What is the MITRE ATT&CK® Framework?
Insights about getting started with the MITRE ATT&CK framework, including real-world examples for integrating and improving detection capabilities
MITRE ATT&CK is a comprehensive framework that serves as an assessment tool and knowledge base for understanding the behavior of cyber attackers. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
The framework provides detailed guidance on adversary tactics and techniques based on real-world observations of common cyberattacks. It establishes a shared language to describe the tactics and techniques used by threat actors and threat intelligence needed to counter new cyber threats effectively, which streamlines collaboration efforts around creating strong defense and mitigation plans.
At Tanium, our mission to keep our customers safe and secure means our IT security organizations must operate according to the highest cybersecurity standards. To achieve this, our cybersecurity team has been working to adopt the MITRE ATT&CK framework to help us improve and measure the effectiveness of our threat detection capabilities.
In this post, we’ll provide an overview of the MITRE ATT&CK framework, including key terms, benefits, lessons learned implementing it, and potential challenges you should know about.
- What is MITRE ATT&CK?
- Common MITRE ATT&CK definitions
- Benefits of the MITRE ATT&CK framework
- 5 steps for integrating the MITRE ATT&CK framework into security operations
- Lessons learned: How to successfully apply the MITRE ATT&CK framework
- MITRE ATT&CK framework challenges
- How to get started
What is MITRE ATT&CK?
Created by the MITRE Corporation in 2013 to document advanced persistent threats used against Windows enterprise networks, MITRE ATT&CK is a rapidly growing open-source knowledge base of adversary behavior phases, known as tactics, and the specific actions they might take, or techniques.
The framework’s adaptability is evident in its organization into several matrices, each representing different stages of an attack lifecycle. These stages include Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, and Impact, ensuring comprehensive coverage.
MITRE ATT&CK covers a wide range of platforms, including Windows, macOS, and mobile, as well as cloud environments and control systems, and it is used by both private and government organizations alike.
The framework is an essential resource for the cybersecurity community by offering methodologies and strategies to better detect, respond to, and mitigate cyber threats. For example, security professionals can use MITRE ATT&CK to evaluate and develop cybersecurity products and services to ensure they’re effective against known adversary behaviors and develop threat models to identify vulnerabilities and enhance defenses.
By leveraging this framework, organizations can improve their security strategies and overall security readiness.
Common MITRE ATT&CK definitions
The MITRE ATT&CK framework is constantly updated with the latest tactics, techniques, and procedures (TTPs) utilized by threat actors throughout each stage of a cyberattack. Each component is essential to the framework, so let’s drill deeper to understand these specific terms and their roles better.
To note: When we mention the MITRE ATT&CK framework, we’re referring to the adversary techniques and tactics included in the MITRE ATT&CK Enterprise Matrix.
What are MITRE ATT&CK tactics and techniques?
Described as the why behind the techniques, there are currently 14 Enterprise tactics used to categorize the reason for performing certain actions. In addition to these tactics, the framework lists around 200 Enterprise techniques or how adversaries could achieve their goals.
Let’s review the 14 Enterprise tactics and types of techniques adversaries may use:
- Initial access involves gaining an entry point into a network.
- Execution involves running malicious code within the compromised system.
- Persistence involves maintaining their foothold in a system for ongoing exploitation despite restarts, changed credentials, and other interruptions that could cut off their access.
- Privilege escalation involves gaining higher-level permissions on a system or network to gain extensive control over the system, change configurations, execute commands, or access restricted data.
- Defense evasion involves avoiding detection by security defenses to maintain access to a system without being discovered by the defenders or security solutions.
- Credential access involves stealing credentials like passwords, tokens, or keys to allow them to masquerade as legitimate users, escalate privileges, and move laterally within the network.
- Discovery involves gaining knowledge about the system and internal network by identifying valuable resources, understanding security settings, and mapping the network to plan further operations.
- Lateral movement involves techniques that adversaries use to move through a network by gaining access to other systems after the initial compromise.
- Collection involves gathering data of interest to extract valuable information from the compromised system.
- Command and control involves establishing a means to communicate with the external command and control servers to receive instructions, exfiltrate data, or manipulate compromised systems.
- Exfiltration involves stealing data from a network after establishing a presence to extract sensitive information from the compromised system for use or exposure outside the organization.
- Impact involves disrupting, compromising, or destroying data and systems to cause harm to the organization’s operations and reputation.
- Reconnaissance involves gathering information about their targets to prepare for other operations.
- Resource development involves establishing resources that threat actors can use to support operations throughout the attack lifecycle.
Techniques: Spear phishing emails, exploiting public-facing applications, and using stolen credentials
[Read also: What is Business Email Compromise (BEC)? The rising costs of BEC attacks]
Techniques: Command and script interpreters, user execution, and exploiting software vulnerabilities to execute code without user interaction
Techniques: Creating or modifying system processes, adding login items, and using web shells
Techniques: Exploiting system weaknesses, configuration oversights, and programmatic errors to obtain elevated access to resources usually protected from an application or user
Techniques: Disabling security software, obfuscating or encrypting data and scripts, and using stealthy techniques to blend in with everyday traffic
Techniques: Input capture, brute force attacks, and exploiting system or service credentials
[Read also: What is Active Directory security? Risks and best practices]
Techniques: System and network reconnaissance, directory listings, and querying system configurations or services
Techniques: Using valid accounts, remote services, or remote desktop protocols to move from one system to another within the same network
Techniques: Collecting sensitive documents, capturing user input, and harvesting data that can be used or exfiltrated for further operations
Techniques: Using custom protocols, web traffic, or domain generation algorithms to maintain communication while avoiding detection
Techniques: Transferring data to cloud storage, using compression to disguise and reduce the size of the data, or using automated exfiltration processes
Techniques: Data destruction, defacement, and resource hijacking
Techniques: Social engineering, network scanning, and researching public information to understand the target environment better
Techniques: Acquiring and compromising accounts, developing malicious payloads, and setting up infrastructure such as command and control servers
What is the MITRE ATT&CK Matrix?
You’ll often see the terms MITRE ATT&CK Matrix and MITRE ATT&CK framework used interchangeably to describe the same catalog of attack information. However, the MITRE ATT&CK Matrix visually represents the tactics and techniques an adversary can use to comprise the framework.
There are currently three distinct MITRE ATT&CK Matrix versions that align with the different adversarial techniques and tactics used for each:
- Enterprise MITRE ATT&CK Matrix for enterprise networks
- Mobile MITRE ATT&CK Matrix for mobile devices (like iOS and Android operating systems)
- Industrial Control System (ICS) MITRE ATT&CK Matrix for ICS networks
As these matrices receive regular updates, you should refer to the MITRE website for the latest versions.
Cyber Kill Chain vs. MITRE ATT&CK framework
When researching the MITRE ATT&CK framework, you may encounter another framework — the Cyber Kill Chain. While the Cyber Kill Chain and MITRE ATT&CK framework are both models used to describe and analyze the phases of a cyberattack, they approach the topic from different perspectives.
The Cyber Kill Chain, developed by Lockheed Martin, outlines the stages of an attack from early reconnaissance to the final objective, typically data exfiltration or system compromise. It emphasizes a linear progression through several stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives.
On the other hand, the MITRE ATT&CK framework is a more granular and comprehensive model that describes the tactics and techniques adversaries use at each stage of their attack. It is not strictly linear and allows for a more complex understanding of an adversary’s behavior. The framework includes many techniques that can occur at various stages of an attack, providing a detailed view of the adversary’s actions.
Think of the Cyber Kill Chain as a high-level overview of an attack lifecycle, while the MITRE ATT&CK framework provides a detailed, tactical-level view of the adversary’s behavior and techniques.
Benefits of the MITRE ATT&CK framework
Like most security teams, we need help determining where to invest finite resources and how to measure the success of our threat detection program. We required a mechanism to identify gaps and assign corresponding risks in our existing detection strategy to address these questions. In doing so, we discovered various ways we can apply the MITRE ATT&CK framework to provide a solution to our problem.
Here are some of the characteristics of the MITRE ATT&CK framework that we find most valuable:
- It’s actionable. We view MITRE ATT&CK through two different lenses: strategic and tactical. From a strategic perspective, we can use the framework as a part of a security program to assess risk, prioritize, or measure progress.
- It’s behavior-focused. MITRE ATT&CK stood out most for us for its technique-focused approach in describing post-compromise adversary behavior. Developing detection that identifies the behaviors of software or adversaries is challenging but a more durable form of detection.
- It’s risk-informed. We continuously prioritize based on risk from the order in which we triage and investigate alerts to the urgency of patches applied to the systems we engineer. This approach works well when prioritizing a list of known alerts or to-dos, but it doesn’t help to identify or prioritize the tasks you don’t know exist.
Why this matters: By taking a tactical approach and identifying the specific techniques outlined in the framework, our organization can improve our ability to detect malicious activities.
Why this matters: Instead of detecting malicious software by hash, we can increase our ability to detect malicious software by describing its behavior. Let’s use process injection as an example. In this use case, attackers can swap out different malware or software to inject their malicious code into a process, thwarting atomic indicator detection, but the underlying behaviors still exist. The same applies to people (attackers).
Why this matters: When it comes to detection, MITRE ATT&CK provides a straightforward way to identify gaps by contextualizing them within the adversary’s lifecycle. It also helps us assess the risks of those gaps and ultimately inform better prioritization for our practitioners.
5 steps for integrating the MITRE ATT&CK framework into security operations
Here are the steps we took, which you can apply to your organizations:
- Start with a well-known subset of detection
We began this journey by mapping some Tanium product module components used in our IT environment. Like our customers and probably most organizations, our security team uses a suite of tools, some of which provide us with out-of-the-box detection capabilities.
- Align on requirements
Unfortunately, there isn’t a magic solution (yet) that allows you to import your detection and map it to the ATT&CK components in a pretty interface. However, you can use tools to interact with the ATT&CK API to export data in different formats and views, including CSV.
- Create the mapping
We began with a common approach we have seen others take — using a spreadsheet to get started quickly and for easy collaboration. With a collaborative mapping initiative underway, we wanted to design visualizations to identify detection deficiencies aligned with the operating system and adversary lifecycle.
- Identify gaps
We started generating reports based solely on frequencies. While these reports obviously didn’t tell a complete story, they helped draw our attention a few potentially problematic areas: - Prioritize and measure success
While we had lofty ideas of a complicated system to track the mapping, we wanted to make sure we didn’t try to boil the ocean. By starting small and using MITRE ATT&CK as an actionable “punch list” for building and improving detection capabilities, we could make iterative refinements to our process and show a return on investment for our time right away. With these reports in hand and the ability to generate more, we can measure and prioritize based on risk, assign ratings, estimate effort, and report our success.
We recommend starting with something well-known rather than trying to understand and document someone else’s detection logic, especially when most solutions do not expose their native detection mechanisms to customers. For example, this could be internally developing logic monitoring log events within a Security Information and Event Management (SIEM) system.
[Read also: What is security automation? Benefits, importance, and features]
Mapping can be tedious and time-consuming, so we needed to define the basic requirements for the information we wanted to capture as a team in hopes that we wouldn’t have to go back through and add more to it later.
Here are the mapping components we chose:
– Visibility into operating systems: At Tanium, we operate a mixed environment of Linux, Mac, and Windows, so it was essential for us to identify gaps by operating systems. Since MITRE ATT&CK already maps techniques to operating systems, this job was partially complete for us. We only needed to ensure we could capture an operating system component to the detection we mapped.
– Actionability: Not all our detection is created equal. For example, some alerts are actionable for analysts, while others require additional correlation, data sources, or analyst intervention before becoming actionable. Capturing actionability will help us weight prioritization.
– Modular and flexible: We needed our mapping to be flexible enough to evolve with newly created ATT&CK techniques or detection.
– Collaborative: We needed to create a repeatable process that enabled our security team and other teams within Tanium to collaborate on the mapping.
While we found the framework intuitively maps higher-level MITRE ATT&CK tactics and contains linkage and context to software used by adversaries and adversary groups, we chose to separate the MITRE techniques, a list of detection components, and the mapping between the two into different sheets to keep this mapping as modular as possible. This way, if MITRE updates or adds new attack techniques or we do the same to our detection, we only need to adjust in one place.
MITRE ATT&CK mapping examples
Figures 1-4 below illustrate how we set up each spreadsheet.
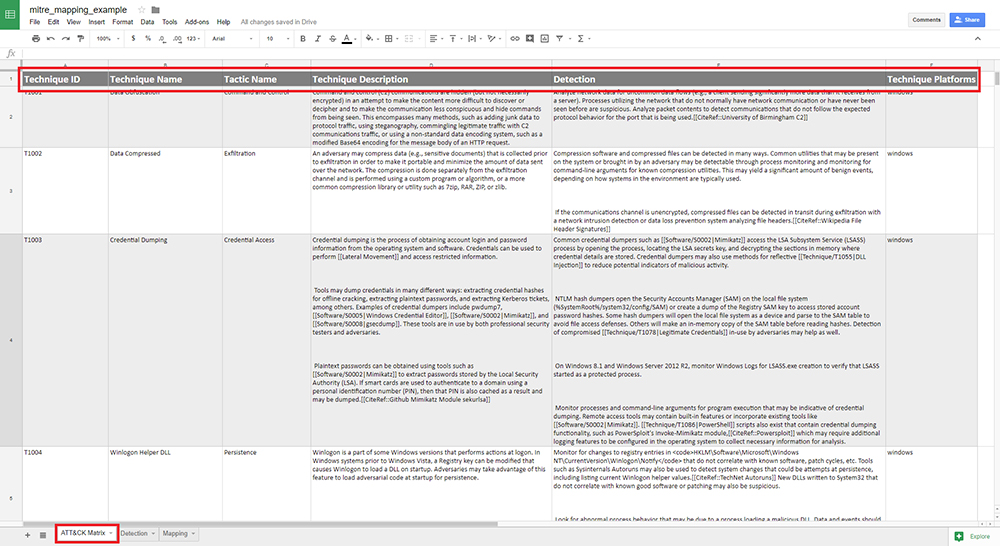
Figure 1 shows the MITRE ATT&CK Matrix sheet of the spreadsheet. Here, we used ATT&CK’s API to generate a CSV of each technique, added some additional context, and where we will update or add techniques as MITRE releases them. In this case, we included the technique name, ID, description, and details, including detection methods and corresponding tactic names (exfiltration, credential access, etc.).
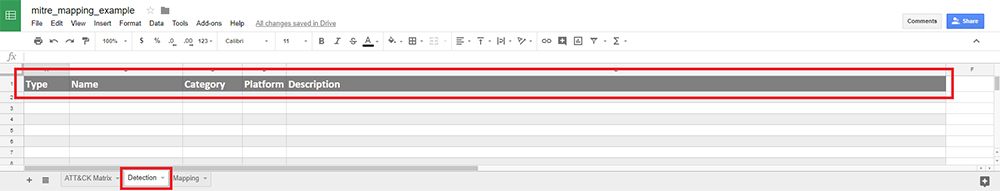
Figure 2 shows our detection template, where we track and maintain our detection capabilities. Like the ATT&CK Matrix in Figure 1, we included fields to help us identify key detection components: the type, name, category, platform, and description. We have redacted the actual detection components from this screenshot.
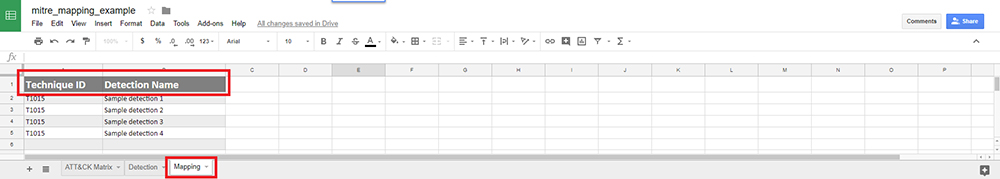
Figure 3 shows the mapping between the ATT&CK Matrix in Figure 1 and the detection template in Figure 2. We chose two values we do not expect to change often as our “primary keys” — the ATT&CK technique ID and our detection name. These are the only two values we add to the mapping manually.
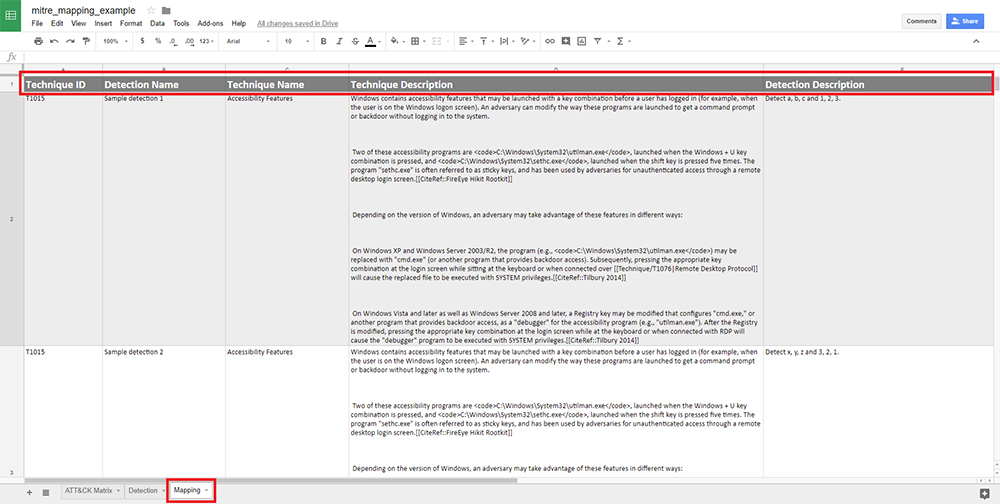
Figure 4 shows how we used the vertical lookup formula to populate additional columns based on our two primary key fields and how we can add further context to the mapping.
– Detection by tactics: To estimate detection coverage through the post-compromise attack lifecycle, we counted the number of detection mechanisms mapping to techniques for each tactic.
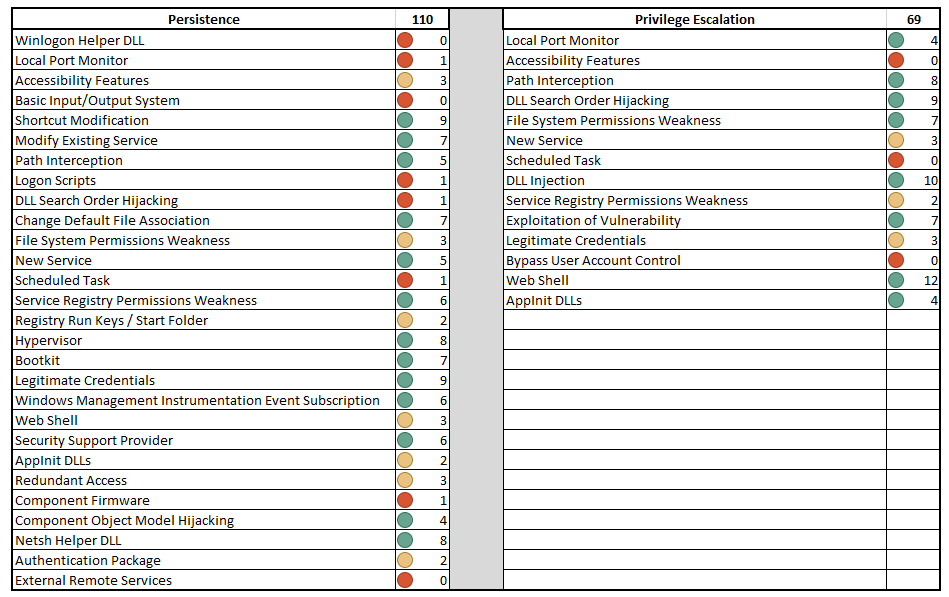
– Detection by techniques: For a more granular view, we estimated our detection coverage for each technique. Unlike detection by tactic, this provided us with a unique lens through which to quantify our detection capabilities. See Figure 5 below for an example report showing counts by tactic and by technique for the persistence and privilege escalation tactic. Note: The numbers provided in this example have been randomized.
– Detection by operating system: To distinguish further between our Mac, Windows, and Linux detection, we organized detection by tactic and techniques into groups for each operating system. This detection method allowed us to identify those tactics or techniques with a heavy detection bias toward an operating system. See Figure 6 below for an example report identifying detection gaps by operating system.
We also use these reports to visualize progress and advocate for necessary changes. By providing a structured and detailed overview of the threat landscape and our security posture based on the MITRE ATT&CK framework, organizations can make more informed decisions on resource allocation, risk management, and strategic planning needed to maintain a proactive and resilient security strategy and ensure defenses are aligned with current and evolving cyber threats.
For the Cybersecurity and Infrastructure Security Agency (CISA), understanding adversary behavior is often the first step in protecting networks and data. The success network defenders have in detecting and mitigating cyberattacks depends on this understanding.
Lessons learned: How to successfully apply the MITRE ATT&CK framework
Since the MITRE ATT&CK framework is still evolving, we hesitate to identify these lessons as best practices. Instead, we share our experience to provide guidelines to help you and your team explore this framework.
Using these elements and steps to identify a path forward, we tactically started improving our detection capabilities using MITRE ATT&CK as a punch list. Simultaneously, we wanted to take a step back and better understand our current state so we could begin to develop metrics, assess risks, and incorporate MITRE ATT&CK into our detection planning and goals.
Here’s what we learned.
Begin at the beginning: What does your security team work on, and in what order?
The Tanium security team categorizes our work as either operational or enhancement-based. Operational, or run-focused work, tends to consist of shorter-term tasks, such as break fixes, security operations functions, and incident response. Enhancement, or build-focused work, tends to consist of longer-term projects aimed at improving the ability to perform operations.
What we discovered — and is likely happening at your organization — is that our security team was deprioritizing enhancement projects to handle operational needs. While keeping the lights on seemed intuitive, we wanted to avoid falling into a perpetual loop of running day-to-day operations without making substantive improvements that increased our effectiveness and efficiency.
By analyzing risk associated with known gaps in detection capabilities, our team hoped to identify higher-value alerts with a lower operational burden.
Can the mapping be improved?
Focusing on mapping internally developed detection capabilities to MITRE ATT&CK made the most sense as a starting point for us. However, as we expand, we find that we are mapping thousands of different detection components from various tools to more than 100 techniques. In most cases, this is a many-to-many mapping relationship.
While our spreadsheet began as a suitable place to start, it’s now getting tough to handle. We noticed minor data quality issues between the number of different mappings and the various contributors, such as duplicate mappings or formatting inconsistencies. It is cumbersome to flip between multiple sheets, and we’re wasting time copying and pasting content from one field to another. Some of the visualizations and reports we want to develop on the data, mainly those showing linkage, could be more challenging to build and maintain within the constraints of a spreadsheet.
[Read also: Are cybersecurity analytics missing from your security strategy?]
We have been improving our ability to store and maintain our mapping data while experimenting with new visualizations and usage for the data. Having built our spreadsheet in a modular format, manipulating or working with the data in another medium was straightforward. We could import our detection, techniques, and mapping into a SQLite database by saving each sheet as a CSV and applying some light Python. The SQLite database was more manageable for us to pass around and provided an easier way to manipulate the data, albeit requiring some scripting experience.
With the data sitting in a database, we can now try to use a web application front end to visualize and pivot between the data, aid in data quality and validations, and make adding or updating mappings even quicker without the need for scripting skills. Also, linking to the MITRE ATT&CK API lets the application notify us of new techniques or sub-techniques and automatically import them.
How do you measure success?
Metrics play a vital role in helping our team assess its operational components. We measure alert distribution, volume, outcome (e.g., true positive, false positive, defective alert, etc.), and time to detect, triage, and resolve an incident, among other factors.
While these metrics help us identify problems and trends based on what has already happened and allow us to track how we improve over time, they do not provide insight into the maturity of our program or help us identify what the team might be missing. By creating the right benchmark to assess our detection capability, we can carefully track, assess risks, and ultimately communicate our evolution of detection capabilities.
Measuring coverage beyond frequency analysis has proven challenging. In the initial stages, we relied on frequency analysis to identify and prioritize those MITRE ATT&CK techniques where we had little or no threat detection capabilities.
As our detection capabilities expand, the detection mapped to MITRE ATT&CK techniques will also grow. Still, high frequency does not necessarily indicate we have thoroughly and adequately addressed that technique. As such, we are starting to experiment with different mechanisms to check within a technique to identify gaps and attempt to quantify mechanisms for coverage, including indicators to distinguish between higher fidelity and lower fidelity detection.
Is the framework working?
When we design detection, we also create test use cases. We execute these test cases when the detection is created and periodically execute those tests manually over time. We supplement these test cases with red teaming exercises to test narrow cases designed for a single detection and identify attacker behaviors we effectively or ineffectively detected. Now that we have incorporated MITRE ATT&CK as a detection framework, we can shift focus to designing scripts and test cases to simulate different MITRE ATT&CK techniques.
By leveraging the power of the Tanium platform, we can also automate and randomly distribute these ATT&CK evaluations throughout our environment regularly and begin to introduce a continuous testing process for our security program. Cyb3rWard0g already has a great start for threat hunting with the ThreatHunter-Playbook, as does Uber with the cyber adversary simulation tool Metta. Both projects take approaches to aid in developing and testing detection aligned to the MITRE ATT&CK framework that can be leveraged as a part of a continuous testing program and to assess security operations center (SOC) maturity.
Having that ironed out, we visualized expanding the mapping to other detection capabilities and partner solutions we use.
MITRE ATT&CK framework challenges
While instrumental in shedding light on common adversary behaviors and methods, it’s important to note that the MITRE ATT&CK framework is not a security IT compliance standard like PCI DSS, HIPAA, or ISO 27001, and not a replacement for following cyber hygiene best practices.
Viewing the MITRE ATT&CK framework through the lens of a compliance checklist can actually impede the effectiveness of your overall security strategies, particularly if it leads to misallocating limited resources in an attempt to mitigate every technique listed. While solving for every ATT&CK technique is an admirable goal, it just doesn’t stand up to a cost-benefit analysis.
For example, let’s look at Technique ID T1012, Query Registry, in which adversaries may interact with the Windows Registry to gather information about the system, configuration, and installed software. To date, the MITRE ATT&CK website lists more than 100 threat actor groups, malware families, or utilities that may query an unknown number of registry keys for T1012. Some referenced resources cite registry keys that may be modified, but many don’t name specific keys that will be queried.
While organizations can already gain insight into process execution using an endpoint management solution to make it easier to detect targeted reg.exe queries, what about attacker tools that use APIs to query registry keys and values? Should security teams record the tens of millions of registry queries happening daily per endpoint for every Windows endpoint in the enterprise? What will it cost in bandwidth, storage, and compute time to analyze the data? And what analysis is the right analysis?
Given that not all outliers are malicious and not all commonly occurring queries are benign, the value of having exhaustive coverage for T1012 reinforces using the MITRE ATT&CK framework as a guide for understanding threats rather than a prescriptive compliance mandate and the importance of taking a risk management approach to successfully mitigate many of the techniques listed by improving your overall security controls, initiatives, and technologies.
How to get started
We found that the MITRE ATT&CK framework is flexible, actionable, and aligned with our team’s behavior-focused detection strategy. By building a process to map between our detection and the MITRE ATT&CK framework, we laid a solid foundation to build upon. While we still have a lot of initial mapping until we reach a maintenance state, we have already seen a return on our investment with basic reporting. As the mapping continues to evolve, we will build more reports to address more questions and expand use cases.
Applying this recent and evolving framework has taught us a great deal about improving our threat detection capabilities, and we hope our insights will help you achieve your cybersecurity needs.
Using Tanium to leverage the MITRE ATT&CK framework can help your organization better understand what adversaries are doing, prioritize threats, and ensure the best mitigations are in place by effectively remediating endpoint vulnerabilities to improve security posture.
Tanium gives the unique power to secure, control, and manage millions of endpoint devices within seconds with unprecedented speed, scale, and simplicity. Security and IT operations teams now have complete and real-time data on the state of endpoints at all times to more effectively protect against modern-day threats and realize new levels of cost efficiency.
Learn about our vision for helping organizations solve previously unsolvable endpoint security challenges through Autonomous Endpoint Management (AEM).
Additional MITRE ATT&CK framework insight from Pricewaterhouse Coopers (PwC)
We have worked closely with our partners at PwC for years to build endpoint detection and response (EDR) service offerings for our customers. PwC has also provided more information about the application of the MITRE ATT&CK framework and how they leveraged Tanium Signal to enhance their detection capabilities by explaining the importance of orchestration in building a strong EDR practice.