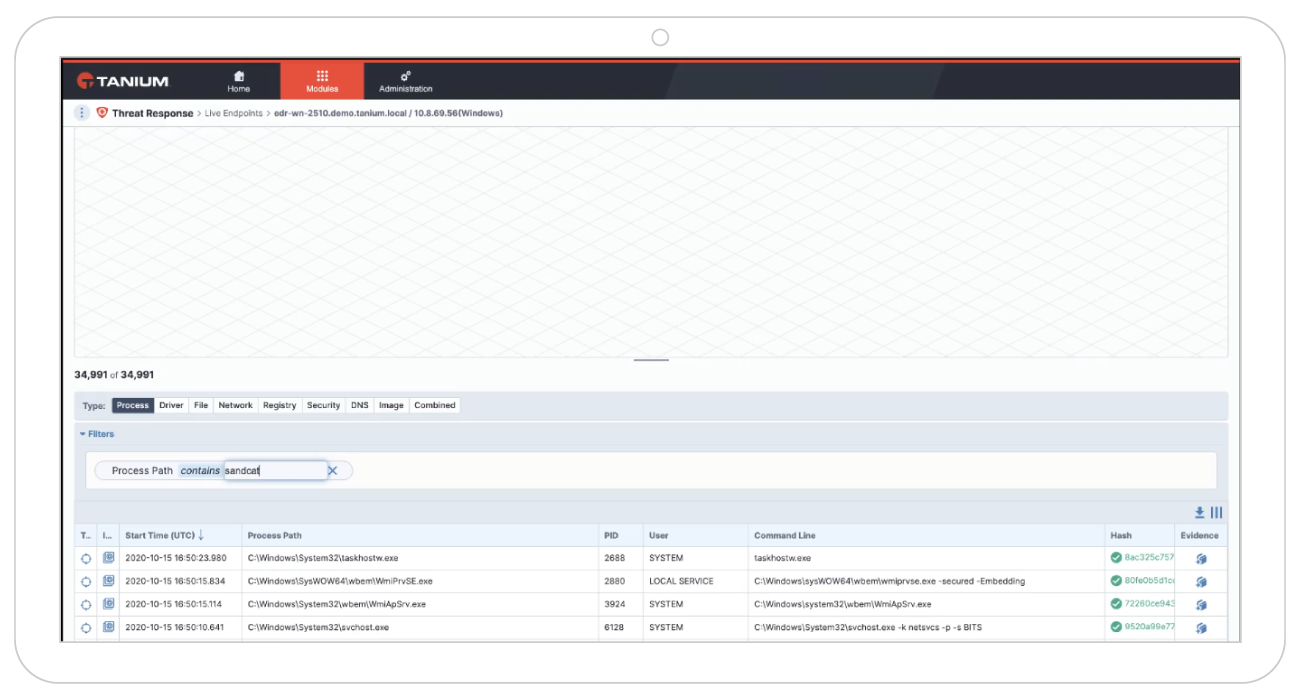
Mean time to investigate threats (elapsed time)
How long does it take your team to investigate a threat? The longer a cybercriminal has access to network resources, the more damage can be done. Mean time to investigate threats lets you know the time it takes to identify malicious activities from benign behavior.
Mean time to remediate threats (% of software)
Once you’ve identified a threat, do you fix it quickly? Investigating and remediating threats saves time and money. And faster is better. The mean time to remediate threats lets you benchmark response time and reduce it.