6 Charts That Show What Is and Isn’t Working in Endpoint Security
The massive shift to remote work has increased the complexity of securing endpoints. A new survey details the wins and losses and points the way forward.
By now, the story of how large organizations—from global manufacturers and consultancies to government agencies—mobilized their workforces during the pandemic has been well recited. Distributed workforces not only carried on, they grew their organizations’ market reach, productivity, and digital innovation.
CIOs have been hailed as heroes of the effort.
But with millions of workers connecting to corporate and public-sector networks over tens of millions of endpoints—laptops, PCs, tablets, virtual machines in the cloud—the complexity of securing those endpoints has exploded. Today, ransomware and other malware pose the biggest security threat to organizations. That’s followed by human error, insider threats, and software vulnerabilities (see: the Log4j flaw), according to the new 2022 Endpoint Security Visibility Report, produced for Tanium by Cybersecurity Insiders.
As cyber assaults against private and public organizations have mushroomed, hitting critical infrastructure, software providers, and government agencies, business and tech leaders have struggled to maintain resilience. The recent directive from the Cybersecurity and Infrastructure Security Agency (CISA) ordering all federal agencies to patch some 300 software vulnerabilities is a crucial step for the government and for the private industries that look to it for guidance.
The new survey, which queried 345 cybersecurity professionals, highlights what is and what is not working for endpoint data security. The charts below illustrate the challenges and solutions for organizational, business, technology, and security leaders.
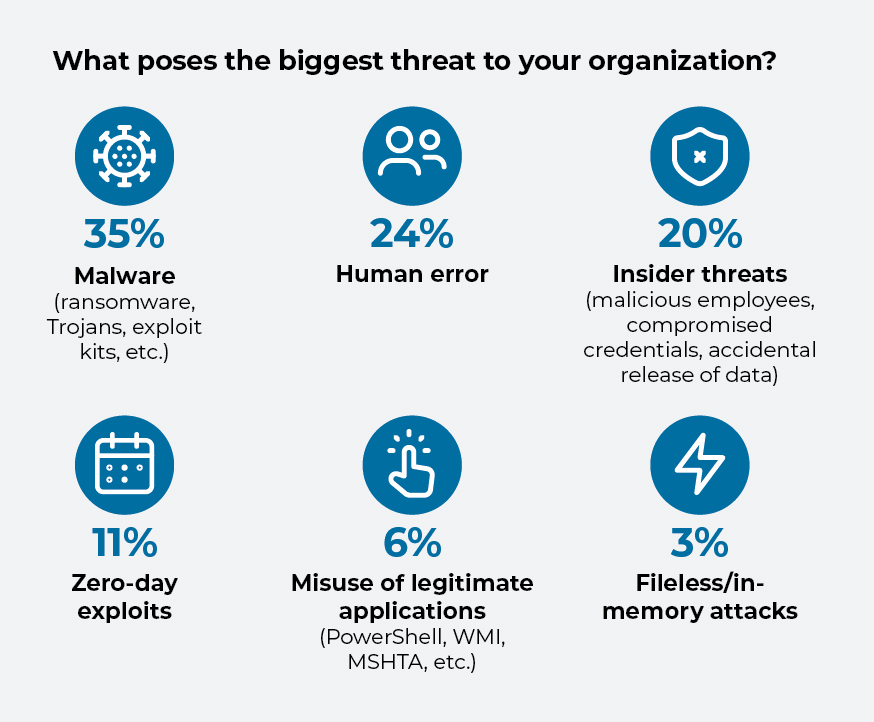
Hackers, encouraged by the yawning attack spaces created by remote working and distributed endpoints, have made 2021 the year of ransomware, seizing network assets and demanding cash for their return. More than a third of respondents in the survey list malware and ransomware as the greatest security threats to their operation.
Lesser but still significant threats are those resulting from human error. From emailing the wrong person to lost or stolen passwords, people inevitably make careless mistakes and bad actors are ready to pounce. Nearly a quarter of respondents cite employee missteps as among their chief security concerns.
[Read also: How real-time incident response resolves the inevitable breach]
And while outside threats are the biggest cybersecurity risk, dangers lurking from within are problematic, too. A fifth of respondents are concerned about the risks posed by untrustworthy or malicious employees, with an ax to grind or an eye on personal gain.

While organizations are worried about cyber threats, they’re also concerned about their ability to deal with them. Some 36% of respondents cited issues with their speed of incident response, and 32% doubted their threat-detection capabilities.
More than a quarter say they have no visibility into their overall cybersecurity posture. This is problematic because three areas make up the major building blocks of good cyberdefense: It’s not just the tools and processes—it’s the people. A third of respondents say they lack in-house cybersecurity skills, and 38% say their biggest challenge is patrolling cybersecurity 24 hours a day.
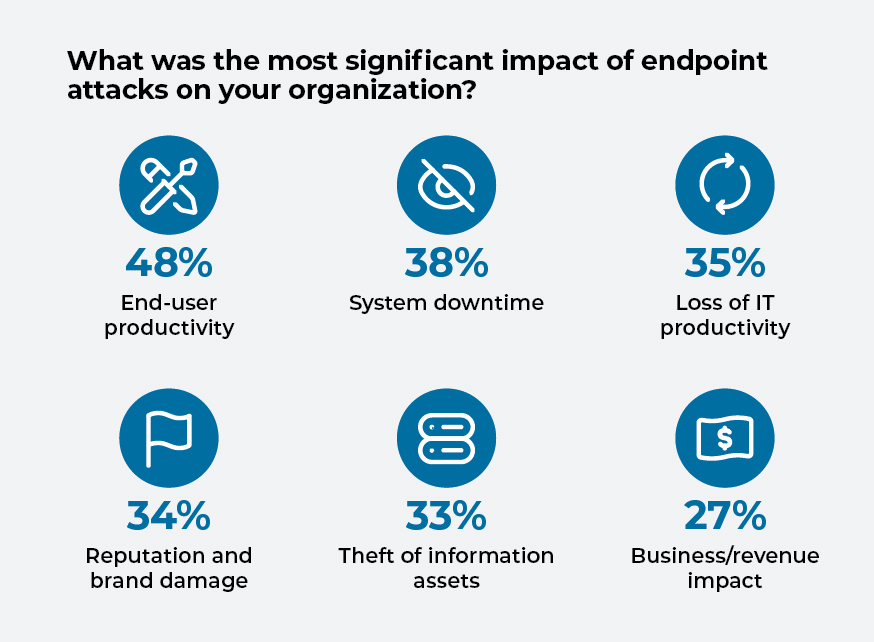
Attacking endpoints can impact end-user productivity and allow hackers to gain leverage over their targets. When a company’s business is halted or disrupted by a cyberattack, the business owners usually opt for the fastest route to getting operations back online. If it’s a ransomware assault, that often means paying the attackers.
Almost half of respondents cited loss of end-user productivity as the main negative impact from endpoint attacks. More than a third cited system downtime, and a similar proportion cited loss of IT productivity and brand damage.
In September, the FBI spelled out the cyber threats facing nearly all organizations, from small farms to large producers, processors, manufacturers, markets, and restaurants. The agency said hackers are targeting network vulnerabilities to steal or lock up data and encrypt systems, particularly in business sectors that are “increasingly reliant on smart technologies, industrial control systems, and internet-based automation systems.”
[Read also: 6 tips for shielding your organization from rising cybercrime]
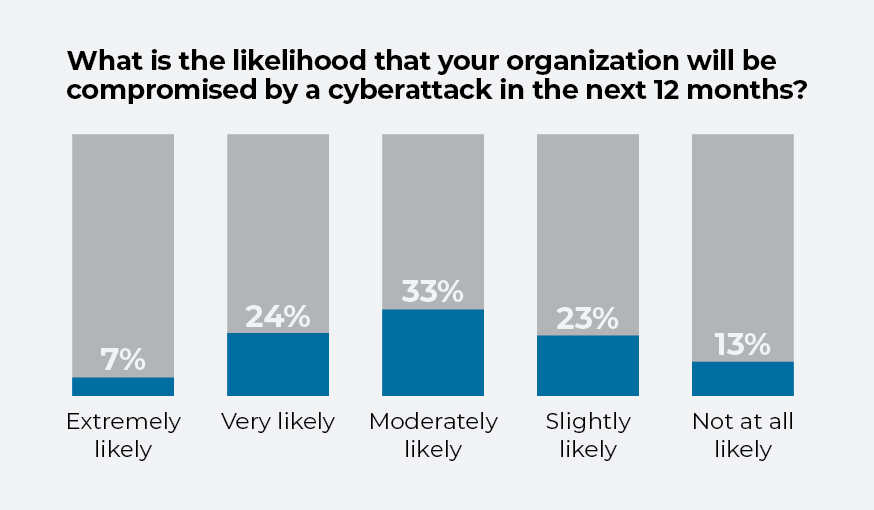
Nearly all organizations understand the threats. A third of survey respondents say the risk that their organization will be compromised in the next 12 months is “moderately likely.” A quarter view a breach as “very likely,” while 7% peg that risk as “extremely likely.”
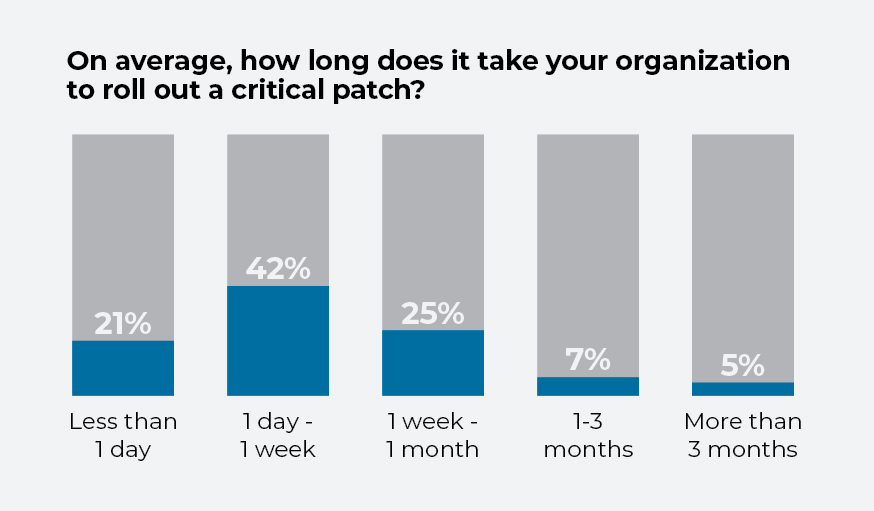
Regular software patching is critical to cybersecurity. But just as important as identifying flaws is the speed of patching itself. Remote work has created bigger networks and bigger patching needs: Workers use an assortment of devices to access corporate networks and services from new and differing locations. There are also dangers in hasty patch management. Patching updates with weak cyberdefenses are a lucrative entry point for cybercriminals.
[Read also: Patch management—challenges and solutions for implementing an effective strategy]
The most common patch-response time, according to the survey, is between one day and one week, with 42% of respondents saying they patch within this time frame. Some 37% say they take longer than a week to patch, while a fifth take less than a day. But even taking a day to patch can allow hackers to cause massive disruption with long-lasting damage.
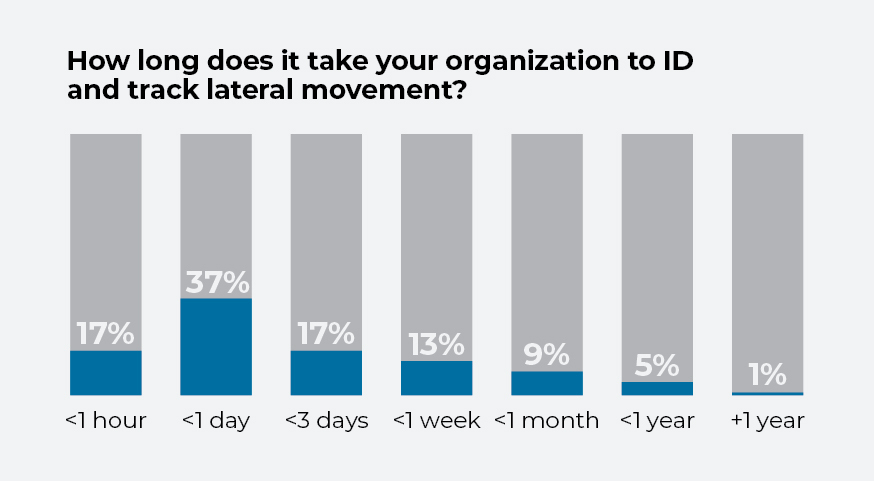
If a cybercriminal or nation-state gains a foothold in an organization’s network, limiting their movement is the next crucial line of defense. Organizations can deploy tools to detect suspicious activity on their networks and use strategies to block lateral movement, for instance by restricting administrator rights and adjusting network configurations.
Real-time response is key to these efforts. More than a third of the survey’s respondents say it takes them less than a day to pinpoint and track lateral movement. Some 17% say it takes less than an hour, while 17% say it takes them less than three days.








