What is Phishing? Types, Risks, and Prevention
Phishing attempts lure people into sharing sensitive data like bank and credit card information. These attacks exploit human vulnerability, not system flaws, to gain usernames, passwords, and unauthorized access.
UPDATE: This post, originally published on November 27, 2023, has been updated to reflect the most current information available about phishing attacks.
Phishing attacks are a cunning tactic cybercriminals use to deceive individuals into divulging sensitive information, such as bank account details and credit card numbers. These schemes are meticulously crafted to mimic legitimate requests for data, often through emails that appear to be from trusted sources.
By exploiting human vulnerability, these attacks bypass the need to leverage technical or configuration errors within systems. Instead, they focus on manipulating people into providing usernames, passwords, and other credentials, granting attackers unauthorized access to secure systems and data.
Phishing is one of the most infamous and pervasive types of cyberattacks today. It’s a form of social engineering attack that originated in the 1990s when the early World Wide Web introduced the concept of usernames and passwords to the masses. The Anti-Phishing Work Group and the Federal Trade Commission (FTC) have been at the forefront of combating these threats, providing valuable tips and resources to help individuals and organizations stay safe.
In this post, we’ll start by defining what phishing is and then explore the various types of phishing attacks. From there, we’ll examine the security risks associated with phishing and why it’s so challenging to stop. We’ll also look at real-world examples of phishing attacks and how they’re evolving over time.
Additionally, we’ll discuss the role of AI in modern phishing schemes and provide practical advice on preventing phishing attacks in your organization. We’ll cover how to train employees to recognize phishing attempts, what to do if you click on a phishing link, and how organizations can combat phishing while enhancing the digital employee experience.
- What is phishing?
- What are the different types of phishing attacks?
- What is the security risk of phishing?
- Why is phishing so difficult to stop?
- What are examples of phishing attacks?
- How are phishing attacks evolving?
- What role is AI playing in phishing attacks today?
- How can I prevent phishing attacks in my organization?
- How do I train employees to recognize phishing attacks?
- What to do if you click a phishing link
- How can organizations fight phishing attacks while improving the digital employee experience (DEX)?
What is phishing?
Phishing is a type of cybercrime where attackers trick people into giving away sensitive information like passwords or credit card numbers. This is often done through fake emails, texts, or phone calls that look like they come from trusted sources and can contain links to fake websites or malware. Typical signs of phishing include typos, poor grammar, and unusual greetings.
Pharming is a common technique used in phishing to redirect users from real websites to fake ones without their knowledge, many times through manipulated URLs. Victims may unknowingly download malware or provide sensitive information that can be used for further cybercrime.
Now that you have a clearer understanding of what phishing is, let’s explore the different types of phishing attacks and how threat actors use phishing to target individuals and organizations.
What are the different types of phishing attacks?
Phishing comprises a wide array of attack types, with more emerging over time. Some of the most common include:
- Email phishing: Phishing emails are the most pervasive type of phishing attack. Here, an attacker (commonly a spam emailer) sends a message designed to look legitimate, such as from a financial institution or a business the victim engages with.
Fraudulent hyperlinks in the email lead to a fake website that looks legitimate to trick users into entering their personal details, like bank account information, which the attacker captures. Email-based phishing attacks like business email compromise (BEC) have long been a primary attack vector. - Spear phishing: A more personalized version of the email attack, spear phishing messages rely on information gleaned about the victim to enhance the message’s legitimacy and improve the odds of a successful attack. Spear phishing often targets high-value victims, such as CEOs and finance professionals, as the spoils of these attacks can be immense. “Whaling” is another term commonly used to describe the spear phishing of extremely high-value targets.
- Vishing: Voice phishing attacks take place over the phone, lending an air of added legitimacy and urgency to the attack. A visher will often tell a victim that their computer has been compromised and walk them through the steps needed to grant remote access or coax them to give personal information like passwords and credit card numbers.
- Smishing: SMS phishing occurs via text message but otherwise resembles email phishing tactics. Again, it takes advantage of lower consumer awareness about the risks of fraudulent texts.
- Social media phishing: Popular platforms like Facebook and Instagram have become lucrative avenues for attackers to find new phishing victims. Phishers often create phony profiles and befriend the victim by using the personal information people share about themselves on these sites.
What is the security risk of phishing?
While a phishing attack can be devastating to an individual, it can be even more costly to a business. A single compromised username and password can open the entire enterprise up to the attacker if that account has elevated access privileges. These attacks can lead to unauthorized access to systems, data breaches, and malware infections. The consequences include financial losses, identity theft, and compromised IT security.
Phishing attacks have steadily grown in prominence since they first appeared, with no signs of slowing down. In 2022, nearly 38% of all complaints received by the FBI’s Internet Crime Complaint Center (IC3) were related to phishing – the most common type of cybercrime IC3 tracks. As phishing attacks become more sophisticated, using phishing to plant malware like ransomware in computer networks is increasingly popular with cyber gangs.
Given this rising threat, which experts believe will only worsen with the advances of artificial intelligence, learning how to recognize and prevent phishing attacks is essential for individuals and organizations alike.
Why is phishing so difficult to stop?
For attackers, phishing remains the preferred method because it is so lucrative. It’s one of the simplest types of attacks for scammers to engage in, as attackers need no significant amount of specialized knowledge to mount an attack. This has led to such a massive number of phishing attacks that the sheer volume of them overwhelms many organizations.
Humans, by nature, tend to trust what they’re told – particularly if it has some sense of urgency.
Phishing requires minimal energy and minimal cost, which alone would be enough to sustain it. But even more of a driver is its high success rate compared to other types of attacks since humans, by nature, tend to trust what they’re told — particularly if it has some sense of urgency.
Notices that our various accounts have been canceled, that charges have been applied for purchases we didn’t make, or that we have unclaimed rewards waiting to be collected all sound like pressing issues that require further, immediate investigation. Phishing attacks are often designed to instill some level of panic or urgent enticement – “free TikTok followers” – further lowering the victim’s guard.
The bottom line is that phishing is designed to prey on the psychology of the victim, which makes it difficult to defend against.
Meanwhile, phishers are getting better and better at luring victims, so even experienced users are caught off guard by fraudulent emails and text messages that look quite real. For less experienced users, a lack of experience with these types of attacks puts them at even greater risk.
All of this continues to feed the phishing fire, which shows no signs of abating anytime soon.
What are examples of phishing attacks?
One of the more challenging aspects of phishing is that every attack looks different, so it’s hard to create any universal guide to defend against them. In general, these are some of the most common types of phishing attacks and how they work:
- Emails designed to look like legitimate corporate correspondence: Phishing emails are usually commercial and almost always contain an embedded link directing the victim to a malicious website that aims to harvest login credentials or financial information like account numbers or to install malware.
Some of the most common types of phishing emails are phony invoices for products or services the victim did not purchase, notifications from banks or other service providers (usually alerting the victim to some fraud, charge, or account cancellation that hasn’t really occurred), notifications that the victim is due funds, or messages from the victim’s employer (often spoofing human resources or executive email accounts) instructing them to take some kind of action.
[Read also: What is business email compromise?]
- Messages that claim to be from the government: A typical phishing attack pattern is to mimic a government agency with a scary message like, “The IRS says you owe taxes” or “The police say an arrest warrant is out for you.” Another common attack claims that your Social Security number has been somehow “canceled.” All these phony statements attempt to frighten the user into taking action and providing personal or sensitive data.
- Text messages from people who claim to know you: Phishing text chains can begin with something as simple as a “Hello” from an unknown phone number, after which they can take any number of avenues to route to some fraud.
- Messages designed to look like they’re from a colleague or loved one: These are often used in spear phishing attacks and can be delivered via email or text. They often ask the victim to take a financial action, such as “Can you make a wire transfer for the company?” or “I’m stuck and need money; can you send me cash via an online payment system?”
These messages prey on victims who will naturally be more willing to help their boss or a relative – with those contacts’ identities often scraped from social media. - Social media messages from hacked or spoofed accounts: Social media is now fertile ground for phishing attempts where phishers make contact via direct messages on social media apps. Many such phishing attacks begin with a simple request that a victim “follow” the phishing account, which helps to improve their appearance of legitimacy and long-term success rates.
- Phone calls with “urgent” information: Vishing attacks are more complex and costly, so vishers often get straight to the point. These attacks usually inform the victim that they have invoices (or taxes) due and offer to take an immediate payment over the phone, that a prize has been won and requires some advance payment to receive it, or that – commonly – their computer has been compromised and requires a system update to repair it.
These phony tech support operators invariably install malware onto and/or steal credentials directly from the victim’s device.
How are phishing attacks evolving?
Phishing is evolving along with the rest of the technology industry, becoming more pervasive, easier to undertake, and more sophisticated. Some of the key advances in recent years include:
- Frequency: Phishing is everywhere. What was once restricted to email is now a universal problem across all communication platforms: text messages, phone calls, various types of documents, search engine results, other browser-based platforms, and even in-person media. Nowadays, phishing attacks are even commonly embedded in QR codes. Mobile device–based attacks have proven to be far more effective than email-based ones, so these attacks are likely to continue.
- Quantity: The amount of unprotected consumer data is exploding. Users share more information online than ever, and very little of that is protected behind a corporate firewall. This is giving attackers more ways than ever to exploit their victims.
- Democratization: “Phishing-as-a-service” gives criminals turnkey access to sophisticated attack technologies. Embarking on a career as a phisher no longer requires specialized knowledge. Subscription services now allow anyone to launch phishing campaigns by clicking a few buttons and paying the service operator less than $100 monthly. These services are often hosted on legitimate cloud services, which makes them even more challenging to detect and stop.
- ROI: Nation-state attacks are becoming less of a threat; phishing is now dominated by those focused on monetary goals and return on investment. Like any smart business executive, cybercriminals are looking at ways to diversify and turn phishing attacks into a recurring revenue stream. The result is more aggressive actions, such as extortion, proving that phishing is not only on the rise but continually evolving.
- Automation: AI tools help phishing attacks evade detection. We previously discussed the ways that AI is making phishing messages seem more natural and realistic, but AI is also impacting cybersecurity evasion, including bypassing spam filters and antivirus solutions.
“Polymorphic” phishing technologies also allow phishing messages to adapt their look, language, and target URLs on the fly, making them even harder to detect. These technologies alter the sender’s name, email address, and even the body of the message so that each email is unique – and more likely to bypass anti-malware filters.
What role is AI playing in phishing attacks today?
Historically, phishing messages have been generated by unsophisticated attackers with poor writing and design skills, making their typo-ridden messages exceedingly easy to spot.
Those days are gone.
The standard phishing defense of looking for obvious spelling or grammar errors is no longer effective. With AI tools like ChatGPT, attackers can easily clean up their grammar and write with better clarity, both of which make their attacks much more difficult to detect.
In some cases, AI is even taking things a step further by allowing attackers to mimic the voice and style of a victim’s friends and colleagues. A victim’s manager can be imitated down to their distinctive use of slang, commonly used phrases, and shorthand – even emojis. Now, those polished phishing emails can be cleverly personalized, making it nearly impossible to tell the difference between a malicious attack and a genuine article.
Besides leveraging AI, cybercriminals are also leveraging our interest in AI. In the summer of 2023, cyber researchers detected an uptick in fake AI promotions on Facebook, in which cybercriminals created ads featuring fake profiles of marketing companies that claimed to offer AI packages and access to Meta AI.
As businesses and individuals explore the best ways to use generative AI to handle corporate data, cybercriminals are also jumping on the bandwagon. This means savvy enterprise leaders must expect (and prepare for) newer and even more clever phishing attacks in the future.
How can I prevent phishing attacks in my organization?
It’s hard enough for individuals to keep phishing attacks at bay, but for organizations, the problem is compounded, meaning security operations teams have their hands full defending against the threat. Here are the most effective tactics to stop phishing attacks:
- It starts with training: The most proactive organizations have formal programs to educate users on how to spot phishing attacks and what to do if they receive one. These training sessions can be formal in-person sessions or online classes. The most progressive organizations may even “spot-check” employees by sending internally generated phishing messages to test whether they will click on a malicious link, open an attachment, or report phishing as directed, reinforcing the training lessons.
The goal of training is not to fault users for clicking on a phishing message but to give them the confidence they need to identify phishing scams proactively – or at least ask for help.
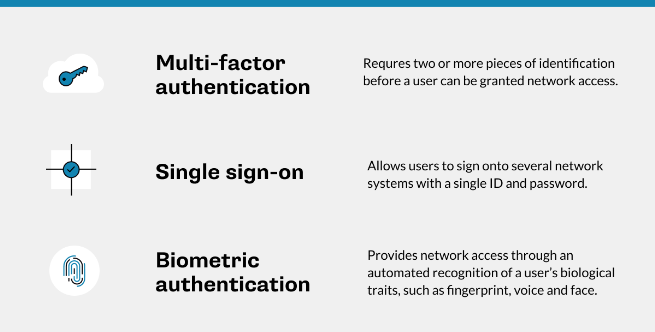
- Implement secure login methods: Multi-factor authentication (MFA), single sign-on (SSO), and biometric login requirements are key to stopping a phisher if they succeed at compromising a username and password. Without the additional security factors, they will be unable to access the network without the additional security factors.
For example, MFA requires employees to use a second (and possibly third) form of security – usually a passcode delivered via text message or through an authentication app – whenever they access network resources. (An important caveat: Phishers will also attempt to phish those added factors out of the victim.)
- Ensure anti-malware software is installed and updated: These tools are critical for stopping damage if a malicious link is clicked or an attacker successfully delivers malware to a user’s PC. Organizations must install anti-malware tools on all nodes in their network and keep software up to date. Remember, however, that software can only do so much, and multiple layers of anti-malware tools won’t provide increased protection over one well-managed tool.
- Block suspicious emails at the source: Anti-spam systems that prevent email messages with suspicious (or known spam) links in them are a massive help in keeping phishing attacks at bay.
How do I train employees to recognize phishing attacks?
In an enterprise setting, training your staff is a critical safeguard against phishing – the final line of defense if all other countermeasures have failed.
Phishing messages are more credible-looking than ever and require deeper analysis to spot fraud.
The goal of training is not to fault users for clicking on a phishing message that has made it through your corporate safeguards but to give them the confidence they need to identify phishing scams proactively – or at least ask for help if they think something might be amiss with a message. Users who fear punishment for making a mistake are less likely to report those mistakes when they (inevitably) happen.
Anyone organizing an enterprise’s training sessions should keep two major guidelines in mind:
- Training sessions should be brief and fun. No one wants to spend hours out of their day in an anti-phishing seminar. However, quick, 30-minute interactive and entertaining sessions can be incredibly effective, especially if they are undertaken regularly and feature new material each time. For example, Dell produced an 18-minute audio story with the production values of a radio drama or podcast, describing a fictional – yet typical – phishing attack and its aftermath during Cybersecurity Awareness Month this past year. (You can listen by clicking here and scrolling down to the link for “Audio story: A Modern Cyber Attack.)
- Simulations can help reinforce lessons after formal training sessions end. Organizations can craft their own faux phishing emails and periodically send them to staff to test how many are reporting messages and identify any individuals who may need additional training — all done without judgment, of course.
The training strategy itself should include these key reminders of a smart cyber defense:
- Anything can be spoofed these days. A return email address that looks to be from a legitimate website is no guarantee that the email came from one. Attackers may buy lookalike domain names or use other methods to manipulate email addresses to make them appear to be sent from trusted domains. Phishing messages are more credible-looking than ever and require deeper analysis to spot fraud.
- Any request for information, such as login credentials or financial information, is likely a phishing scam. Your organization should make it a strict policy to never send credentials or financial data through email or text.
- Hovering over webpage links is still an effective and underused way to test for legitimacy. Most email programs allow you to hover the cursor over a link without clicking on it to see where it actually leads. If there’s a mismatch between the expected link and the actual one, it’s probably a scam. Teaching employees how to hover over to identify fraudulent links is a critical step that should be part of any training program.
- If you only take away one thing, it should be this: Report before you click. “When in doubt, report” policies should be hammered home regularly.
Teach users that there’s no harm in reporting a legitimate message if they have the slightest suspicion. Also, ensure security teams respond to suspicious message notifications quickly. Users who are waiting for security ops to respond may become frustrated and decide to take matters into their own hands.
What to do if you click a phishing link
Despite all your best efforts, it’s almost inevitable that a phishing attack will make it through your defenses. When this happens, you need to act fast, utilizing an incident response playbook to help manage what happens next.
Some of the best incident response practices for phishing attacks and many other security incidents include:
- Releasing a timely and complete disclosure. If a user knows they’ve been attacked, it’s important that they come forward quickly, as time is of the essence in the aftermath of an attack. As noted earlier, this means building a guilt-free reporting process that rewards users for disclosures rather than punishing them. Find out in detail what happened leading up to the attack before you jump into action.
- Quarantining known impacted systems before malware can spread. Immediately change any exposed passwords and passwords to any potentially connected bank accounts. Report and cancel credit card numbers that may have been revealed.
- Running a full intrusion detection sweep to uncover any malware that might have made its way onto the network. By preserving the source of the phishing attack, security operations can better determine the nature of any threats that might have been introduced. Logs should be scanned for suspicious logins, URLs, IPs, and other traffic going in and out of the network since the attack.
- Taking regular backups and testing for integrity. In a worst-case scenario, data can be restored to a time before the attack was initiated.
- Performing tabletop exercises to help security teams prepare for a speedy and effective response. Teams can practice responding to phishing threats in a controlled environment by simulating real-world scenarios.
- Reinforcing training by reviewing employee mistakes. There’s no need to “make an example” of the specific individual who may have clicked the link. In fact, that’s likely to be counterproductive in the long term. However, it can be invaluable to show users what a successful phishing attack looks like — and the damage it can cause.
Watch a demo about how to use Tanium Threat Response to perform enterprise-wide threat hunting to identify, contain, and remediate threats all in one platform
How can organizations fight phishing attacks while improving the digital employee experience (DEX)?
Balancing security with a positive user experience can be challenging. Many users become frustrated with demanding security requirements, which can drive them to look for ways to bypass these measures that can introduce additional vulnerabilities and even higher security risks.
Organizations that work to improve the overall digital employee experience for users will likely find their employees more engaged and observant when it comes to email security and computer security in general.
The key to taking proactive measures against phishing techniques (and all other security measures) is to avoid interrupting the user’s workflow. Email clients outfitted with a one-button “Report this message” function or, at the very least, a dedicated anti-phishing email address where suspicious messages can be forwarded are an excellent first step.
The fewer hoops an employee must jump through to report an attack, the more likely they are to do so. Keeping attacks to a minimum is best — no user wants to spend their day filing reports. Eventually, alert fatigue will set in, and bad habits may develop.
Stepping back, organizations that work to improve the overall digital employee experience for users will likely find their employees more engaged and observant about email security and computer security in general.
Users who are less stressed out due to their day-to-day working environment will likely be more understanding of the need for security and anti-phishing measures and more willing to work toward the common goals of preventing attacks, protecting the organization, and participating as a cohesive team. Like a smart DEX program, good security hygiene benefits everyone.
Enforcing strong password policies, MFA, and providing training sessions can all disrupt users’ workflow to some extent, and they may well push back against them. However, your training messaging needs to stress that the present disruption will be far less painful than a future disruption caused by a successful phishing attack. A little pain now is better than a massive disruption later.
Phishing attacks are a pervasive threat that requires constant vigilance and proactive measures to protect against them. By leveraging Tanium’s Digital Employee Experience solution as part of their overall endpoint management efforts, organizations can gain visibility into the performance of their endpoint devices to quickly identify and remediate issues, maximize employee productivity by ensuring users have a seamless experience, and can more easily gain an understanding of employee sentiment to ensure users have the tools and knowledge necessary to identify, secure against, and avoid successful phishing attempts.
Using our platform approach, organizations empower their workforce with Tanium DEX and seamlessly integrate with Tanium Threat Response to safeguard productivity by swiftly remediating phishing threats and other cyber risks. Choose a proactive defense; choose Tanium for a resilient digital environment.
Additionally, our vision for autonomous endpoint management (AEM) takes this a step further, aiming to create a self-defending network that can detect and respond to threats in real time. Act now to fortify your defenses with Tanium’s cutting-edge technology. Together, we can outsmart the phishers and safeguard our digital future. Request a free, personalized demo or register for a Converge World Tour event near you to see it in action.




