The challenge of knowing every asset
Point solutions provide incomplete inventory and limited, stale data.
0
of IT decision-makers discover unidentified endpoints weekly
0
of software licenses go unused by employees
0
of organizations have experienced breaches through unknown assets
Complete asset management
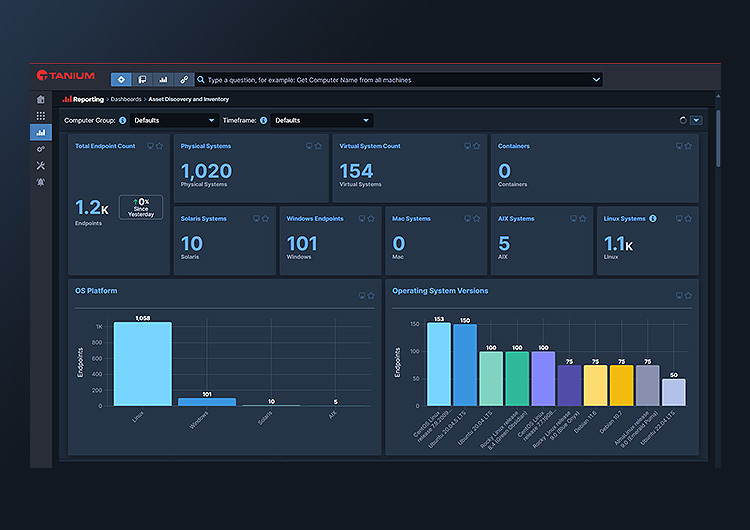
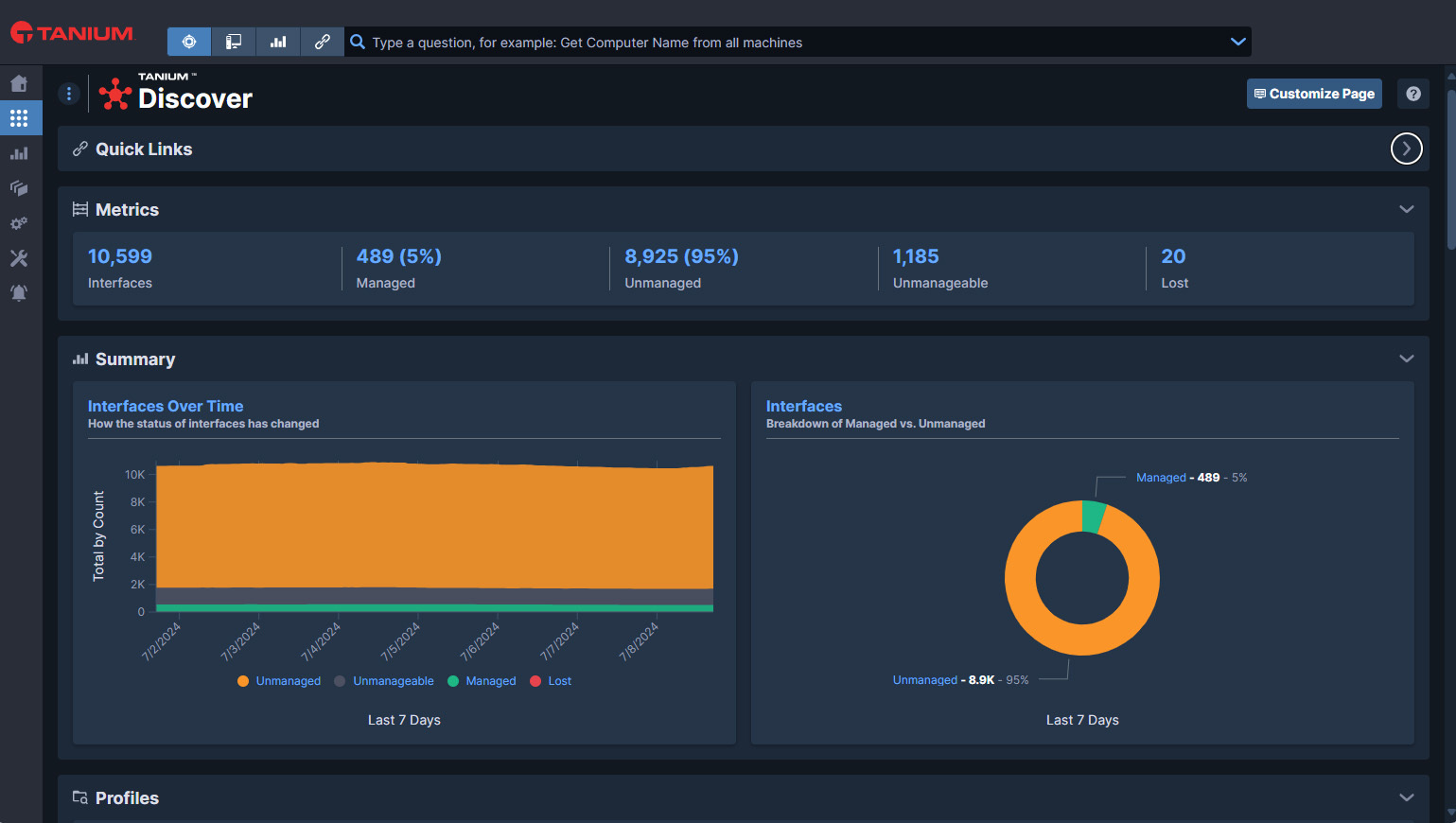
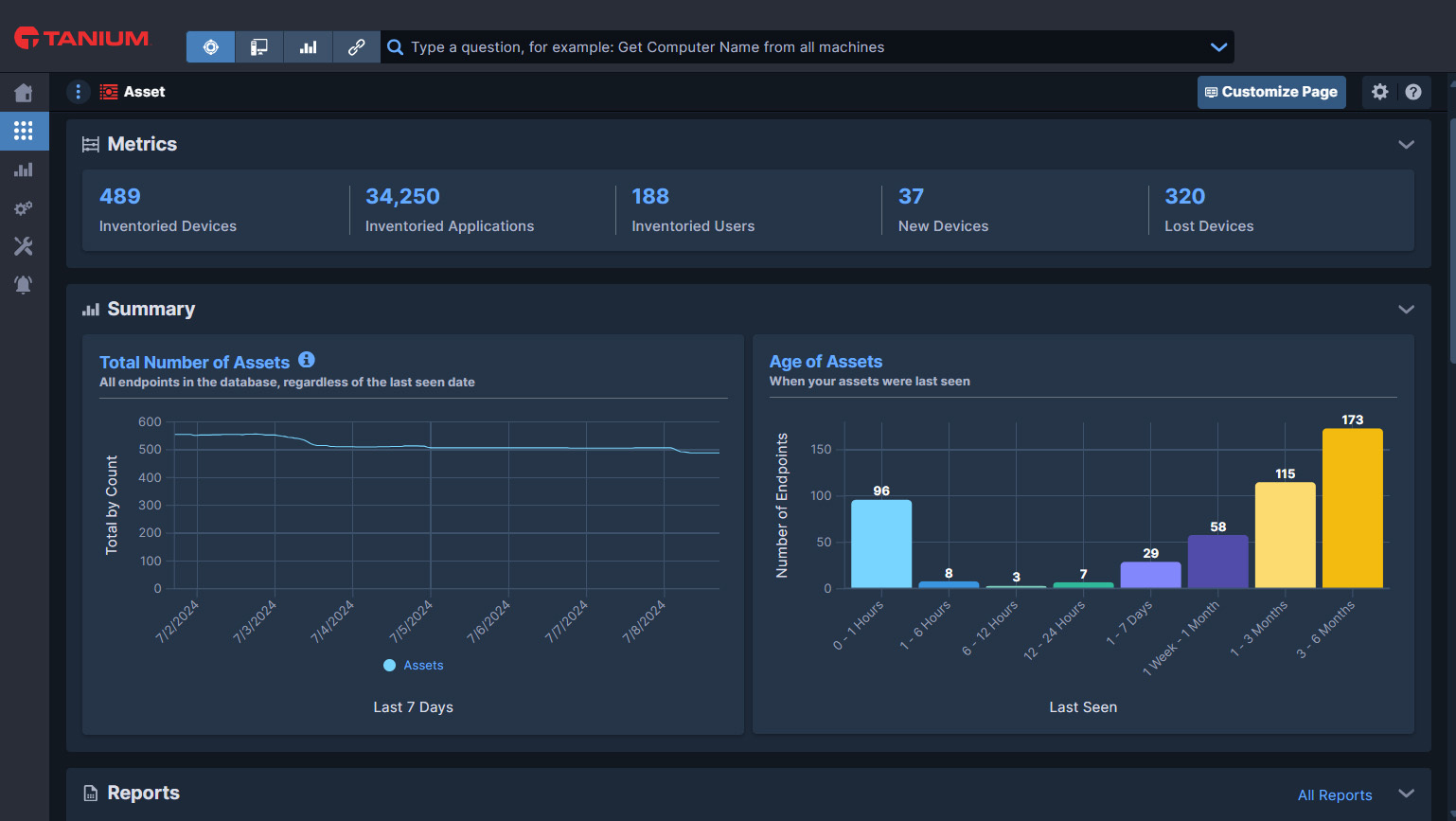
Tanium Core includes Asset Discovery and Inventory, which provides accurate visibility and high-fidelity data that reduces costs and risks as well as improves workflow efficiency.
Gain visibility to all unmanaged endpoints
Discover every endpoint in your environment, building comprehensive inventory using real-time data.
Avoid unnecessary hardware and software costs
Report on asset and license usage statistics for each installed app to optimize your estate, reduce risks, and decrease costs.
Equip third-party systems with accurate, high-fidelity data
Leverage Tanium to provide accurate, real-time data to other tools (e.g., CMDB, SIEM) and unify teams with a centralized single source of truth.
Analyze endpoint data when planning the migration to cloud
Gain full visibility to provide the best analysis for cloud migration and manage both on-prem and cloud assets with Tanium.
Simplify merger and acquisition processes
Quickly ID software license data and find unmanaged endpoints to make decisions, meet compliance, and bring acquired endpoints under management.