Layered Security Methods Keep Threats at Bay
Adding intelligent layers of security can complement your IT hygiene practices and prevent increasingly common cyberattacks
With every business now a potential target, preventing cyberattacks may be your company’s new top security goal. And as the old saying goes, “An ounce of prevention is worth a pound of cure.” Viewed through the lens of cybersecurity, this adage holds so true that we’ve given it a name: cyber hygiene.
You’ll hear this term spoken often, referring to the healthy routines you should practice to greatly reduce the risk of becoming a target for malware or ransomware attacks. In May of this year, even the president released an Executive Order encouraging the private sector to focus on security best practices.
Effective cyber hygiene requires constant vigilance and upkeep. Fortunately, this ongoing work becomes far less onerous if your people, processes and toolkits lean into these basic principles. Tanium has recently partnered with Deep Instinct to help you efficiently and effectively protect and prevent threats at the endpoint before they cause harm.
Locking your doors and windows
The easiest way to remove the target from your back is to not give attackers an easy way into your estate, also known as “locking your doors and windows.” This concept refers to good hygiene practices such as knowing with certainty all of the endpoints that exist in your environment, keeping your endpoints properly configured, training your staff about security concerns like phishing and misuse of credentials, and rigorously patching and updating your software to remove the vulnerabilities most hackers are seeking.
But we can do more to secure those digital doors and windows, which is why we have partnered with Deep Instinct to leverage its Endpoint Security prevention platform in key areas of the framework that we use to secure your endpoints.
Adding sentries to guard the estate
To illustrate how Tanium works with Deep Instinct to protect and defend your estate, it’s useful to think about it in terms of a security lifecycle. This lifecycle steps through five phases.
Your organization can lock every door and window and then additionally add sentries to stand guard at every portal — Deep Instinct’s lightweight agent protects the endpoint by continuously scanning for threats. If a threat is detected, it prevents the threat from executing before it can do damage. Finally, Deep Instinct responds by sending notification telemetry to the Tanium Threat Response console, providing details on the malware that can be used to look for similar threats over the rest of the estate.
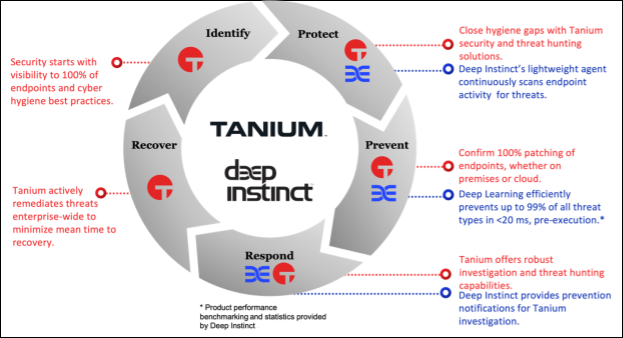
Tanium and Deep Instinct work together to protect your IT estate and prevent and respond to threats.
Let’s take a look at an example scenario to understand the security gained by enhancing your Tanium platform with Deep Instinct:
- Knowing that if you can’t see it, you can’t protect it, your IT team uses Tanium’s Asset Discovery and Inventory tools to identify and inventory all of your endpoints.
- Your security team trains your employees on security awareness and policies to help adhere to cyber hygiene practices. To efficiently and effectively protect your network and endpoints, the team leverages Tanium’s Security and Risk & Compliance solution along with Deep Instinct’s Endpoint Security software.
- Let’s say a hacker targets your business by sending an email that contains a weaponized PDF document or a link that sends users to a web form on an internet-facing web server. When the user hits submit on the form, code executes that reaches out to a command and control server to download additional malicious files.
- Deep Instinct’s lightweight agent on the endpoint uses Deep Learning AI predictive intelligence to detect these types of malware prior to being written to disk and thereby prevents the code from executing. Deep Instinct then sends an alert and telemetry data to your Security team that provides details on the malware.
- The information appears in the Tanium Threat Response console. Your security team can use this information to search for similar file hash values across the entire estate, ensuring this particular malware has not appeared elsewhere.
- On the rare occasion that an attack campaign does manage to successfully begin its attack lifecycle, you can use Tanium to immediately quarantine the endpoint, or group of endpoints, preventing the attack from moving laterally. You can then use any number of Tanium tools to remediate the attack — removing files, installing patches or other actions, all done at any scale required.
Learning more about Deep Instinct
Deep Instinct co-exists on endpoints to offer functionality that goes far beyond the traditional or next-gen antivirus software to prevent 99% of known and unknown threats before they cause harm.
Leveraging Deep Learning artificial intelligence, Deep Instinct agents continuously expand their detection capabilities by making new connections and predicting new attack types over time. Deep Instinct can detect an incredibly wide variety of malicious attacks — zero-day, ransomware, file-based, fileless, supply chain — in as little as 20 milliseconds, 750 times faster than it typically takes an attack to encrypt and infect an endpoint.
Moreover, Deep Instinct benchmarking shows a 99%+ detection and blocking rate (far higher than other endpoint protection platforms) and a 0.1% false-positive rate, which means your security team spends far less time investigating to separate the signal from the noise or tuning the software to reduce false positives.
Adding a measure of peace
At the end of the day, no cyber hygiene solution is 100% foolproof, but with Tanium and Deep Instinct, you have stronger protection on your endpoints, clear visibility across your estate, and a single source of truth from which to examine prevented threats and respond immediately at scale.
To learn more about our partnership and request your own personalized demo, visit the Deep Instinct partner page.




