What Is Multifactor Authentication (MFA)?
Multifactor authentication is a powerful security method that adds a critical layer of protection to your digital identity.
Rather than relying solely on a password—a single point of failure—multifactor authentication, or MFA, requires users to verify their identity using two or more distinct factors. This layered approach ensures that even if one credential is compromised, unauthorized access to your account is still blocked.
UPDATE: This post, originally published on November 22, 2022, has been refreshed to reflect the latest best practices in multifactor authentication, including new insights on cloud-based MFA, adaptive authentication, and how these technologies support Zero Trust strategies.
In today’s cybersecurity landscape, passwords alone are no longer sufficient. Phishing, credential stuffing, and brute-force attacks have made single-factor authentication a liability. That’s where MFA comes in—adding layers of protection and becoming a cornerstone of any Zero Trust strategy.
These factors fall into different categories: something you know (like a password), something you have (like a passcode or software token—such as those generated by authenticator apps like Google Authenticator or Microsoft Authenticator that provide time-based one-time passwords (TOTPs) without requiring physical hardware, or something you are (like a fingerprint scan).
MFA empowers users by offering multiple ways to prove who they are, making it significantly harder for malicious actors to impersonate them. For example, a stolen password alone won’t be enough if the attacker doesn’t also have access to your phone or fingerprint. But MFA isn’t just a best practice—it’s a foundational element of modern security strategies that protects accounts, strengthens identity verification, and builds trust across systems and services.
This guide breaks down what MFA is, how it works, the different types, and how to implement it effectively. Whether you’re just getting started or scaling across a complex environment, you’ll find actionable insights to help you get it right.
- Types of multifactor authentication
- MFA vs. 2FA: Understanding the difference
- How multifactor authentication works
- The factors of multifactor authentication
- Why multifactor authentication is essential for cybersecurity
- Challenges and considerations for MFA adoption
- Passwordless MFA: The future of authentication
- How Tanium supports effective access management with real-time device visibility
- Frequently asked questions about MFA
- Related resources
See how Tanium enables Zero Trust security
across your enterprise
Types of multifactor authentication
MFA types vary based on the number and nature of authentication factors, such as passwords, biometrics, and smart devices.
Two-factor authentication (2FA)
2FA, the most widely adopted form of MFA, requires users to verify their identity using two distinct types of credentials—typically something they know (like a password) and something they have (like a one-time code from an authenticator app or SMS). This layered approach significantly reduces the risk of unauthorized access, even if a password is compromised.
To note: While SMS-based 2FA is better than no MFA, it is more vulnerable to interception and SIM-swapping attacks than app-based or hardware-based methods.
2FA is especially effective for protecting online accounts and critical systems such as email, cloud platforms, and financial services, where a single stolen password could lead to serious breaches. For example, logging into your work email might require your usual password plus a six-digit code from Microsoft Authenticator on your phone, making it much harder for attackers to gain access remotely.
2FA balances usability and additional security, making it a smart first step for organizations looking to strengthen access controls without overhauling their entire authentication infrastructure. It’s simple, effective, and a no-brainer for any organization still relying on passwords alone.
|
Pros
– Stronger protection against phishing and credential theft
– Easy integration with most modern apps and services – Increased user confidence and compliance with security standards |
Cons
– Slightly slower login experience
– Dependence on a secondary device (e.g., phone) – Potential user frustration if access to the second factor is lost |
|---|
Three-factor authentication (3FA)
3FA builds on the foundation of two-factor authentication by adding a third, distinct layer of identity verification, enhancing access management for high-risk environments—typically a biometric factor such as a fingerprint, facial recognition, or retina scan. This approach combines:
- Something you know (like a password)
- Something you have (like a mobile device or security token)
- Something you are (like a biometric trait)
3FA is most effective in environments with elevated security demands, such as government systems, healthcare networks, financial institutions, and critical infrastructure, where the consequences of unauthorized access are severe. It’s also increasingly used in remote work scenarios where sensitive data is accessed outside the corporate perimeter.
[Read also: What is Active Directory security? Risks and best practices]
3FA is ideal when security stakes are high, and user experience can be balanced with risk. While not necessary for every login, it’s a powerful safeguard for securing mission-critical systems and confidential data.
Imagine accessing a secure medical records system. You enter your password, approve a push notification on your phone, and scan your fingerprint. Even if a cybercriminal steals your password and phone, they still can’t access the system without your biometric data.
|
Pros
– Provides the highest level of assurance among common MFA methods
– Strong defense against phishing, credential theft, and device compromise – Helps meet stringent compliance requirements (e.g., HIPAA, FIPS, CJIS) |
Cons
– More complex and costly to implement and maintain
– Can introduce user friction or accessibility challenges – Biometric data, if compromised, cannot be changed like a password, posing long-term identity risks if not securely stored and encrypted |
|---|
Adaptive MFA
Adaptive or risk-based MFA dynamically adjusts authentication requirements based on contextual signals. Contextual signals may include device fingerprinting, login velocity, browser metadata, and historical user behavior.
Instead of applying the same level of friction to every login attempt, adaptive authentication evaluates risk in real time and only prompts for additional verification when something seems unusual.
Adaptive MFA is especially effective in hybrid or remote work environments, where access management must adapt to varying risk levels, and users access systems from a variety of locations and devices. It also excels in high-compliance industries or dynamic threat landscapes, where real-time risk detection and response are critical to maintaining secure access.
|
Pros
– Reduces friction for users by minimizing unnecessary prompts
– Detects and responds to real-time anomalies like unusual login behavior – Scales easily across hybrid and remote environments with broad signal support |
Cons
– Requires complex integration with multiple data sources
– May confuse users due to inconsistent prompt behavior – Can misclassify legitimate or malicious activity due to imperfect risk scoring |
|---|
Biometric MFA
This type of MFA relies on inherent traits such as fingerprints, voice recognition, or retina scans. It is one of the most secure forms because biometrics are difficult to replicate or steal.
[Read also: The new biometrics dilemma – will they make us safe or sorry?]
Biometric MFA is especially effective in tightly controlled environments or where password fatigue and device loss are common concerns. For example, a healthcare provider might use fingerprint authentication to ensure that only authorized staff can access patient records, eliminating the need to remember or manage multiple credentials.
|
Pros
– Extremely difficult to forge or steal compared to passwords or tokens
– Convenient and fast for users—no need to remember or carry anything – Ideal for environments requiring hands-free or rapid access (e.g., hospitals, manufacturing floors) |
Cons
– Requires specialized hardware, which may not be universally available
– Privacy concerns around storing and managing biometric data – Can be affected by physical changes (e.g., injury, illness) or environmental conditions (e.g., gloves, lighting) |
|---|
Cloud-based MFA
This method delivers MFA via cloud services, making it easy to integrate across hybrid environments and remote users. It typically includes Single Sign-On (SSO) and integrates with identity providers.
Cloud-based MFA is built for the way we work now—remote, hybrid, and always on. It offers a scalable, identity-first approach to security, especially for distributed workforces. It is especially effective for organizations with distributed workforces or those adopting Zero Trust architectures, where centralized control and scalability are key.
For example, a global marketing team using multiple SaaS platforms can rely on cloud-based MFA to ensure secure, seamless access, whether they’re logging in from Austin, Amsterdam, or anywhere in between.
|
Pros
– Easy to deploy and scale across remote and hybrid environments
– Centralized management through identity providers and SSO platforms – Frequent updates and improvements without on-premises maintenance |
Cons
– Dependent on internet connectivity and third-party service availability
– May introduce latency or downtime if the cloud provider experiences issues – Potential compliance concerns for industries with strict data residency requirements |
|---|
Now that we’ve covered the different types of MFA, let’s clear up a common point of confusion: how does 2FA actually differ from MFA?
MFA vs. 2FA: Understanding the difference
MFA and 2FA are often used interchangeably, but they’re not the same thing.
2FA is considered a subset of MFA. It requires exactly two types of credentials—typically something you know (like a password) and something you have (like a one-time code or mobile device). It’s a significant step up from password-only security and is widely used for email, banking, and SaaS logins.
MFA, on the other hand, is more flexible. It can include two or more factors from different categories, such as biometrics (something you are) or behavioral signals (something you do). This layered approach is especially valuable for high-risk environments or users with elevated privileges.
| Features | 2FA | MFA |
|---|---|---|
| Number of factors | Exactly 2 | 2 or more |
| Flexibility | Limited | High |
| Security | Moderate | Stronger |
| Common use cases | Email, VPN, SaaS apps | Finance, healthcare, Zero Trust environments |
| Examples | Password + SMS code | Password + token + fingerprint |
2FA is a solid starting point—but MFA is where real security maturity begins. As cyberattacks evolve and compliance requirements become more stringent, organizations are transitioning beyond basic two-factor authentication setups toward more adaptive, risk-aware strategies.
However, not all MFAs are created equal. The right mix depends on your risk profile, user base, and what you’re trying to protect. This means that modern organizations are moving towards incorporating additional layers of biometrics, device health, location awareness, and even behavioral signals to make smarter, context-aware access decisions.
Ready to modernize your endpoint management?
Discover Tanium AEM
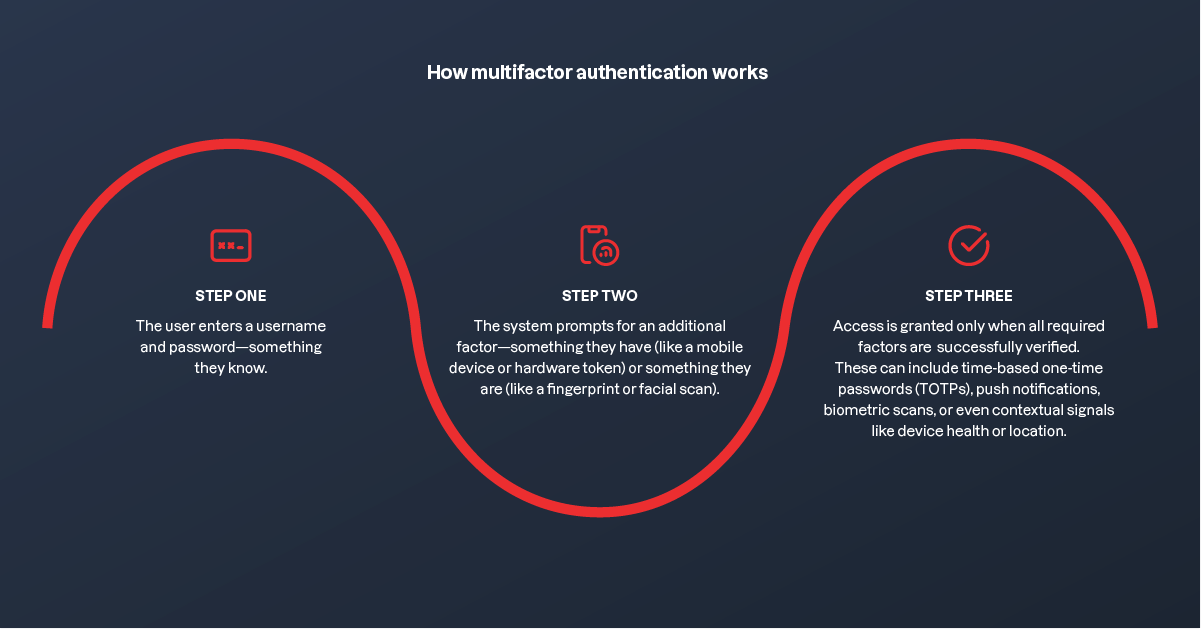
How multifactor authentication works
MFA is about making identity verification smarter—and harder to fake. Instead of relying on a single password (which can be guessed, stolen, or phished), MFA requires users to present multiple forms of proof before they’re granted access.
Here’s how MFA typically works:
- Step one: Enter your username and password—something only you know.
- Step two: Confirm your identity with something you have (like your phone) or something you are (like a fingerprint).
- Step three: You’re in—once all factors check out, including one-time codes, biometrics, or even device health and location.
 This layered approach drastically reduces the likelihood of unauthorized access, even if one factor is compromised. A stolen password alone won’t get hackers very far if they also need your phone, fingerprint, or physical location.
This layered approach drastically reduces the likelihood of unauthorized access, even if one factor is compromised. A stolen password alone won’t get hackers very far if they also need your phone, fingerprint, or physical location.
And as MFA evolves, it’s not just about adding more steps—it’s about adding smarter ones. Modern implementations can adapt in real time, adjusting the level of authentication required based on risk signals like login behavior, device posture, or geographic anomalies.
The factors of multifactor authentication
MFA works by requiring users to present two or more types of evidence (factors) from different categories before granting access to ensure the security of online accounts and protect the user’s identity. These factors fall into five main groups:
- Knowledge factors (something you know) are credentials that the user memorizes.
- Passwords: The most common form, but also the most vulnerable to phishing and reuse attacks
- PINs: Often used on mobile devices or smart cards; shorter than passwords, but still susceptible to guessing
- Security questions: Less secure due to answers that can often be found on social media or through social engineering
- Possession factors (something you have) require the user to physically possess a device or object.
- Mobile phones: Used for receiving SMS codes or push notifications via authenticator apps or text messages
- Hardware tokens: Generate time-based one-time passwords (TOTP), often used in financial services
- USB keys/smart cards: Physical devices that must be inserted or tapped to authenticate; highly secure and common in government or regulated industries
- Inherent factors (something you are) rely on biometric characteristics unique to the user.
- Fingerprints: Common on smartphones and laptops; fast and user-friendly
- Facial recognition: Increasingly used in mobile and enterprise devices
- Iris or retina scans/voice recognition: High-accuracy options used in secure facilities or call centers
- Location-based factors (where you are) assess the user’s physical or network location.
- IP address: Helps detect logins from unusual or risky locations
- GPS location: Used in mobile-based MFA to verify geographic presence
- Network ID: Confirms access from a trusted corporate network
- Behavioral factors (something you do) analyze patterns in how users interact with devices.
- Typing patterns: Measures rhythm and speed of keystrokes
- Mouse movements: Tracks how users navigate interfaces
- Navigation habits: Looks at typical login times or app usage
Tanium’s take: MFA is only as strong as the devices it runs on. That’s why we focus on the endpoint—validating posture, detecting drift, and giving identity platforms the real-time context they need to make smarter access decisions.
Why multifactor authentication is essential for cybersecurity
MFA isn’t just a security upgrade—it’s a frontline defense against today’s most common and costly cyber threats. By requiring more than just a password, MFA makes it exponentially harder for attackers to gain unauthorized access, even when credentials are compromised.
Defending against credential theft
Stolen credentials remain one of the top causes of data breaches. Phishing, brute-force attacks, and credential stuffing are all designed to exploit weak or reused passwords. MFA breaks that chain. Even if an attacker obtains your password, they still require a second (or third) factor—such as a fingerprint, a device, or a location match—to gain access. That extra step often stops an attack in its tracks.
Meeting compliance requirements
Regulations like HIPAA, PCI DSS, and NIST not only recommend MFA—they require it. MFA is a baseline requirement for safeguarding regulated information and demonstrating that access controls are in place in industries such as healthcare, finance, and government. It’s not just about checking a box—it’s about building trust with regulators, customers, and partners.
Enhancing usability without sacrificing security
MFA doesn’t have to mean friction. With modern options like push notifications, biometrics, and device-based authentication, organizations can implement MFA in ways that feel seamless to users. Whether it’s employees, contractors, or customers, MFA can unify access policies across the board without slowing anyone down.
Did you know? According to Microsoft, MFA can block over 99.9% of account compromise attacks involving
stolen credentials.
Challenges and considerations for MFA adoption
While MFA significantly strengthens security, its implementation isn’t always straightforward. Organizations must navigate technical, financial, and human factors to ensure a smooth rollout and long-term success.
Here’s a breakdown of the most common challenges and what they mean in practice:
Cost and complexity
Deploying MFA often requires upfront investment in tools, licenses, and infrastructure, especially for large or hybrid organizations.
- May require purchasing hardware tokens, SMS gateways, or mobile device management tools
- Licensing costs can scale quickly across departments or regions
- IT teams may need to configure MFA across multiple platforms and identity providers
Integration with legacy systems
Older systems may not support modern MFA protocols, making integration difficult or inconsistent.
- Legacy apps may require custom development or third-party plugins
- Inconsistent MFA enforcement can create security gaps
- May delay rollout timelines or require parallel authentication systems
User resistance
Some users may view MFA as inconvenient or unnecessary, especially if they’re unfamiliar with the technology.
- Adding login steps can frustrate users if not clearly explained
- Resistance may lead to risky workarounds or support tickets
- Requires training and communication to build trust and adoption
Lost devices or access
When users lose access to their second factor, like a phone or token, it can disrupt productivity and access to critical systems.
- Users may be locked out of essential tools or data
- Help desk teams need clear workflows for recovery or re-enrollment
- Backup methods (e.g., recovery codes or alternate contacts) must be secure and accessible
Cyberattacks
MFA is strong but not foolproof, especially when users are unaware of how attackers might bypass it.
- Phishing attacks can still trick users into revealing secondary credentials
- Prompt fatigue (e.g., repeated push notifications) can lead to accidental approvals
- Users may not recognize suspicious behavior if adaptive MFA is poorly explained
What many MFA guides miss: Most advice stops at setup. But real-world security lives in the messy middle—when users lose devices, policies drift, or attackers get creative.
Passwordless MFA: The future of authentication
Passwords have always been the weakest link in the security chain—easy to forget, easy to steal, and often reused across systems. Passwordless MFA eliminates the knowledge factor, relying instead on possession and inherence factors for authentication. Instead of relying on something you know, it verifies identity using something you have or are—no password required.
This approach combines the strength of multifactor authentication with the simplicity users crave. Think biometric scans, device-based authentication, or FIDO2 security keys that unlock access with a tap or glance. The result? Faster logins, fewer help desk tickets, and dramatically reduced risk of credential-based attacks.
Passwordless MFA is particularly effective in high-compliance or high-risk environments where password hygiene alone is insufficient. It also supports Zero Trust principles by continuously validating identity without relying on static credentials.
Passwordless MFA benefits include:
- Eliminates the risk of password reuse and phishing
- Reduces IT overhead from password resets and lockouts
- Delivers a smoother, more intuitive user experience
Bottom line: Passwordless MFA is gaining traction as a promising evolution in secure, user-friendly access, but its adoption depends on organizational needs, infrastructure, and risk posture.
How Tanium supports effective access management with real-time device visibility
Tanium empowers organizations to make smarter secure access decisions by turning real-time device visibility into actionable insights through integrations with third-party solutions like identity platforms to inform and enforce conditional access policies.
For example, Tanium enables the continuous assessment of device compliance and risk posture, allowing organizations to gain real-time data about a device’s state, including encryption status, firewall settings, and security policies.
Identity platforms like Microsoft Entra ID can use this real-time device telemetry to understand compliance status, vulnerability exposure, and whether a device is allowed on the network, helping organizations enforce conditional access policies more effectively and applied consistently across the environment to enforce Zero Trust at scale.
Tanium brings real-time endpoint context into the equation, helping ensure that access decisions are based on the actual state of the device, not just the user.
This is critical for Zero Trust.
Additionally, Tanium’s on-premises operating system, TanOS, supports MFA enforcement for SSH access to Tanium infrastructure, helping secure administrative access to critical systems. Administrators can configure MFA requirements, such as TOTP, to ensure that only verified users can access critical Tanium systems.
This configuration strengthens protection for mission-critical infrastructure by reducing the risk of unauthorized access. MFA enforcement can be tailored to organizational policies, and administrators can specify preferred authentication methods directly within the TanOS console.
Want to see how MFA fits into a broader Zero Trust strategy? Watch how Tanium and Microsoft Entra ID work together to deliver real-time, risk-informed access decisions—without slowing users down.
Frequently asked questions about MFA
What are the 3 credentials used in multifactor authentication?
- Something you know (like a password)
- Something you have (like a passcode or software token)
- Something you are (biometric)
These three categories are defined by standards bodies like NIST (SP 800-63B) and are widely adopted across the cybersecurity industry.
However, some frameworks also recognize a fourth category that incorporate contextual signals, such as location, device, or behavior. These are used in adaptive or risk-based authentication to assess whether a login attempt is suspicious and may trigger additional verification steps. For example, Microsoft and other identity providers use IP-based geolocation to flag logins from unusual regions and prompt step-up authentication.
To note: These signals enhance the layers of security but are not considered standalone authentication factors under NIST or CISA guidelines.
What is the strongest form of multifactor authentication?
Some of the most secure MFA implementations combine biometrics or hardware tokens with adaptive, risk-based authentication, especially in high-compliance or high-risk environments. However, the “strongest” setup depends on your threat model and infrastructure.
What are examples of multifactor authentication?
Using a password and a fingerprint, or a password and a one-time code from an authenticator app or SMS.
To note: App-based or hardware-based codes are generally more secure than SMS.
Is MFA really more secure?
Yes. MFA significantly lowers the risk of unauthorized access by introducing multiple verification layers. CISA notes it can make you “99% less likely to be hacked.”
Should you always have MFA enabled?
In most cases, yes. Every organization should use MFA to strengthen cybersecurity, protect sensitive information, and reduce the risk of credential-based attacks. However, implementation should consider user experience, system compatibility, and risk level.
Related resources
- Is multifactor authentication living up to its hype?
- Tanium experts bust common password myths
- What is data loss prevention? And why you need it
- Achieve Zero Trust at scale With Tanium and Microsoft Entra ID
- Tanium integration use cases
Tanium Autonomous Endpoint Management (AEM) empowers IT and security teams to act with precision and speed—automating changes, surfacing real-time recommendations, and confidently executing updates at scale. Whether you’re managing patching, compliance, or incident response, AEM brings together visibility and action in one unified platform.
MFA is just the start. With Tanium, you don’t just enforce policy—you enforce trust. See how our platform turns visibility into action and action into resilience by requesting a live, personalized demo today.




