Update New Dell PC Bugs Now to Avoid Potential Compromise
Five high-severity flaws have been found in hundreds of millions of devices worldwide
May 4 is meant to be a day when fans of all things Star Wars get to celebrate the sci-fi media franchise. But system administrators were busy with something more urgent after Dell released a patch for five “high severity” flaws impacting various desktops, laptops, notebooks and tablets.
Although not remote code execution (RCE) vulnerabilities, the bugs could still cause a denial of service or leak information without the system owner’s permission. Once again, the spotlight is on organizations’ vulnerability and patch management processes.
Here’s what you need to know and how Tanium can help.
What are the flaws?
First discovered by SentinelLabs, the vulnerabilities exist in Dell’s firmware update driver v2.3 (dbutil_2_3.sys) dating back to 2009. Given that they have been undisclosed for 12 years, the vulnerable driver has since been installed on hundreds of millions of Dell products.
All five flaws are tracked as CVE-2021-21551, with a CVSS score of 8.8. Here are the details:
- Memory corruption — CVE-2021-21551: Local Elevation of Privileges #1
- Memory corruption — CVE-2021-21551: Local Elevation of Privileges #2
- Lack of input validation — CVE-2021-21551: Local Elevation of Privileges #3
- Lack of input validation — CVE-2021-21551: Local Elevation of Privileges #4
- Code logic issue — CVE-2021-21551: Denial of Service
How could attacks work?
The good news is that these aren’t RCE bugs, so they can’t be used to directly compromise a system.
But the concern is that an attacker who has managed to gain remote access via a different vulnerability exploit is able to escalate privileges locally using the first four bugs to run code in kernel mode. This tactic could be used to bypass security tools running in your environment.
Organizations have a small window of opportunity to remediate, since there are no reports of the bugs being actively exploited in the wild.
However, given the vast number of devices potentially affected, it would seem likely that threat actors will soon turn their attention to developing exploits for these vulnerabilities.
How Tanium can help
As we’ve discussed before, it can take just hours following the release of a vendor patch before threat actors produce proof-of-concept malware. That doesn’t give you long to find and fix any vulnerable endpoints.
Given the distributed nature of today’s workforce, that can be increasingly challenging — unless you have platforms like Tanium to provide visibility and control at speed and scale.
On Tuesday, Dell released an update utility to mitigate CVE-2021-21551. Organizations must therefore complete two essential tasks: find the issue and remediate.
Here are the Tanium solutions to help you do just that:
- Tanium Interact allows you to quickly and easily query whether you have vulnerable endpoints (e.g., Dell computers featuring CVE-2021-21551) and receive answers in real time, across thousands or even hundreds of thousands of IT assets.
- Tanium Deploy reduces complexity and enhances business resilience for IT operations teams. It enables you to install, update or remove software across your environment at speed and scale.
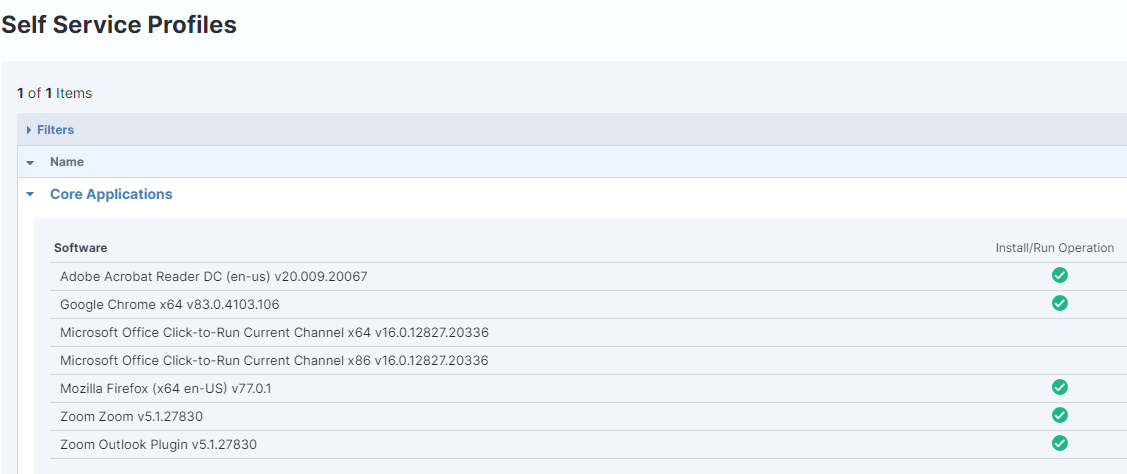
With Tanium Deploy, end users can select and deploy the software they want while you control the approvals
- Tanium Enforce allows organizations to simplify, centralize and unify policy management of end-user devices. This helps eliminate and mitigate vulnerabilities and business risk.
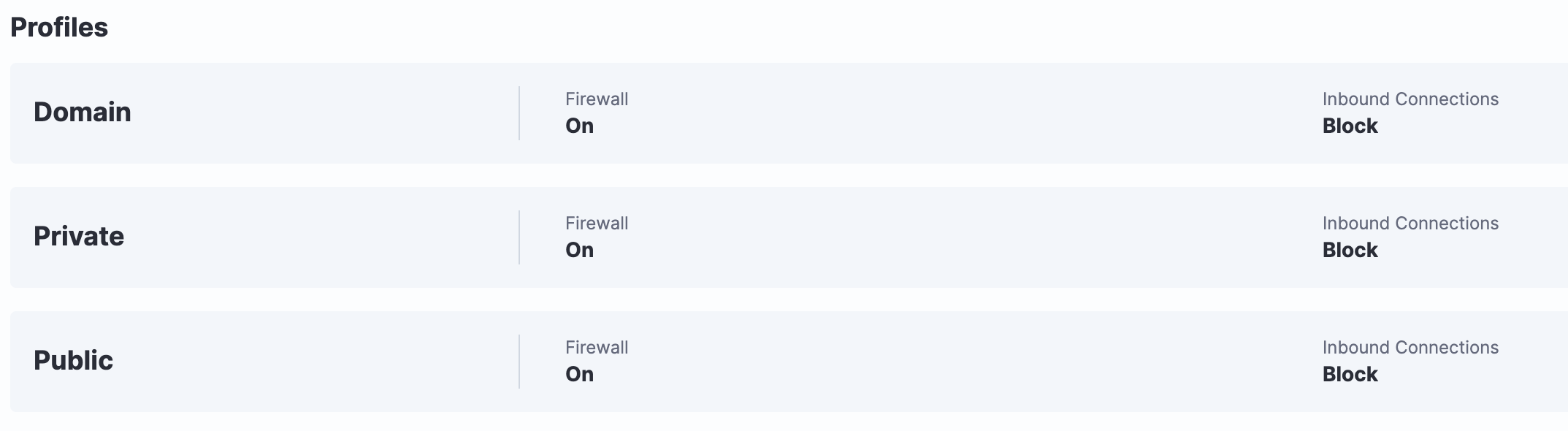
Monitor and maintain firewall policies on endpoints with Tanium Enforce
Here’s what to do:
- Use Tanium Interact to find any affected endpoints as outlined in our Community article.
- Use Tanium Interact to deploy the Dell Security Advisory Update – DSA-2021-088 utility via a new Tanium core package.
- Create a Tanium Enforce remediation policy to delete the vulnerable files.
- Use Tanium Deploy to create software packages to update any existing Dell driver utilities. This prevents the vulnerable driver file from being reintroduced.
You can read more technical details on the Community post here. Vulnerabilities are a way of life today. It’s how you respond to them that matters.
Learn more about how the Tanium platform can help find and remediate vulnerabilities.



