9 Ways Tanium Improves Vulnerability and Configuration Management
Coping with an expanding attack surface as the pace of digital transformation accelerates.
Today’s enterprises are in a bind. On the one hand, they must accelerate the pace of digital transformation to survive and thrive at a time of global crisis. But as they do so, the corporate attack surface continues to expand.
To address this, enterprises need a vulnerability and configuration management platform that helps them easily identify security exposures and quickly mitigate risk across all endpoints. With the right tool in place, CISOs and IT Ops leaders can make major IT hygiene improvements and create an approach for lasting business success.
Challenging times
The COVID-19 pandemic has compounded existing endpoint visibility challenges for organizations, thanks to surging numbers of remote workers and new IT and business priorities. The impact could be severe: 60% of organizations have previously been breached as a result of an unpatched vulnerability.
Unfortunately, most current vulnerability and configuration management tools fail their users because they lack real-time data, are excessively bandwidth-hungry, and are too narrowly focused, leading to tool sprawl.
Tanium offers a better approach.
Here are 9 ways Tanium helps organizations improve vulnerability and configuration management
1. Work from a single console
The Tanium Platform helps operators carry out essential identification, reporting, remediation and validation actions from within the same streamlined user interface. By being continuously informed through on-demand or recurring vulnerability and configuration assessments, operators can review their immediate security status through dashboards and reports.
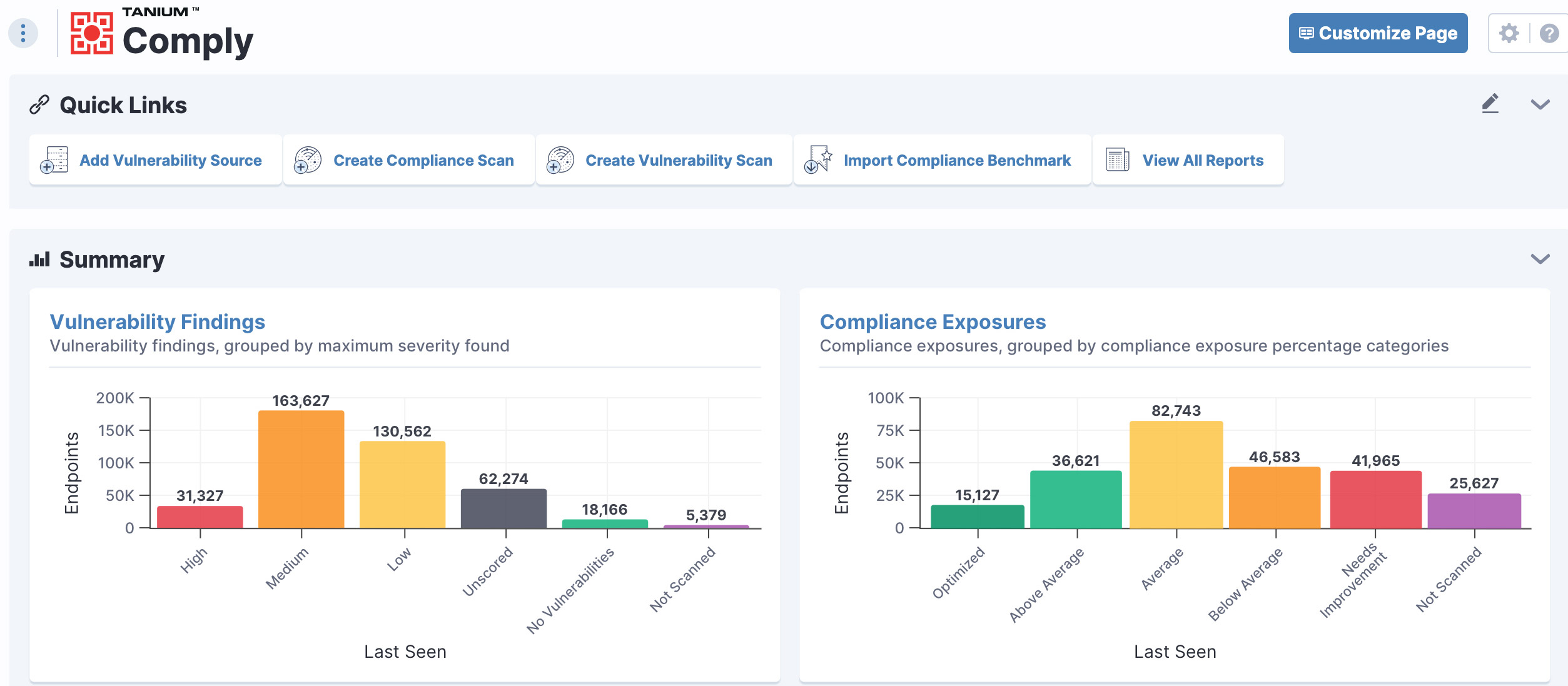
Streamlined user interface with Tanium
As high-priority issues are identified, operators can perform one-click remediation through patching, software updates, and policy and configuration changes. Metrics and evidence for key reporting and compliance audits are available in real time, eliminating the need to manually correlate data from multiple tools. This helps simplify workflows and enhance user productivity while eliminating tool sprawl.
2. Benefit from comprehensive assessments
Many vulnerability and configuration management tools are limited in their effectiveness because of bandwidth constraints, especially in managing remote devices.
Typically, scans are conducted on a remote basis that requires security exceptions and the ability to remotely authenticate onto devices. These scans often run serially across the inventory of remote devices and can take hours or days to complete.
Thanks to Tanium’s patented distributed architecture, the Tanium Platform can assess hundreds of thousands of endpoints with minimal impact — supporting multiple assessments of the endpoint environment, if required, in near real time.
3. Automate remediation tasks
Many existing vulnerability and configuration management tools rely on separate tools or third-party integrations to resolve issues they uncover, which adds to the burden on IT staff and forces organizations to invest in additional solutions.
Tanium allows remote staff to quickly and easily perform critical actions to fix any vulnerability or misconfiguration issues. Even better, the Tanium Platform can automate a number of vulnerability remediation processes to free IT staff to work on higher-value tasks.
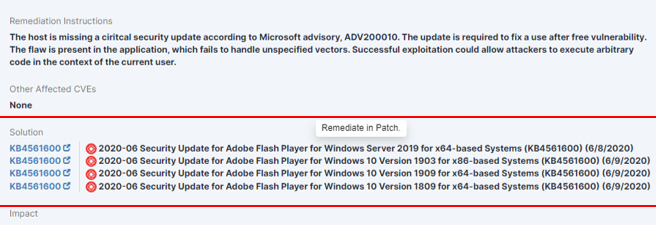
Tanium allows you to automate remediation
4. Unite teams with a distributed architecture
Tanium’s unique linear chain architecture makes it possible for organizations to replace complex sets of traditional point tools to greatly simplify how they remediate and patch endpoint devices.
Rather than siloed tool sprawl, Tanium provides a single platform capable of scaling to hundreds of thousands of endpoints without impacting bandwidth. In doing so, it provides a single source of truth for siloed IT operations and security teams to unite around. And team collaboration matters: One study finds that coordinating with other parts of the business can add an extra 12 days to the patching process using traditional tools and approaches.
5. Minimize bandwidth issues
As mentioned, legacy vulnerability and configuration management solutions are typically network intensive and bandwidth heavy. This restricts the scope of endpoint scans and forces organizations to carefully manage their assessment schedules and remediation activities.
But Tanium’s distributed architecture places data processing and collection at the endpoint layer to minimize performance disruptions or downtime. Most important, it means Tanium supports continuous monitoring of the endpoint environment if desired, for maximum visibility and control.
6. Support ecosystem of compliance tools
Global organizations spend tens of millions each year on compliance with data protection regulations. Yet even as the regulatory environment continues to rapidly evolve, legacy tools have been built to meet just a limited set of existing standards and known security challenges.
Tanium’s approach is more open and adaptable. Backed by APIs that make it easy to integrate with third-party products, Tanium allows customers to rapidly adapt to changes to their security and compliance requirements.
7. Gain insights with rich metrics
For IT leaders, ongoing assessments of technology solutions are key to evaluating return-on-investment (ROI) and developing more effective strategies.
With Tanium’s rich data and visibility, users can extract key data and metrics they need anytime to inform compliance audits, remediate issues, report on progress against security initiatives, and measure key metrics like mean-time-to-identify.
8. Streamline workflows
Tanium is focused on helping organizations run more efficiently and securely without putting extra pressure on already overburdened IT teams. To help with this, the Tanium Platform helps organizations create automated workflows to reduce repetitive, manual tasks. Thanks to these capabilities, IT operations and security staff can focus on more strategically important work.
9. Report as you like
The final piece of the vulnerability and configuration management puzzle is reporting. Within Tanium’s intuitive console, customers can access flexible reporting capabilities — ranging from high-level executive summaries to generating data-based answers to detailed questions.
Tanium’s real-time data can support external and internal audits while helping show business efforts key results of remediation programs.
With the Tanium Platform, your organization can reduce the financial and reputational risk associated with security breaches while minimizing the time and resources required to manage vulnerabilities and compliance.
Learn more about Tanium Vulnerability and Configuration Management and request a demo.
You can also read our other blog post Seven Ways to Improve Your Vulnerability and Configuration Management Program.




