Accenture, Google, and Tanium: Working Together to Address Enterprise Security Risks
The world of IT security has changed dramatically in the past year, but which changes really matter, and how should companies respond in order to keep their employees and data safe?
A recent Tanium webinar, “The Secrets of High-Speed Threat Detection Using Petabytes of Data,” featured experts from Accenture, Google and Tanium. They offered a bracing look at the shifting landscape for IT security, identifying new threats and offering guidance for protecting enterprise assets, even when most employees are working from home.
The webinar also included a demonstration of the joint solution of the Tanium Platform with Google Chronicle, Google’s cloud-based platform for collecting and analyzing petabytes of telemetry data in real time to detect and remediate security threats on corporate networks.
Attacks are up and attack surfaces are larger
IT security has probably changed forever as a result of so many people working from home during the pandemic, says Nick Taylor, managing director and UKI security lead for Accenture. The shift to remote work and the accompanying increased reliance on cloud services have accelerated an IT transformation that was already underway.
Now that transformation is maturing into a new paradigm of highly distributed workforces and increased reliance on partner networks. Security teams need to adjust their investments and processes accordingly, or they’ll fall victim to new forms of attack and new types of vulnerabilities.
In a world when everyone’s working from home, corporate data and devices are exposed in ways they never have been before. According to Taylor, home networks are about 3.5 times as porous as corporate networks, which means that any endpoint in a home office is at much greater risk than the same endpoint when it was in a corporate office.
Attackers are taking advantage of the chaos created by the pandemic. Taylor noted that:
- Over 60,000 domains have been registered with names related to COVID19. Many of these domains are used for phishing campaigns and other criminal activities
- Cybercriminals have impersonated the World Health Organization (WHO), offering to send consumers updates about COVID infections in their area for a low subscription fee. Through the sign-up form, the criminals gain access to credit card numbers and bank account details.
- Cybercriminals are also spreading disinformation, such as the rumor that COVID is the result of 5G networks.
- Criminals are attacking life sciences companies, stealing intellectual property, and disrupting factories and supply lines.
From industry surveys and insights from Accenture’s network of about 90 CISOs, Taylor shared these troubling numbers:
- Attack dwell times are long: often between 200 and 250 days. In that time, attackers have time to explore networks, gain access to more resources, and exfiltrate data for various types of criminal activities.
- Attack volume has doubled recently, but in Europe, the number of breaches per year has remained stable. “Security hygiene has clearly improved,” Taylor said. Otherwise, breach numbers would be rising with attack volume.
- About 40% of breaches involve third parties or partners of third parties, an increase of about 10% from the year before.
- Malicious insider attacks are on the rise. Taylor attributes this to employees feeling isolated, even alienated, from their employees as a result of working in isolation for long periods of time. Employees are worried about the pandemic affecting their jobs. Some decide to capitalize on their insider knowledge for economic gain. They might download data onto local devices, or they might sell login credentials on the Dark Web.
- About 60% of executives say their budgets are not keeping up with rising level of threats. Security accounts for only about 11% of most corporate IT budgets. In many organizations, it should account for more.
Accenture’s advice? First, focus on people being the first line of defense. Give employees the training they need to reduce the chance of them making dangerous mistakes, and help them feel part of the company overall even while they’re working from home.
Also, take advantage of solutions like that offered by Tanium and Google for gaining visibility into endpoint threats, so your IT organization can respond quickly when threats arrive.
Detecting and remediating endpoint threats with Tanium and Google Chronicle
Organizations interested in following Accenture’s advice can take advantage of a new Tanium and Google solution for unified endpoint management and Zero Trust initiatives.
This new offering, sold by Tanium, integrates Tanium’s Threat Response with Chronicle, Google Cloud’s security analytics platform, and helps enterprises detect, investigate and scope advanced, long-lived attacks (advanced persistent threats or APTs).
The integrated offering is especially useful for helping security analysts hunt for advanced persistent threats — threats that might be lingering undetected on a network for hundreds of days.
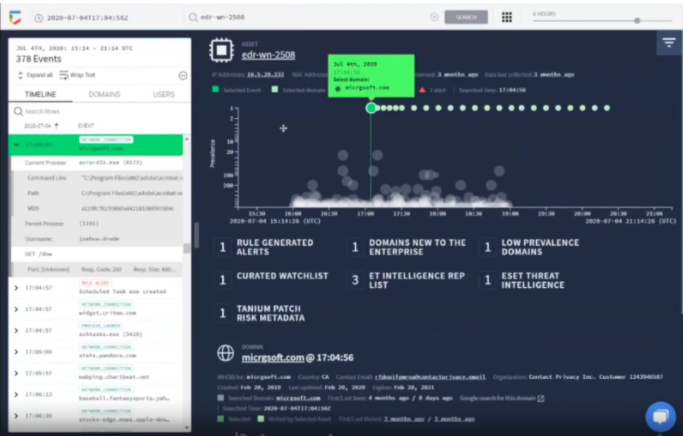
Figure 1. Through its integration with the Tanium Platform, Google Chronicle helps security analysts explore endpoint telemetry data along with updated threat intelligence feeds. Analysts can quickly mitigate threats involving remote endpoints, even in a WFH environment.
Google Chronicle stores a petabyte of endpoint telemetry data streamed from Tanium agents, providing an entire year’s worth of data. Using this massive store of data, analysts can quickly correlate events to identify attacks that would otherwise evade detection. Chronicle’s search technology returns query results instantly, so analysts can investigate and characterize threats as quickly and possible.
For example, a security analyst can use Tanium and Chronicle to investigate activities such as a DNS request for a suspicious domain and to discover any related activity going back one year.
Once the request for the suspicious domain is identified, the analyst can use the Tanium platform to immediately quarantine the affected endpoint, containing the threat.
Watch the webinar with Accenture, Google, and Tanium to learn more about how you can protect your remote workforce from cybercrime.
To learn more about Tanium’s partnership with Google, read our recent press release.




